
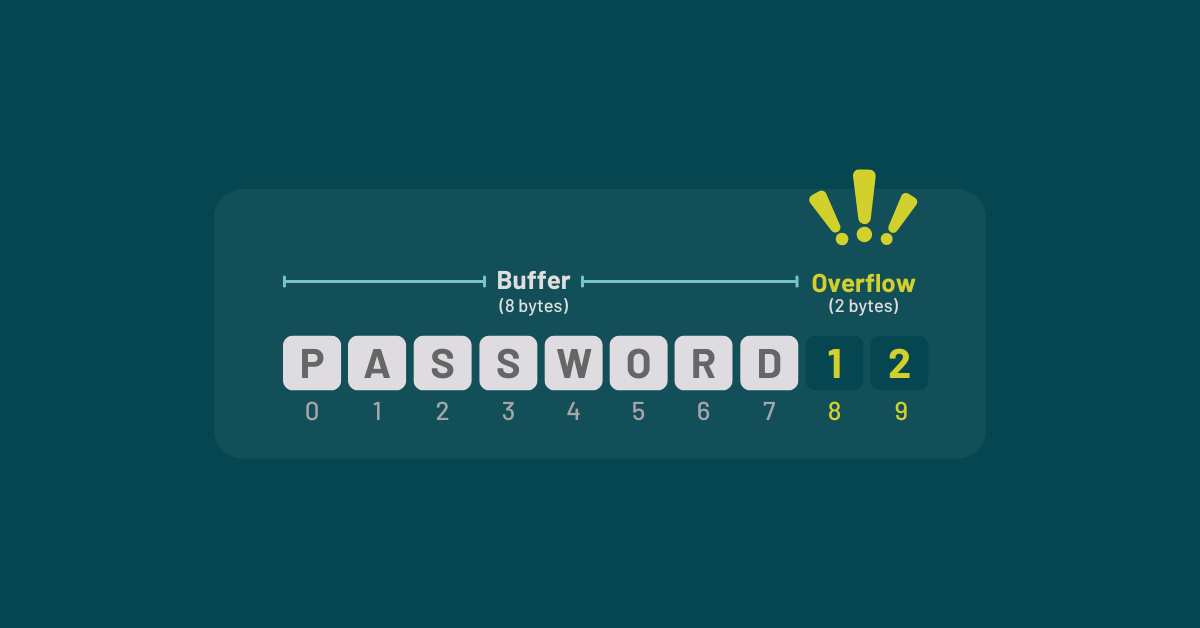
A buffer overflow attack is a common vulnerability in software security. It happens when a program writes more data into a memory buffer than it can hold, causing data corruption, crashes, or even remote code execution.
Buffer overflows have been known for decades. They still pose a serious risk, especially in C and C++ systems that rely on manual memory management. If teams don’t quickly fix buffer overflow issues, the organization could face big problems. These may include severe business impacts, from legal penalties and fines to lost trust and revenue.
This guide explains how buffer overrun attacks work, their consequences, and real-world examples. You’ll also learn how modern cybersecurity tools like Kiuwan help teams detect and prevent them before deployment.
In programming, a buffer is a block of memory set aside to hold data, such as strings, arrays, and user inputs. Buffers have fixed boundaries, but when more data is written than the buffer can hold, the excess spills into adjacent memory. This is called a buffer overflow.
Here’s a C program with a buffer that holds just 10 bytes.
char buffer[10];
// Unsafe: input exceeds buffer size
strcpy(buffer, “This input is way too long!”);
Note that it uses strcpy, which is unsafe. This function copies a longer string without checking the bounds. Extra characters overwrite nearby memory, which can corrupt program behavior, cause crashes, or trigger a segmentation fault—an error that happens when a program tries to access memory it shouldn’t.
To stay safe, replace unsafe functions like strcpy with bounded alternatives such as strncpy. Keep in mind, though, that even strncpy has pitfalls—for example, it doesn’t always null-terminate strings. CERT recommends using safer functions like strlcpy or strnlen_s, or relying on memory-safe abstractions where possible.
A buffer overflow attack occurs when a threat actor sends too much input. This oversized input causes an overflow, allowing them to take control of the program.
Threat actors target buffer overflows because they can do more than crash web applications and systems. These vulnerabilities can result in major security issues, such as denial-of-service (DoS), remote code execution (RCE), and privilege escalation.
Hackers can use buffer overflows to take control of operating systems. They overwrite key memory areas like executable code and function pointers. This allows them to perform unauthorized actions.
Buffer overflow cyberattacks can have mild or severe effects. It all depends on how the attackers use them.
Crashes aren’t just a hassle for companies and their stakeholders. They can also put lives at risk, especially in high-stakes industries. For example, a buffer overflow in medical devices can cause an insulin pump to fail, which could endanger lives. Similarly, in the aerospace industry, a failure in avionics software can threaten flight safety.
Buffer overflow security vulnerabilities are among the oldest and most common software vulnerabilities. Here’s a summary of the most well-known ones.
When threat actors create input to trigger an overflow, it can lead to serious issues. These include data leaks, fines, and lawsuits. Here are the types of buffer overflow attacks and threat actor exploitation techniques to be aware of.
Types of buffer overflows include:
Stack-based buffer overflows are the most common form of overflow vulnerability. They happen when a program writes more data to a buffer on the stack than what the buffer allows. This often corrupts nearby data on the stack. As a result, the program might crash or run incorrectly. Such flaws are frequently introduced by unsafe functions like strcpy when the destination buffer is too small for the source input. A crash usually happens, but if an attacker controls the input, they can change the return address. This lets them send execution to harmful code and take over the program.
Heap-based buffer overflows happen when a buffer in the heap memory is overwritten, usually due to a lack of bounds checking. They can lead to software vulnerabilities and crashes because threat actors modify the program’s memory space beyond its intended boundaries. Compared to stack-based overflows, heap overflows are more complex to exploit. Organizations can prevent these vulnerabilities by implementing proper bounds checking and memory management.
Off-by-one buffer overflows happen when a program writes one byte past a buffer’s limit. This usually occurs due to miscalculating the needed space. For instance, a programmer might forget to include a terminating character like “\0” in C strings. This single-byte overrun can change a nearby byte. This corrupts important control data and lets attackers redirect execution. Organizations can stop off-by-one overflows by:
Attackers look for buffer overflows. Once they find one, they exploit the memory issue to run their code. Common exploitation techniques include:
Attackers change the return address. This is the memory spot where the program continues after a function call. They replace it with an address they choose. They can then inject malicious code using the methods below.
After taking over an address by changing the return address, attackers inject shellcode. This malicious code opens a command shell on the target system, allowing the attacker to gain control and carry out harmful actions.
These are sequences of NOP instructions put at the beginning of code sections. Their goal is to “slide” the CPU’s instruction execution flow to whatever the attacker wants.
A threat actor injects harmful data into the memory heap. This makes the execution flow jump to the sprayed memory instead of the original code. The heap memory stores all the variables created at runtime.
ROP is a clever attack method that lets hackers run code even if strong security measures are in place, like code signing and executable space protection. Attackers attach small pieces of attack code to the stack. Then, they overwrite the return address with this new location.
These exploitation techniques continue to evolve in tandem with defensive measures. Even with protections like stack canaries, ASLR, and DEP, attackers still find clever ways to get around them. Accordingly, organizations must invest in static and dynamic defense.
Buffer overflows can be a serious threat in industries that rely on legacy systems and low-level code. These include:
C and C++ are especially prone to buffer overflow attacks. They use manual memory management, so there’s no automatic bounds checking. Developers have complete control over performance. However, threat actors can easily introduce memory errors without being noticed.
Modern memory-safe languages, like Python, Java, Go, and Rust, automatically check bounds and hide direct pointer manipulation. As such, they are much less likely to be vulnerable to buffer overflow attacks. However, they can still be affected by bugs, for example, in the Java Virtual Machine.
You can prevent buffer overflows by adopting secure coding practices such as:
Preventing buffer overflows is tough. This is particularly true when watching for other software vulnerabilities and having a large attack surface. That’s where Kiuwan Code Security (SAST) comes in.
As a cloud-based application security platform, Kiuwan helps you find and fix buffer overflow risks. Here’s how:
You can detect and prevent buffer overflow vulnerabilities before they reach production. Kiuwan SAST scans C and C++ code for unsafe memory operations, flags violations against CWE standards like CWE-120, CWE-121, and CWE-122, and integrates seamlessly into your CI/CD pipeline.
Start your free trial today to see how Kiuwan helps your team eliminate critical memory risks and maintain compliance with industry standards.
Buffer overflows remain common because C and C++ are still widely used in systems programming and embedded devices, and many legacy applications lack modern security protections.
Buffer overflows aren’t directly relevant in memory-safe languages like Rust, Go, and Swift. That’s because they’re designed to prevent buffer overflows by enforcing strict memory safety rules.
However, using unsafe external libraries can reintroduce buffer overflows. For example, suppose a developer uses unsafe blocks when they need low-level control, and the compiler suspends some safety checks inside these blocks. In that case, buffer overflows can creep back in if the developer isn’t careful. Additionally, if a programmer links to a C library or uses Foreign Function Interface (FFI), the app will be exposed to the same risks as C, even if the developer is working in Rust.
Several compliance standards address buffer overflows. These include:
DevSecOps teams can address buffer overflows by:


