

The world of software development is constantly evolving, and legacy languages such as COBOL, Fortran, Perl, and C are becoming increasingly outmoded. Legacy languages are those that have been around for many years and are no longer actively developed. Although these languages still offer some advantages, such as their relative simplicity, they are quickly becoming obsolete in favor of more modern programming languages.
While legacy languages are now rarely used, some organizations still rely on them to power their applications. Legacy languages are often used in legacy programs and systems, which can be difficult and expensive to replace.
Developers with skills in legacy languages are also highly sought-after, as legacy systems can pose significant software and data security risks. However, developers with the skills to maintain legacy languages are retiring or leaving the job market at a higher rate than new legacy language developers are entering it.
Moreover, new developers are rarely trained in legacy languages, so these languages are largely out of favor with the younger generation. This has left many companies in a precarious situation, as legacy system maintenance is often necessary to ensure their long-term security.
In this article, we’ll look at some examples of legacy languages, what applications still rely on these legacy languages, and why new DevSecOp organizations must cater to these languages.
Developed in 1969, C is one of the oldest and most widely used legacy languages. Dennis Ritchie created C as a system programming language, and it is still widely used in everything from operating systems to databases, web servers, and appsec. This legacy language is the basis of many languages, such as C++, Java, JavaScript, and Python.

Some features of C that make it an attractive language for appsec include its flexibility, portability, and efficiency. Additionally, C is a powerful language with low-level access to memory and hardware, meaning developers have more control over the appsec process.
Despite its age, C remains the primary language for developing embedded systems and system software. It’s also used in appsec, making it invaluable for organizations that need to secure their systems and applications.
COBOL, short for COmmon Business Oriented Language, is one of the oldest programming languages used today. It was developed in 1959 as a portable programming language for the U.S. Department of Defense to process data for its business applications.

Its features include its ability to be used on various hardware platforms and its relatively simple syntax, making it easy for developers to read and understand. It is also highly reliable and secure, making it ideal for appsec.
COBOL is still widely used for mainframe computing, with many organizations using it to develop and maintain their legacy applications. Its advantages include its simplicity, readability, and support for database access.
COBOL’s features make it well suited for legacy programs and systems, although its reliance on lengthy codes has led to many of these applications becoming outdated. However, COBOL is still widely used in business applications such as banking, finance, and accounting, as it can provide organizations with a comprehensive set of security controls.
This legacy language first appeared in 1987 and is often used for system administration tasks, web development, and appsec. Perl is a high-level programming language that combines elements of several languages, including C, shell scripting, and awk.

Due to its flexibility, Perl is often used as a glue language to join different components together. It is also used in appsec as it allows developers to quickly and easily develop secure applications.
Despite its age, Perl remains widely used in appsec due to its flexibility and ease of use. Its most common applications include system scripting, web development, and appsec. Furthermore, it is still widely utilized in legacy applications, such as banking and finance systems.
Though developers and organizations may not use legacy languages as often anymore, they still have some distinct advantages.
New DevSecOp organizations must be aware of risks associated with legacy languages and cater to them accordingly. Here are a few risks to consider:
Overall, legacy languages such as C, COBOL, and Perl remain vital parts of software security. Organizations should consider using legacy languages for their advantages, such as cost-effectiveness, while also understanding the risks and taking appropriate steps to mitigate them.
Due to the risks associated with legacy languages, DevSecOp organizations should consider the risks associated with legacy languages and ensure they use the security features provided by these languages. This will help protect their applications and systems from potential threats. Doing so will also minimize the risks associated with software breaches.
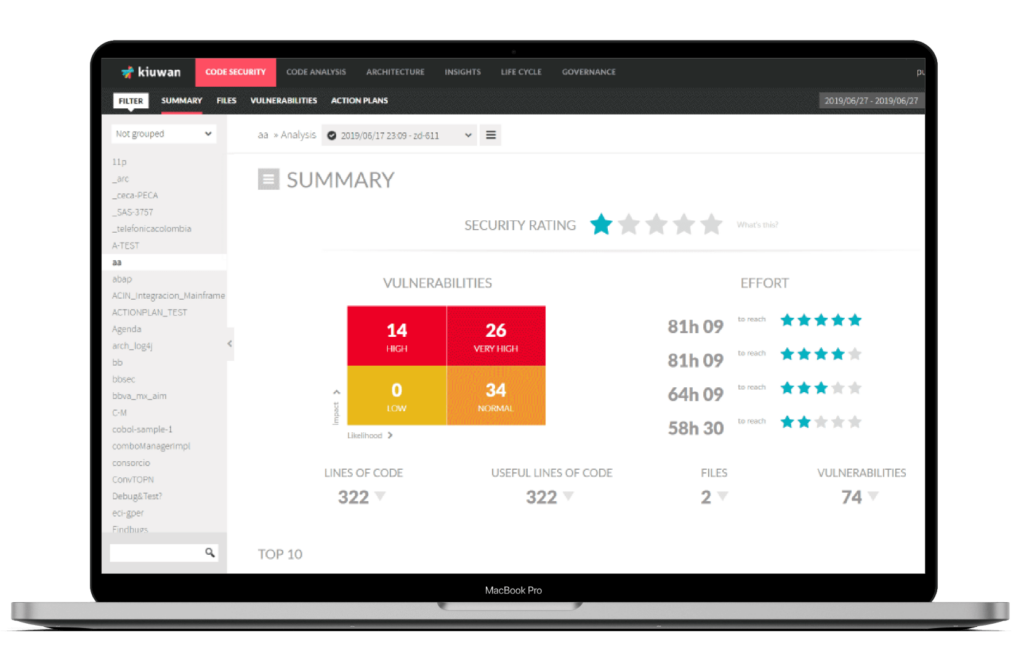
Organizations that still rely on legacy languages should heavily consider using Kiuwan’s SAST and SCA products, as these products ensure legacy applications security.
SAST will help organizations identify and fix security issues in their code, while SCA will help them to identify any vulnerable third-party components used in the application. Kiuwan also offers a wide range of other products and services to protect applications, making it the best solution for organizations looking to secure their applications that rely on legacy languages.


