

Since Russia invaded Ukraine, a new threat vector has circulated in the open-source community. This threat vector, known as protestware, involves activists injecting malicious content into open-source code libraries to express political opinions.
While most protestware only displays pro-Ukrainian or anti-war messages, some are much more dangerous. The “peacenotwar” module in the node-ipc package, for instance, was intended to wipe data stored in Belarus and Russia.
Read on to learn more about protestware and how companies can protect themselves from it.
A portmanteau of the words “protest” and “software,” protestware is an umbrella term for malicious code injected into open-source and third-party code libraries to express political messages. Most of these threat vectors express the creator’s opposition to Russia’s invasion of Ukraine, making them a creative, non-violent form of protest that could be effective in certain circumstances.
However, it can be dangerous if intended to wipe data or take another action.

Although protestware is typically associated with the Russia and Ukraine conflict of 2022, the concept of baking political messages into software has been around for at least a few years. For example, Notepad++ had a “Stand With Hong Kong” update in 2020.
Unlike malicious packages, protestware alterations are usually not made by malicious actors. Instead, they are typically made by respected members of the open-source community.
There are 4 main types of protestware:
In this type of protestware, maintainers add pro-Ukrainian messages in banners in the repo. These can look like:
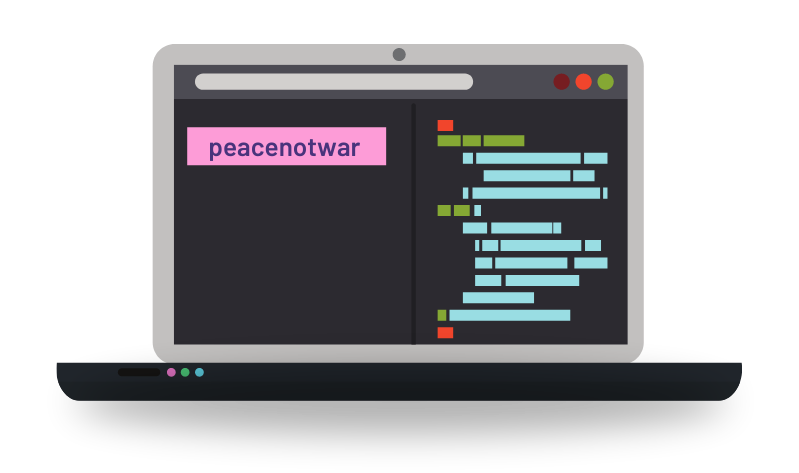
Since repo banners are harmless and only serve to express maintainers’ opinions, companies do not need to take any action when encountering them.
CLI protest logs go a step beyond repo banners. They send political messages to users through CLI logs during and after installing the open-source package.
An illustrative example involved es5-ext, a popular open-source package that had not been updated in almost two years. However, on March 7, 2022, a programmer called medikoo added a postinstall.js component, which contained code for performing time zone checks to geolocate users. If the user were located in Russia, the code would leave a CLI log containing the following:
Like repo banners, CLI protest logs are usually not malicious. There is also plenty of precedence for this type of CLI logging in the software ecosystem. Performing time zone checks are sometimes normal installation behavior, particularly when the vector needs to determine the best way and time to install the package.
In the same vein, many open-source packages log robust messages during installation. Many of these are not directly related to the package itself. For example, they may log emojis, credits, and other information.
In short, there is no need to take any action against CLI protest logs as long as the messages remain inside the installation environment.
The third type of protestware is out-of-ENV protest logs. Unlike CLI protest logs, these packages download outside of the installation environment. Most out-of-ENV protest logs are nondestructive, but they can cause undesirable disruptions in systems by running code on machines.
They may:
Event-source-polyfill, for example, geo-locates users to determine their location. If the user is in Russia, it will show a political protest message in the browser and try to redirect the browser to another website.
Finally, there are protestware packages that threaten the machines they run on.
The most well-known example happened between March 7 and March 8, 2022, when a programmer using the handle RIAEvangelist injected malicious data wiping code into node-ipc, a popular software package used to write systems software. The update executed code that geolocated users’ IP addresses whenever after downloading node-ipc. If the IP address were from Belarus or Russia, the code would wipe all of the users’ files and replace them with a heart emoji.
Accordingly, the U.S. National Institute of Standards and Technology (NIST) has listed RIAEvangelist’s malicious version of node-ipc as a vulnerability ( CVE-2022 23812).
Protestware was initially created as a non-violent protest against Russia’s aggression. However, as illustrated by node-ipc, malicious actors have started using protestware to target innocent Russian and Belarusian open-source users.
Not only are these attacks flagrantly xenophobic, but they also erode the public’s trust in open-source. A quick search on Google and popular programming hubs like GitHub reveals that an increasing number of users have realized that their applications and libraries can one day be exploited to say or do whatever a random developer wants.

Protestware may also set a dangerous precedent for using social causes to attack users and steal data. For example, the situation with node-ipc could have developed in the opposite direction, with a Russian developer geolocating and deleting files on American systems.
Companies need to start protecting themselves from protestware and other related threats. They can do this by creating and implementing the following security approaches:
Developers should only download packages that have ample documentation and are regularly maintained. Documentation and updates will reduce the chance of an activist or threat actor adding protestware code.
Besides looking at the documentation, developer teams should also Google and research each dependency before downloading it. If there are any news articles about how the dependency has been sabotaged, companies must avoid downloading that dependency.
Organizations should also use dependency scanning tools to block protestware and other code anomalies. These tools can review every line of code in new dependencies, allowing IT and developer teams to quarantine suspicious dependencies before they cause any damage.
However, while most of these tools can identify protestware, many may not offer adequate protection. Most dependency scanners can only scan changes after companies have downloaded the package. By the time the package has finished downloading, the company’s systems may already be infected.
Fortunately, some scanners, such as Kiuwan Code Security (SAST), can automatically scan code to spot and fix vulnerabilities. These leading-edge code scanners also cover all important languages and integrate directly with top-notch DevOps tools.
Picking the right dependency scanning tool to block protestware can be trying, particularly for companies new to code scanning solutions.
That is why businesses should consider getting Kiuwan Code Security (SAST). Sleek and powerful, Kiuwan Code Security automatically scans system code to identify and fix vulnerabilities and anomalies.
Specifically, it can help organizations:
What’s more, Kiuwan Code Security covers all important languages and complies with leading security standards like CWE, NIST, and OWASP. It also integrates with cutting-edge DevOps and DevSecOps tools across the software development life cycle (SDLC), giving developers the ability to create a true DevSecOps approach that bakes security into every step of an application’s design.
Interested in experiencing the Kiuwan difference? Get a free demo today. Developers will see how simple it is to start a scan, use the frictionless user interface, generate action plans, and manage code vulnerability.


