The Ultimate Code Security Tool Trusted by Developers
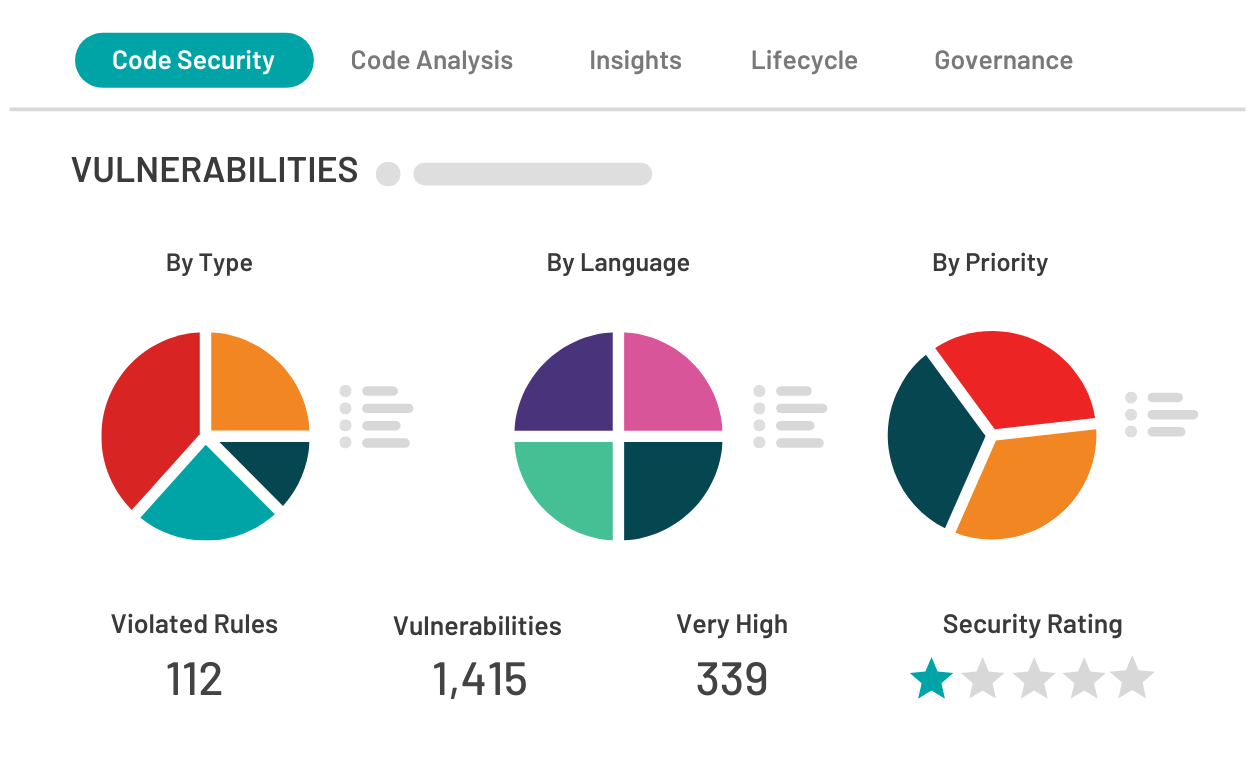
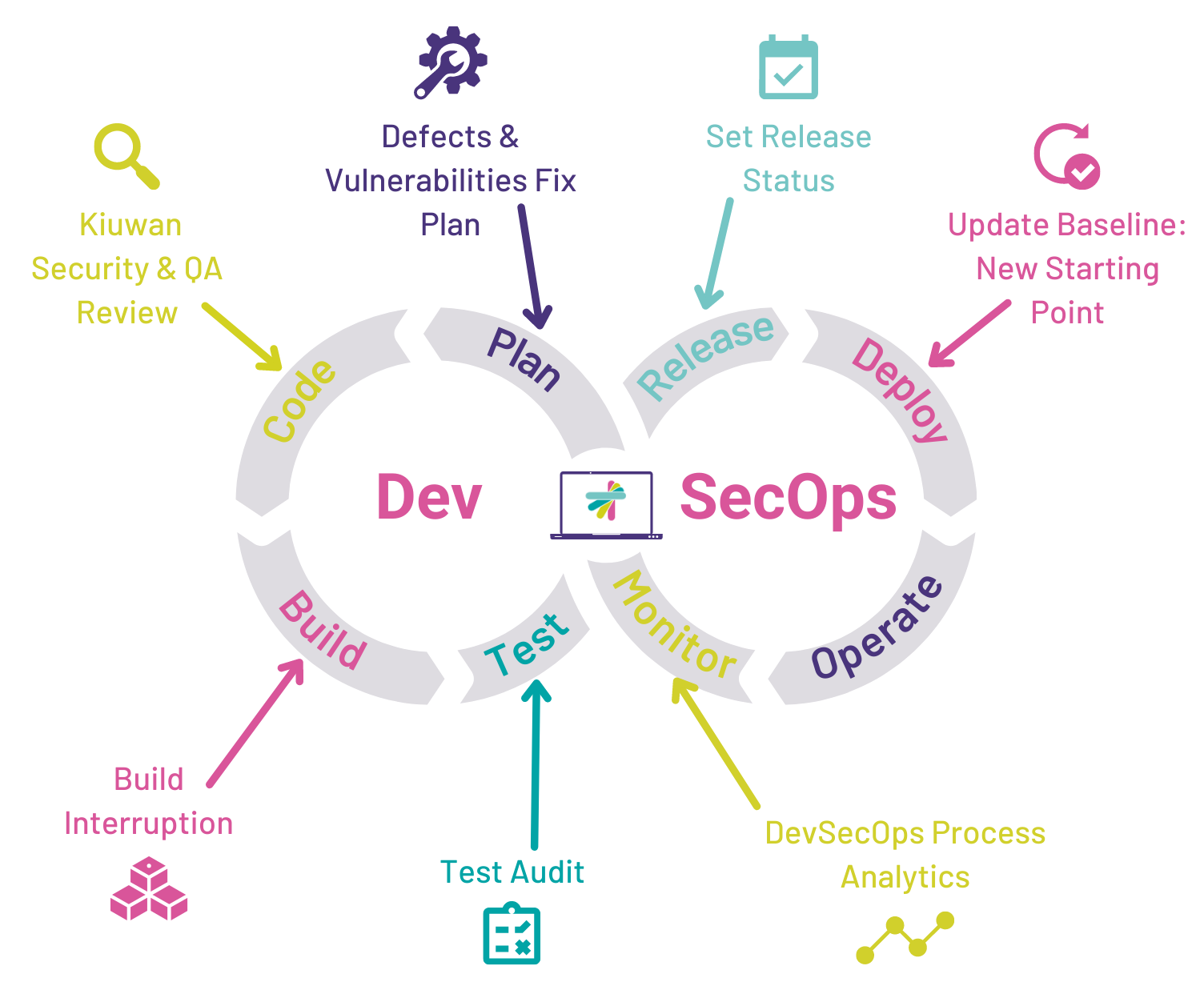
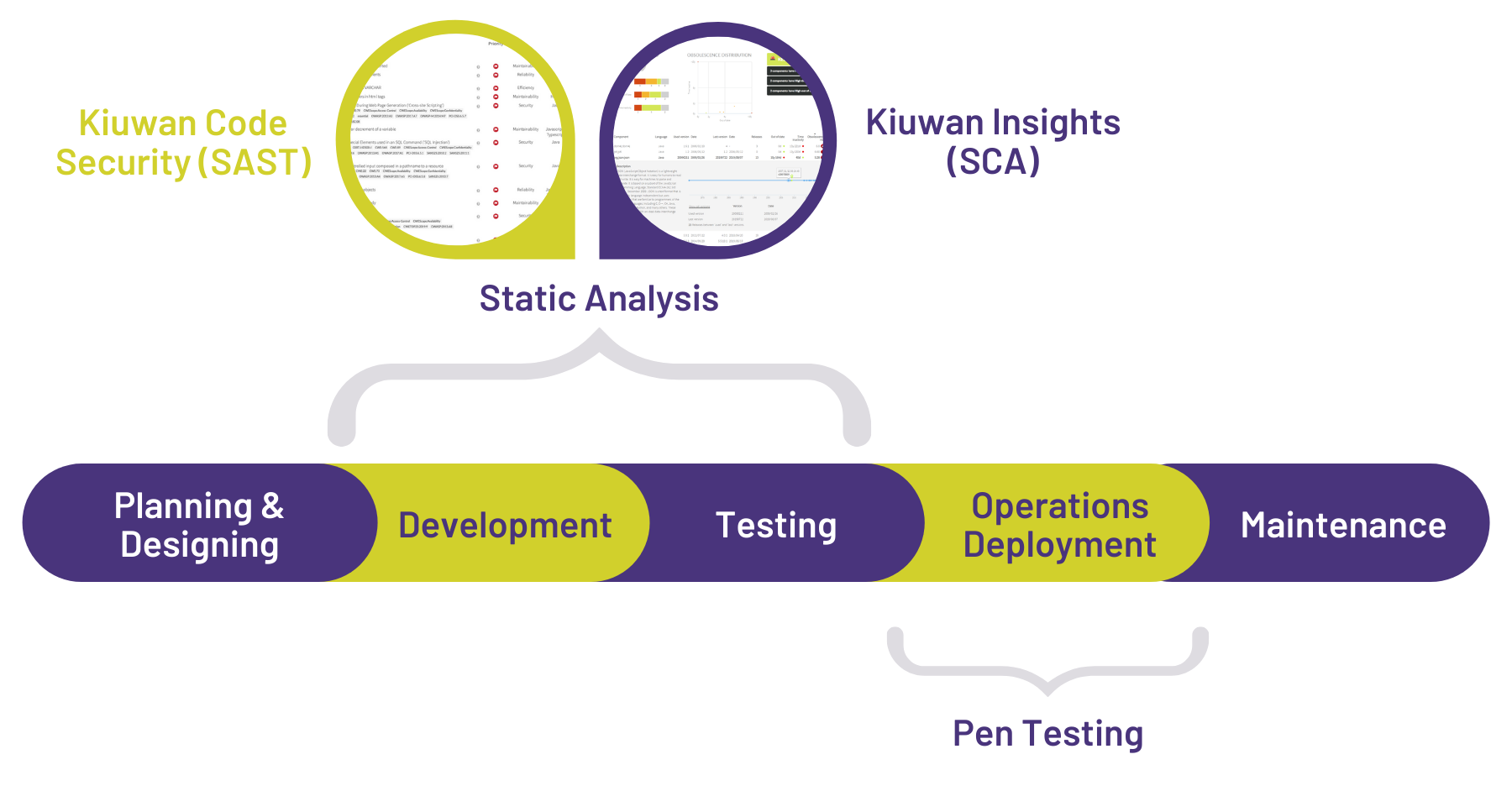
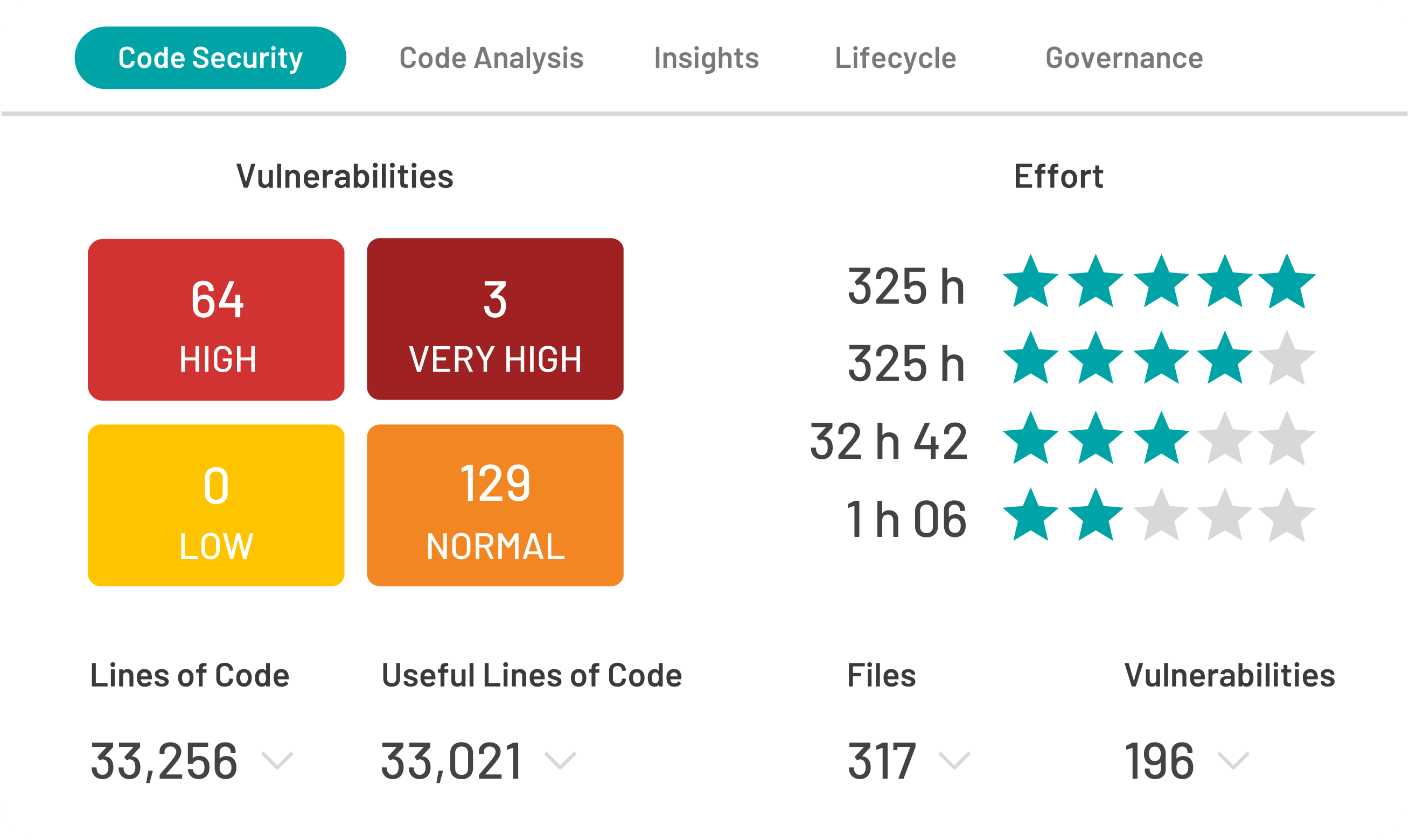
Kiuwan is a powerful, end-to-end application security platform supporting 30+ programming languages. Our comprehensive toolset will empower your team with a combination of SAST, SCA, and QA. Identify vulnerabilities in your applications and remediate them rapidly. The flexibility of both cloud-based and on-premise solutions means you get seamless integration with any development environment.