Root cause of many security breaches is trusting unvalidated input:
Source locations are those code places from where data comes in, that can be potentially controlled by the user (or the environment) and must consequently be presumably considered as tainted (it may be used to build injection attacks).
Sink locations are those code places where consumed data must not be tainted.
The goal of Tainted Flow Analysis is to detect tainted data flows: For all possible sinks, prove that tainted data will never be used where untainted data is expected. While Data Flow Analysis (DFA) is the computer technique to extract info about values at each program site, Tainting Flow Analysis (TFA) is a special case of DFA between sources/sinks for checking if non-neutralized external inputs may reach vulnerability sinks. Kiuwan implements Tainted Flow Analysis by inferring flows in the source code of your application:
|
Tainting Propagation Algorithm: for each sink detected (typically, an argument expression to a call to a sick function), follow backwards the variable value propagation in the CGF (Control Flow Graph) that could affect the sink site, until a source site that “taints” any of the candidate variables is reached.
When inferring flows from an untainted sink to a tainted source, Kiuwan is able to detect if any well-known sanitizer is used, dropping those flows and thus avoiding to raise false vulnerabilities.
Complex subsystems that accept string data that may hold commands or instructions need neutralization of inputs targeted to them.
If untrusted input entering the subsystem may result in unexpected execution of commands/actions, an injection security flaw exists. Examples of such subsystems that are candidates for injection attacks are:
Root cause of most web security flaws:
|
The first defense line against application attacks is an adequate input validation.
Good practice says: “filter on input, escape on output”. |
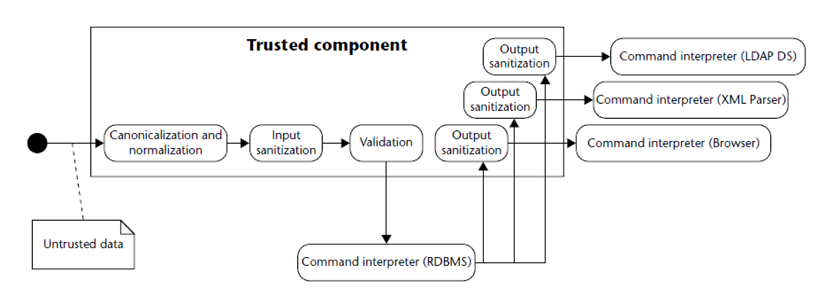
Kiuwan contains a built-in library of sanitizers for every supported programming language and framework. These sanitizers are commonly used directly by programmers or by frameworks. And Kiuwan detects their usage.
But if you are using your own sanitizers, Kiuwan could not recognize them as such, detecting false “tainted data flows”. In this case, you should let Kiuwan be aware of them.
Goal of this section is to teach you how to incorporate custom sanitizers to the Kiuwan built-in library.
During the next section, we will use the terms “sanitizers” and “neutralization routines” as synonyms.
A Neutralization Routine (or Sanitizer) is understood as any piece of code that can assure that any tainted data got as input produces untainted as output. |
This documentation is not related to how to build custom neutralization routines, but how to add your own custom neutralization routines to Kiuwan.
Basically, the process consists of:
Next, for instruction purposes, we will follow these steps using Java as the programming language. Differences with other programming languages will be further detailed.
Any custom neutralization routine must be defined in a custom neutralizations file (xml format). |
Name of the file is irrelevant but location it’s quite important.
Neutralization routines can be configured at different scopes
Depending on the location of the xml file, precedence and scope will change.
Precedence and scope of configurations is as follows:
[analysis_base_dir]/libraries/[technology]
[agent_home_dir]/conf/apps/[app_name]/libraries/[technology]
[agent_home_dir]/libraries/[technology]
Legend:
[agent_home_dir] : local installation directory of Kiuwan Local Analyzer (KLA)
As a general recommendation, we suggest to name the xml file as [technology]_custom_neutralizations.xml (this will help to clearly identify your custom files from Kiuwan own files).
Therefore, next sections will use java_custom_neutralizations.xml as the name for our custom file.
Any CNF must be an XML file with the following structure:
|
Next sections describe this structure.