What does the integration do?
If you or your organization uses Atlassian Bamboo for continuous integration of software to streamline builds for the different development projects. No worries, you can run Kiuwan analyses as part of the processes. Completely automated. This enables continuous code security. You even have the possibility to automatically enforce your security policies automatically.
In continuous integration and continuous delivery (CI/CD) environments is very common (and recommendable) to ensure the security and quality of the software under development.
Kiuwan can do that, in fact, it allows to do baseline or delivery analysis according to the user needs as a step in the build plan defined in Bamboo.
The Kiuwan analysis will be executed by a Bamboo agents. It could be a remote agent or the default agent running on the Bamboo server machine.
How does it work?
Configure your Bamboo agents
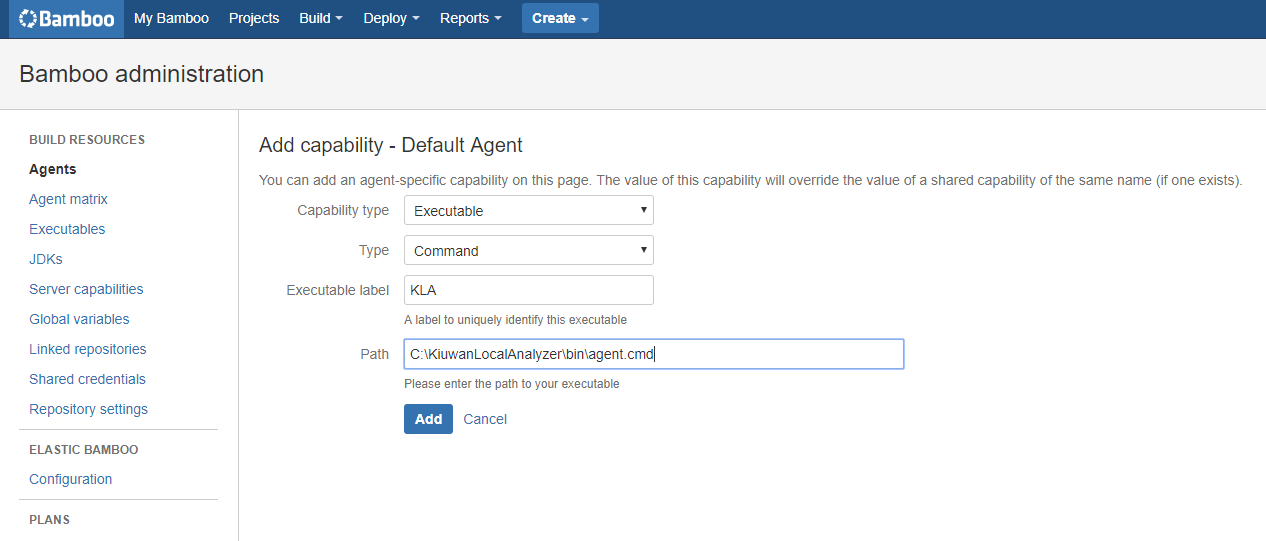
First you need to make sure that any agent that potentially can run a Kiuwan analysis as part of a build plan, has the Kiuwan Local Analyzer (KLA) installed on the same machine, and that you configure a Kiuwan agent-specific capability in the agent. For example, if you install your KLA in C:\KiuwanLocalAnalyzer, you can configure a new agent-specific capability as follows:
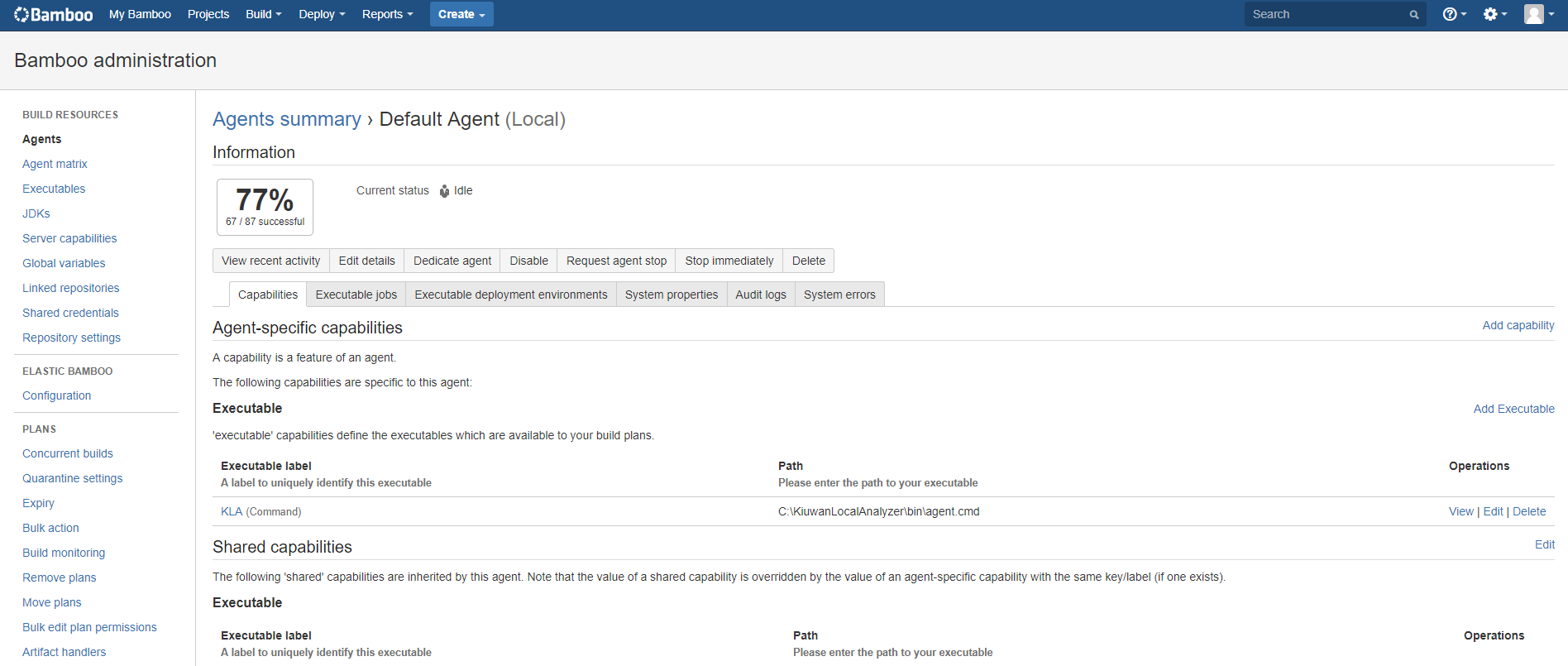
From the Bamboo agents admin page select the agent you want to configure
Click the Add capability link
Select Executable from the Capability type dropdown
Select Command from the Type dropdown
Give the new capability a unique label to identify it, KLA for example
Specify the complete absolute path to the KLA command, C:\KiuwanLocalAnalyzer\bin\agent.cmd for example
Repeat this operation for all agents that will run Kiuwan analyses. THe more agents you have with the KLA capability the more analyses you can run in parallel. This will depend on the number of applications you have under continuous development and your build/analysis strategy.
Once you have all your agents configured, you can create (or modify) build plans to run Kiuwan analyses.
Create Bamboo builds for projects to analyze
Build plans in Bamboo are created for a specific project. Create one, or select an existing one to configure it.
Configure Kiuwan credentials
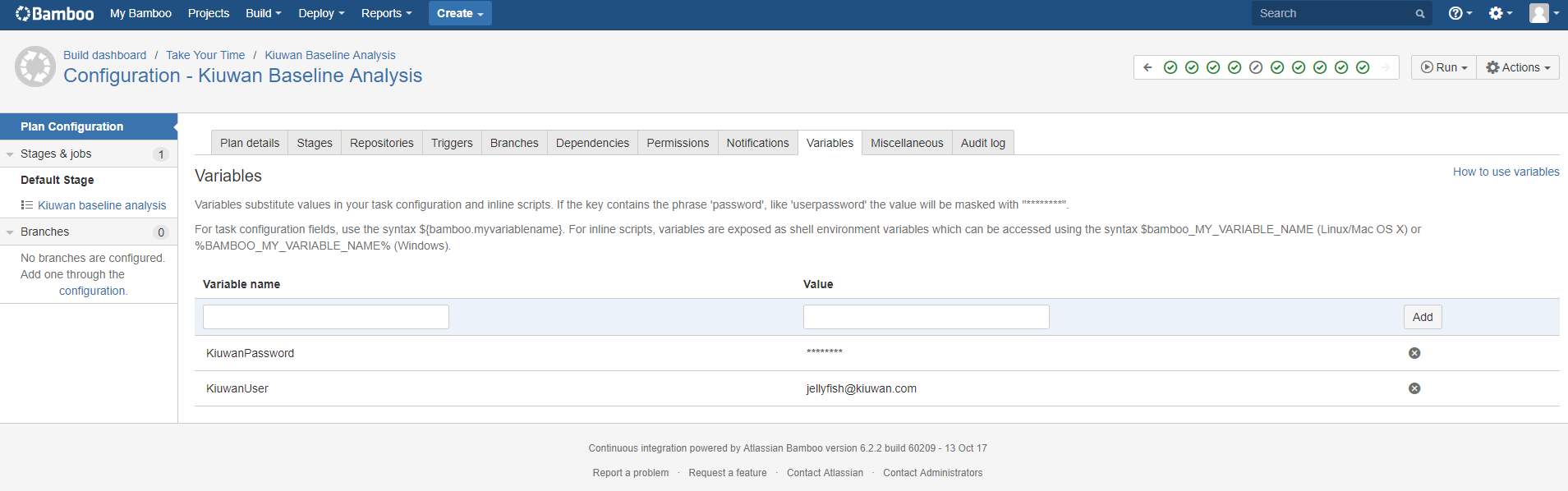
First you have to configure the Kiuwan credentials variables. Go to the variables tab and create 2 variables called KiuwanUser and Kiuwan Password, for example:
Alternatively you could create global variable for your credentials. In that case the same credentials will be used across your build plans. It is up to you what you want to do.
Create an analysis stage
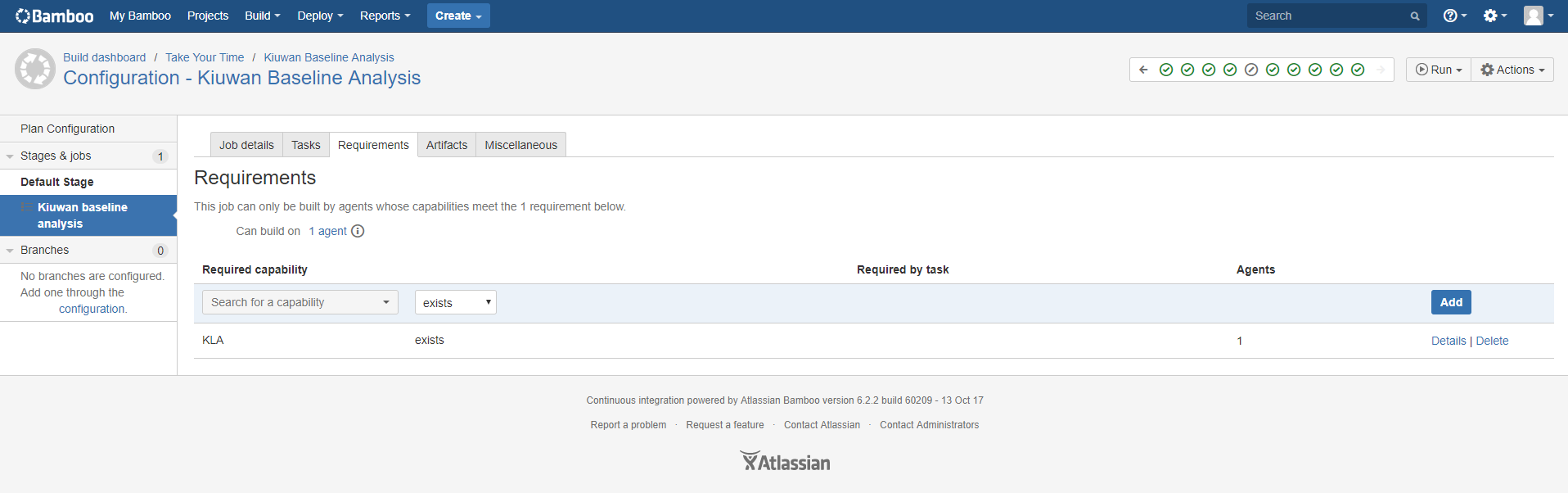
Next you can create a stage to add the aKiuwan analysis job to it or add a job in an existing stage (like we have done here in the default stage). In the Job definition, first you can configure a requirement, searching for the KLA capability and specify the it must ‘exist’. This ensures that the job is sent to an agent that has the KLA installed.
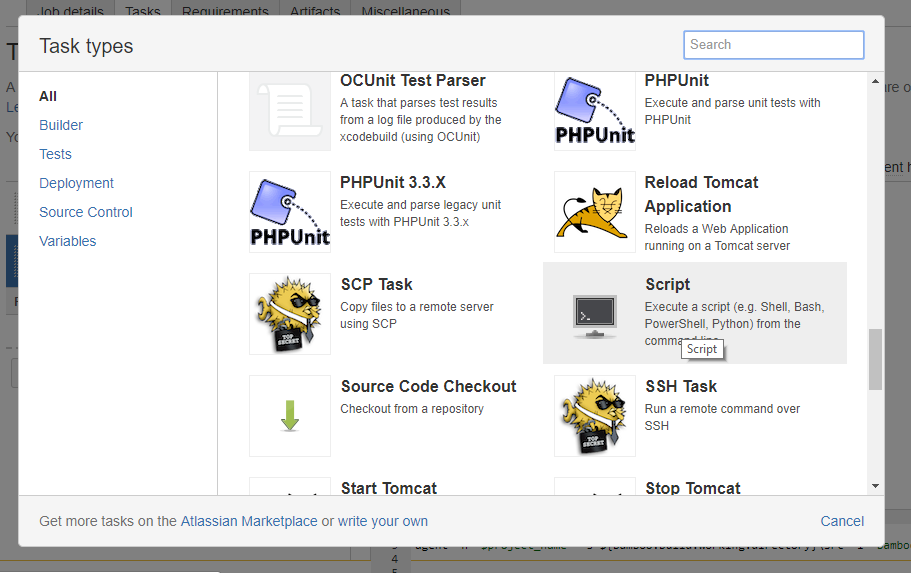
Then go to the Tasks tab to configure the Kiuwan analysis task. Kiuwan needs the source code to analyze it, so make sure that there is a ‘Source Code Checkout’ task before anything else.
After that at least add a Script task to run the Kiuwan analysis. You can configure more tasks (like build) in this stage or just use it only for the analysis. It is up to you how you want to do it.
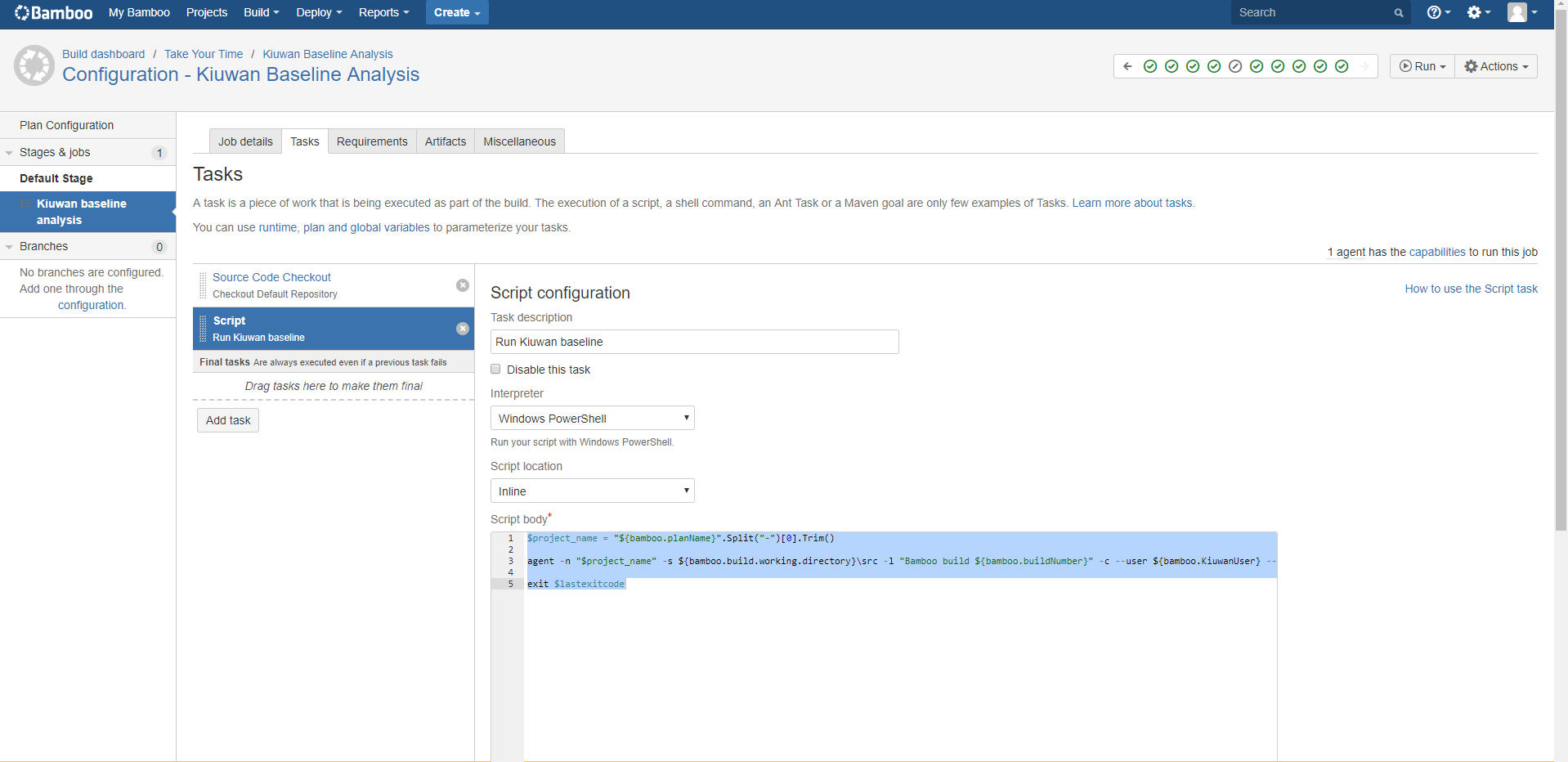
Select the new Script task, add a description (in our case Kiuwan baseline analysis, because that is what it is going to do), select the Windows PowerShell if your agents are Windows based (they could be linux based as well. In that case, you have to specify a different agent capability and here select Shell). Next, select Inline in script location (you could have a file in your repository with the script to run). Finally, enter the following script code in the Script body text area:
This is a PowerShell example, using some PowerShell commandlets. You can come up with a similar script for Linux shells mimicking the functionality.
$project_name = "${bamboo.planName}".Split("-")[0].Trim()
agent -n "$project_name" -s ${bamboo.build.working.directory}\src -l "Bamboo build ${bamboo.buildNumber}" -c --user ${bamboo.KiuwanUser} --pass ${bamboo.KiuwanPassword} -wr
exit $lastexitcode
Alternative Kiuwan analysis. Delivery
Kiuwan can run 2 different types of analysis baseline and delivery. In the previous example the script Kiuwan command runs a baseline analysis if you want to run a delivery analysis you script will look something like:
$project_name = "${bamboo.planName}".Split("-")[0].Trim()
$change_request = "New CR"
agent -n $project_name -s ${bamboo.build.working.directory}\src -l "${bamboo.shortPlanKey}${bamboo.shortJobKey}-${bamboo.buildNumber}" -as completeDelivery -crs resolved -cr ${bamboo.planRepository.branch} -bn ${bamboo.planRepository.branch} --user ${bamboo.KiuwanUser} --pass ${bamboo.KiuwanPassword} -wr
exit $lastexitcode
When do you run a baseline or a delivery analysis? That is up to you and your development process. The difference between the examples here is that the delivery analysis will return a non-zero (10) exit code if the Kiuwan audit falis so the stage will fail, depending on how you configure the plan it could fail in turn. Check the Kiuwan life cycle documentation for more info on deliveries and audits that implement your security policies for changes.
A good use case could be to run a Delivery analysis for every pull request, so the policy is applied before the merge. The merge can be blocked if the pull request doesn’t pass the Kiuwan audit.
Run your build plans
You can run the build plan manually or define different triggers and strategies to run them automatically.
What you do will depend on your development process.
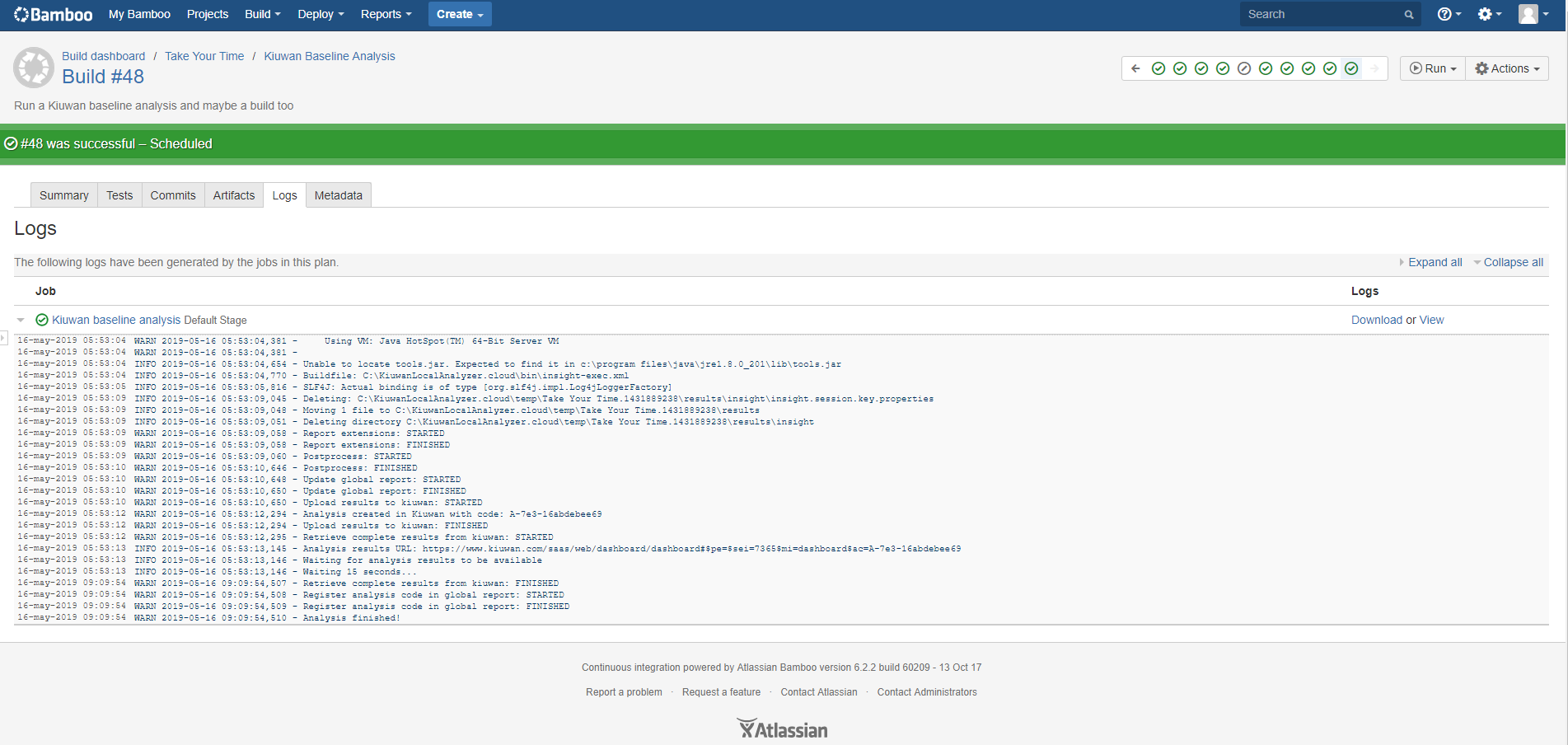
You can follow the Kiuwan task execution on-line or check the logs after execution:
Check your Kiuwan analysis results
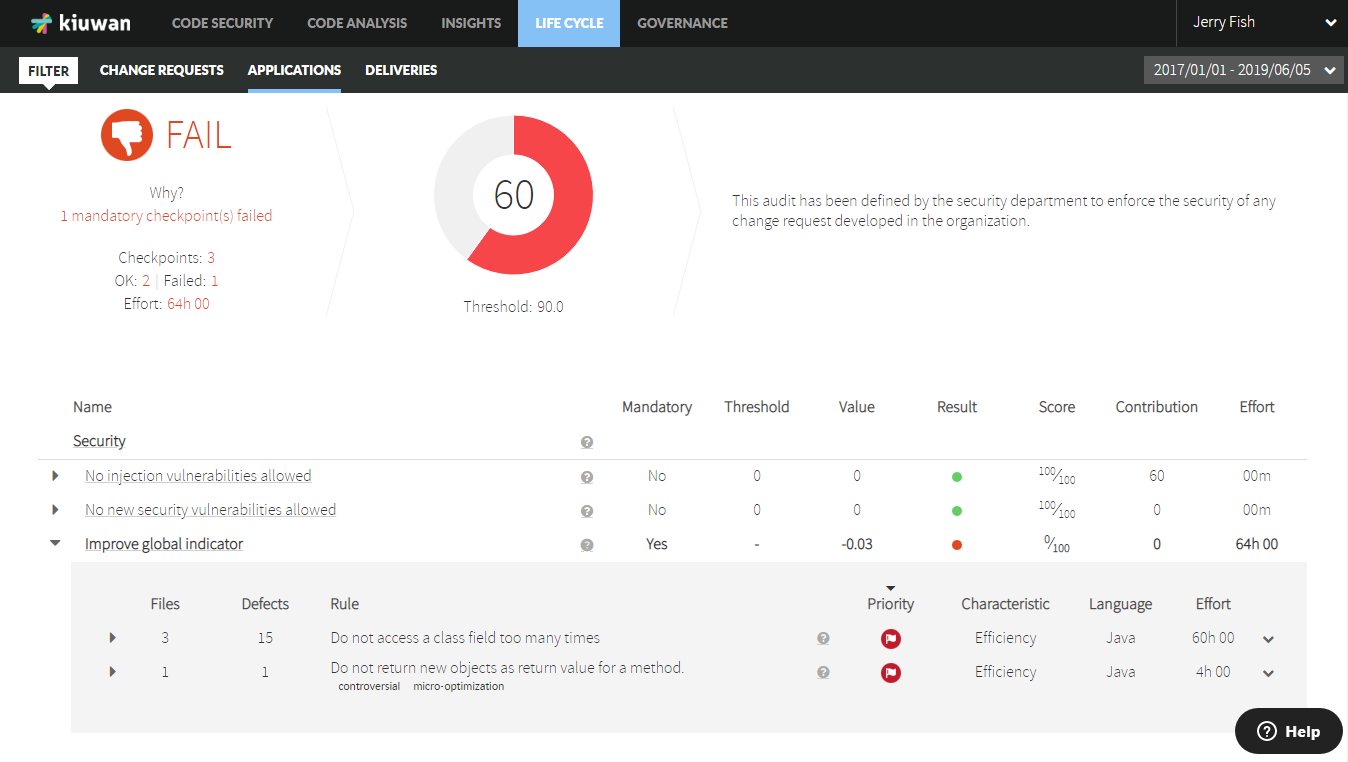
Finally got to your Kiuwan account and check the results. If the analysis was a baseline go to Code Security:
Or check the Kiuwan audit results for delivery analyses: