...
Appendix - Azure Active Directory configuration : How to configure Kiuwan as Service Provider
You must configure your Idp (Azure AD) so it recognizes Kiuwan as a SP (Service Provider).
In Azure AD, you should create an Enterprise Application (Kiuwan SSO, in this example).
To do it, select Azure Active Directory >> Enterprise applications
and click on New application
Select Non-gallery application and fill in the app name (Kiuwan SSO in our example) and click Add button
Just created, you will see a page like this.
Next, you will need to add users that will be allowed to login at Kiuwan SSO application.
Select the users from your Azure Active Directory that will be allowed to login to Kiuwan SSO application.
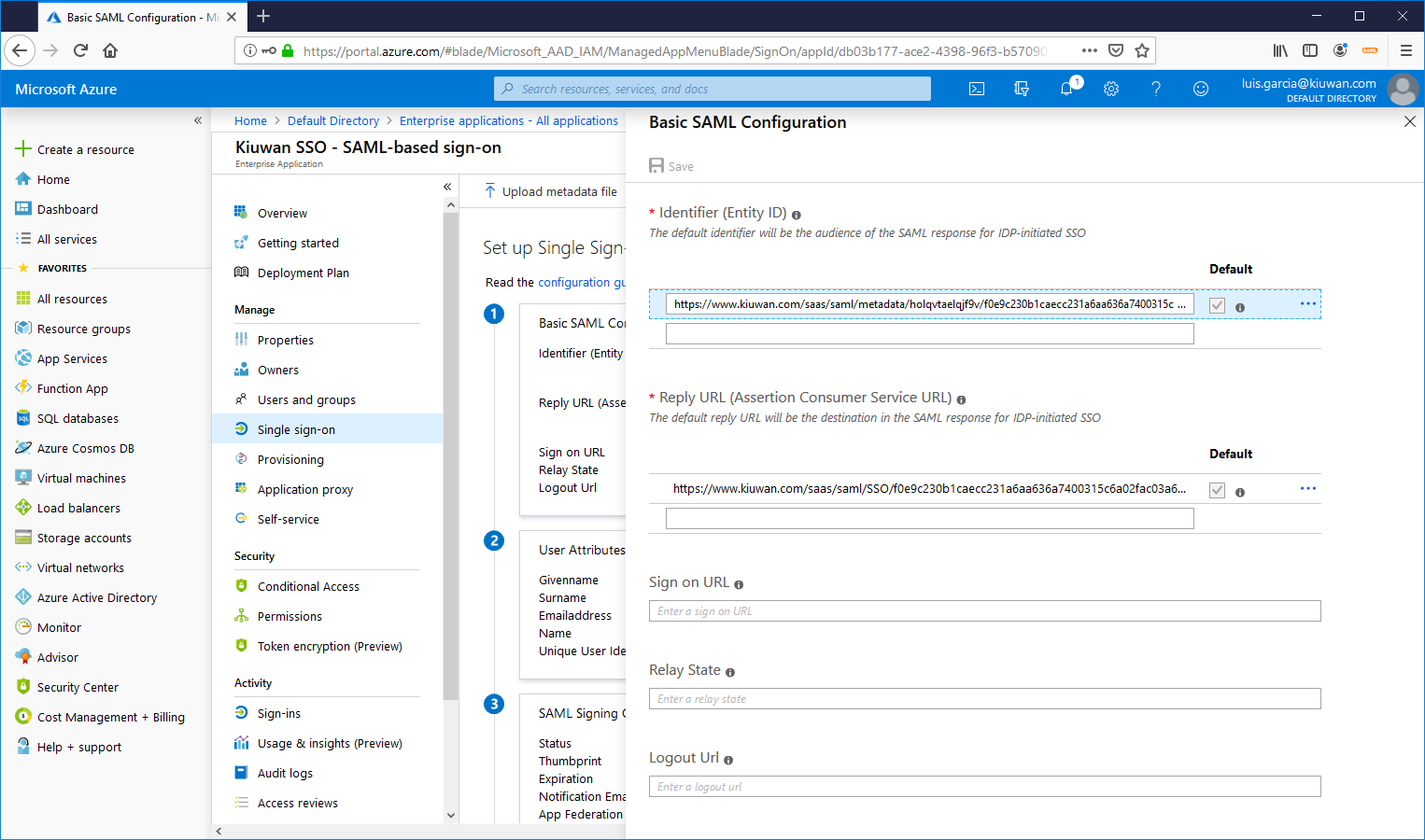
Now that some user has been added, you need to configure the Single sign-on
First, you need to export the Azure Active Directory metadata and import it to Kiuwan.
To export AAD metadata, click on Download link at Federation Metadata XML.
| Info |
|---|
Downloaded XML file needs to be imported into your Kiuwan account , as shown before. After importing AAD metadata into Kiuwan, your Kiuwan account will be ready to generate its own metadata that you will import into AAD. |
To export Kiuwan metadata, go to Account Management >> Organization and you will see the URL to download Kiuwan metadata.
Just type the URL in a browser and save the content as a XML file.
| Info |
|---|
Now, you can import (upload) the Kiuwan metadata XML file into AAD. |
Once uploaded, click con Save.
Once done, you need to set your Claims policy. To do it, click on User Attributes & Claims
Select Name identifier value
and setup the policy on how to manage your ADA usernames to Kiuwan usernames.
In this example, we take the first part of email.
For example, an AAD user with email john.doe@domain.com will be mapped to john.doe when sent to Kiuwan.
Now, you can test Single Sign-On with Kiuwan SSO app.
Just click to Test button.
Select the user (the current or someone else)
Because you are already logged in ADD (and therefore authenticated) you will be forwarded directly to Kiuwan app.
Login from Kiuwan site
Login from Kiuwan site