| Table of Contents |
|---|
...
New version of
...
CQM, Kiuwan Engine and
...
SAP Extractor
| Info |
|---|
Main features of this release are:
|
Kiuwan CQM and Engine
...
New SAP HANA SQLScript Rules
As SAP is introducing many new programming technologies, more and more SAP users are confronted with new languages besides ABAP.
One of these is SAP HANA SQLScript, which is used to develop high-performance stored procedures for the SAP HANA in-memory database.
Kiuwan adds support for SQLScript by providing a specific set of SQLScript rules (*) that will apply to files with extensions: .sqlscript and .hana
- OPT.HANA.EFFICIENCY.AvoidTraceInProduction
- OPT.HANA.EFFICIENCY.AvoidUsingCursors
- OPT.HANA.EFFICIENCY.DeeplyNestedSubqueries
- OPT.HANA.EFFICIENCY.ModificationStatementInLoop
- OPT.HANA.EFFICIENCY.NonTrivialSubquery
- OPT.HANA.EFFICIENCY.ReadsSqlDataNotSpecified
- OPT.HANA.EFFICIENCY.SelectInScalarFunction
- OPT.HANA.EFFICIENCY.UnusedVariable
- OPT.HANA.EFFICIENCY.UseOfCalculationEngineOperator
- OPT.HANA.MAINTAINABILITY.LanguageNotSpecified
- OPT.HANA.MAINTAINABILITY.UnusedCondition
- OPT.HANA.RELIABILITY.ImproperParameterUsage
- OPT.HANA.RELIABILITY.NonCustomErrorCode
- OPT.HANA.RELIABILITY.UseOfUninitializedVar
- OPT.HANA.SEC.ExcessivePrivilegesGranted
- OPT.HANA.SEC.ForbiddenCall
- OPT.HANA.SEC.SqlInjection
| Info |
|---|
A new version of CQM has been released that incorporate new rules (as detailed below). CQM is the default Model (i.e. a concrete set of active and pre-configured rules):
You can find new rules by comparing this release of CQM against previous version. A detailed description of the behavior of these new rules is available in rule’s description. |
| Info |
|---|
A new version of Kiuwan Engine has been released that incorporates bug fixes, performance and reliability improvements in rules and parsers. Kiuwan Engine is the binary code executed when an analysis is run.
|
Additional support for detection of NoSQL Injection vulnerabilities
Support has been added to Kiuwan to detect NoSQL Injection vulnerabilities.
Additionaly to JavaScript, C# and VB.NET, Kiuwan provides support for Java, PHP, Python and Objective-C.
New VB.NET security rules
- OPT.VBNET.CodeInjection
- OPT.VBNET.CodeInjectionWithDeserialization
- OPT.VBNET.CommandInjection
- OPT.VBNET.CrossSiteRequestForgery
- OPT.VBNET.CrossSiteScripting
- OPT.VBNET.DoSRegexp
- OPT.VBNET.InsecureRandomness
- OPT.VBNET.JSONInjection
- OPT.VBNET.LdapInjection
- OPT.VBNET.MVCNonActionPublicMethods
- OPT.VBNET.MVCPostInControllers
- OPT.VBNET.MVCPreventOverpostingModelDefinition
- OPT.VBNET.MVCPreventUnderpostingModelComposition
- OPT.VBNET.MVCPreventUnderpostingModelDefinition
- OPT.VBNET.MVCRemoveVersionHeader
- OPT.VBNET.OpenRedirect
- OPT.VBNET.PathTraversal
- OPT.VBNET.PotentialInfiniteLoop
- OPT.VBNET.ResourceLeakDatabase
- OPT.VBNET.ResourceLeakLdap
- OPT.VBNET.ResourceLeakStream
- OPT.VBNET.ResourceLeakUnmanaged
- OPT.VBNET.SEC.AccessibilitySubversionRule
- OPT.VBNET.SEC.AnonymousLdapBind
- OPT.VBNET.SEC.AvoidHostNameChecks
- OPT.VBNET.SEC.ConnectionStringParameterPollution
- OPT.VBNET.SEC.CookiesInSecurityDecision
- OPT.VBNET.SEC.CrossSiteHistoryManipulation
- OPT.VBNET.SEC.DangerousFileUpload
- OPT.VBNET.SEC.HardcodedCredential
- OPT.VBNET.SEC.HardcodedCryptoKey
- OPT.VBNET.SEC.HardcodedNetworkAddress
- OPT.VBNET.SEC.HardcodedSalt
- OPT.VBNET.SEC.HttpParameterPollution
- OPT.VBNET.SEC.HttpRequestValueShadowing
- OPT.VBNET.SEC.HttpSplittingRule
- OPT.VBNET.SEC.ImproperAuthentication
- OPT.VBNET.SEC.InformationExposureThroughDebugLog
- OPT.VBNET.SEC.InformationExposureThroughErrorMessage
- OPT.VBNET.SEC.InsecureEmailTransport
- OPT.VBNET.SEC.InsecureTransport
- OPT.VBNET.SEC.LogForging
- OPT.VBNET.SEC.MailCommandInjection
- OPT.VBNET.SEC.MainMethodInWebApplication
- OPT.VBNET.SEC.MissingStandardErrorHandling
- OPT.VBNET.SEC.NoSQLInjection
- OPT.VBNET.SEC.PlaintextStorageOfPassword
- OPT.VBNET.SEC.ProcessControl
- OPT.VBNET.SEC.ProperPaddingWithPublicKeyCrypto
- OPT.VBNET.SEC.RegistryManipulation
- OPT.VBNET.SEC.ResourceInjection
- OPT.VBNET.SEC.SerializableClassContainingSensitiveData
- OPT.VBNET.SEC.ServerInsecureTransport
- OPT.VBNET.SEC.SettingManipulation
- OPT.VBNET.SEC.StaticDatabaseConnection
- OPT.VBNET.SEC.TemporaryFilesLeft
- OPT.VBNET.SEC.TrustBoundaryViolation
- OPT.VBNET.SEC.UnsafeCookieRule
- OPT.VBNET.SEC.UnsafeReflection
- OPT.VBNET.SEC.UnvalidatedAspNetModel
- OPT.VBNET.SEC.UserControlledSQLPrimaryKey
- OPT.VBNET.SEC.XMLEntityInjection
- OPT.VBNET.ServerSideRequestForgery
- OPT.VBNET.SqlInjection
- OPT.VBNET.StoredCrossSiteScripting
- OPT.VBNET.SystemInformationLeak
- OPT.VBNET.TooMuchOriginsAllowed
- OPT.VBNET.UncheckedInputInLoopCondition
- OPT.VBNET.UncheckedReturnValue
- OPT.VBNET.WeakCryptographicHash
- OPT.VBNET.WeakEncryption
- OPT.VBNET.WeakKeySize
- OPT.VBNET.WeakSymmetricEncryptionAlgorithm
- OPT.VBNET.WeakSymmetricEncryptionModeOfOperation
- OPT.VBNET.XMLInjection
- OPT.VBNET.XPathInjection
- OPT.VBNET.XQueryInjection
- OPT.VBNET.XSLTInjection
New Objective-C security rules
- OPT.OBJECTIVEC.SECURITY.AvoidSMS
- OPT.OBJECTIVEC.SECURITY.BiometricWithoutMessage
- OPT.OBJECTIVEC.SECURITY.CommandInjectionRule
- OPT.OBJECTIVEC.SECURITY.ConnectionStringParameterPollution
- OPT.OBJECTIVEC.SECURITY.ExecutionAfterRedirect
- OPT.OBJECTIVEC.SECURITY.HardcodedCryptoKey
- OPT.OBJECTIVEC.SECURITY.HardcodedIp
- OPT.OBJECTIVEC.SECURITY.HardcodedUsernamePassword
- OPT.OBJECTIVEC.SECURITY.HttpParameterPollutionRule
- OPT.OBJECTIVEC.SECURITY.HttpResponseCachingLeak
- OPT.OBJECTIVEC.SECURITY.HttpSplittingRule
- OPT.OBJECTIVEC.SECURITY.InformationExposureThroughErrorMessage
- OPT.OBJECTIVEC.SECURITY.InsecureTemporaryFile
- OPT.OBJECTIVEC.SECURITY.KeyboardCachingLeak
- OPT.OBJECTIVEC.SECURITY.MailCommandInjection
- OPT.OBJECTIVEC.SECURITY.MissingContentValidation
- OPT.OBJECTIVEC.SECURITY.MissingPasswordFieldMasking
- OPT.OBJECTIVEC.SECURITY.NoSQLInjection
- OPT.OBJECTIVEC.SECURITY.LogForging
- OPT.OBJECTIVEC.SECURITY.PasswordInCommentRule
- OPT.OBJECTIVEC.SECURITY.PasswordInConfigurationFile
- OPT.OBJECTIVEC.SECURITY.PasteboardCachingLeak
- OPT.OBJECTIVEC.SECURITY.PlaintextStorageInACookieRule
- OPT.OBJECTIVEC.SECURITY.PotentialInfiniteLoop
- OPT.OBJECTIVEC.SECURITY.PrivacyViolation
- OPT.OBJECTIVEC.SECURITY.ResourceInjection
- OPT.OBJECTIVEC.SECURITY.ScreenCachingLeak
- OPT.OBJECTIVEC.SECURITY.SensitiveCoreData
- OPT.OBJECTIVEC.SECURITY.SensitiveDataAccessedFromItunes
- OPT.OBJECTIVEC.SECURITY.SensitiveNoSQL
- OPT.OBJECTIVEC.SECURITY.SensitiveSQL
- OPT.OBJECTIVEC.SECURITY.SensitiveUserDefaults
- OPT.OBJECTIVEC.SECURITY.SerializableClassContainingSensitiveData
- OPT.OBJECTIVEC.SECURITY.SerializationInjection
- OPT.OBJECTIVEC.SECURITY.ServerTrustCredentialCheck
- OPT.OBJECTIVEC.SECURITY.ThirdPartyKeyboardAllowed
- OPT.OBJECTIVEC.SECURITY.UncheckedInputInLoopCondition
- OPT.OBJECTIVEC.SECURITY.UnsafeCookie
- OPT.OBJECTIVEC.SECURITY.URLSchemeHijacking
- OPT.OBJECTIVEC.SECURITY.UserControlledSQLPrimaryKey
- OPT.OBJECTIVEC.SECURITY.WeakKeyDerivationIteration
- OPT.OBJECTIVEC.SECURITY.WeakKeyDerivationPassword
- OPT.OBJECTIVEC.SECURITY.XMLInjection
Additional support for detection of NoSQL Injection vulnerabilities
Support has been added to Kiuwan to detect NoSQL Injection vulnerabilities.
Additionaly to JavaScript, C# and VB.NET, Kiuwan provides support for Java, PHP, Python and Objective-C.
(*) You can find new rules by comparing this release of CQM against previous version.
A detailed description of the behavior of these new rules is available in rule’s description.
Unless you have blocked Kiuwan Engine, Kiuwan Local Analyzer will automatically upgrade it to the last version once a new analysis is run.
In order for these new rules be applicable, your Kiuwan account must be configured to allow automatic engine upgrade:
- If you are using CQM, these new rules will automatically become active and will be applied to new analyses.
- If you are using your own custom model, you can activate them in case you want to be applied to your code.
Recategorization of TypeScript and Angular rules
After adding support to TypeScript, it was not clear for many users that TypeScript support was embedded within JavaScript.
This approach led to some confussions, so we have unified JavaScript and TypeScript as a unique technology (JavaScript/TypeScript), instead of just JavaScript as before).
Although some would argue that JavaScript and TypeScript should be considered as different languages, Kiuwan rules for JavaScript were re-written to apply to both languages.
- All existing JavaScript rules are able to distinguish between JavaScript and TypeScript source code, acting accordingly.
- Nevertheless, there are some rules specific to TypeScript (filter : Framework -> TypeScript )
Besides, Angular rules have been cathegorized according to Angular versions:
- Angular versions previous to 2.x : filter : Framework -> AngularJS
- Angular versions equal or above 2.x : filter : Framework -> Angular
Kiuwan Website
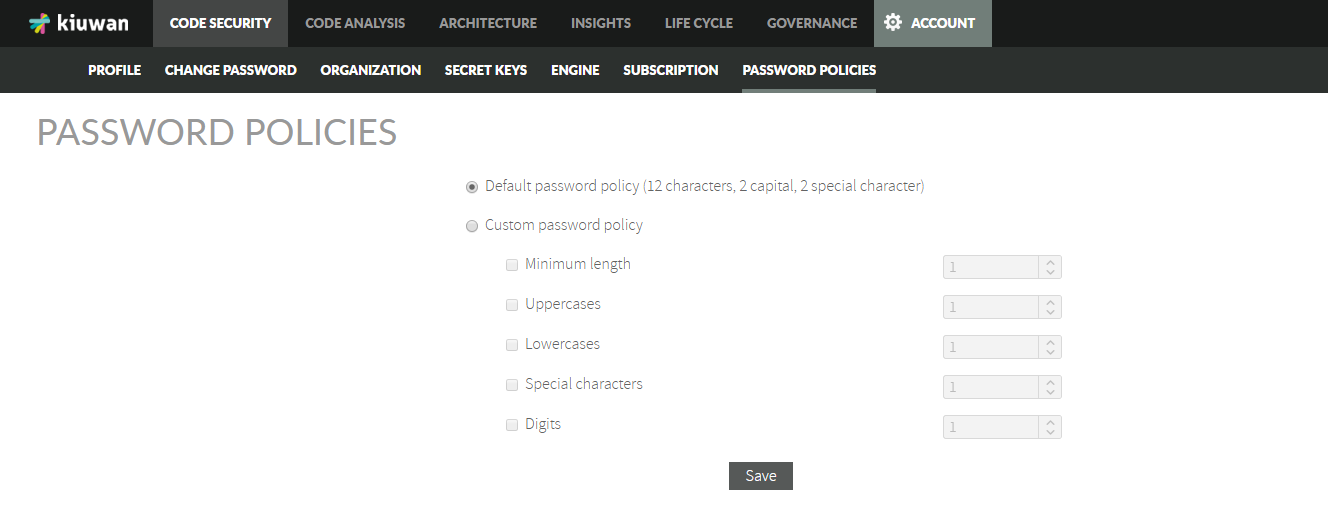
New Passwords Policy
Kiuwan has implemented a more strict password policy that applies to password strength.
This new policy will be applied to any new password (a new one or a modification of a existing one).
For any account, there will be a default policy (12 characters, 2 capital, 2 special characters) but you can customize it to your own requirements.
You can set your acccount's password policy at Account Management >> Password Policies tab (only available to account owner)
Kiuwan Insights
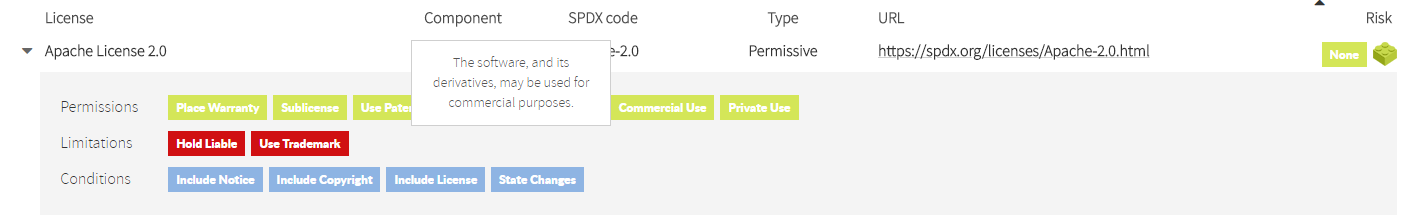
Enhanced readability of Software Licenses Terms
Hovering the mouse over the terms you will get further detail.
New release of SAP Extractor for Kiuwan
New SAPEX distribution (as a Transport Order)
Older versions of SAPEX were delivered as source files that needed to be manually imported into SAP.
This version includes a Transport Order that you can directly import into your SAP system, avoiding manually import all the SAPEX sources.
You can find detailed info at SAP Extractor for Kiuwan
Support for On-Demand Analysis of In-progress Change Requests
This new version include SAP programs so you may analyze a Chage Request (or Task) currently in progress.
You can find detailed info at SAP Extractor for Kiuwan and Local use - In-Progress Deliveries