...
Insights >> Security
...
...
...
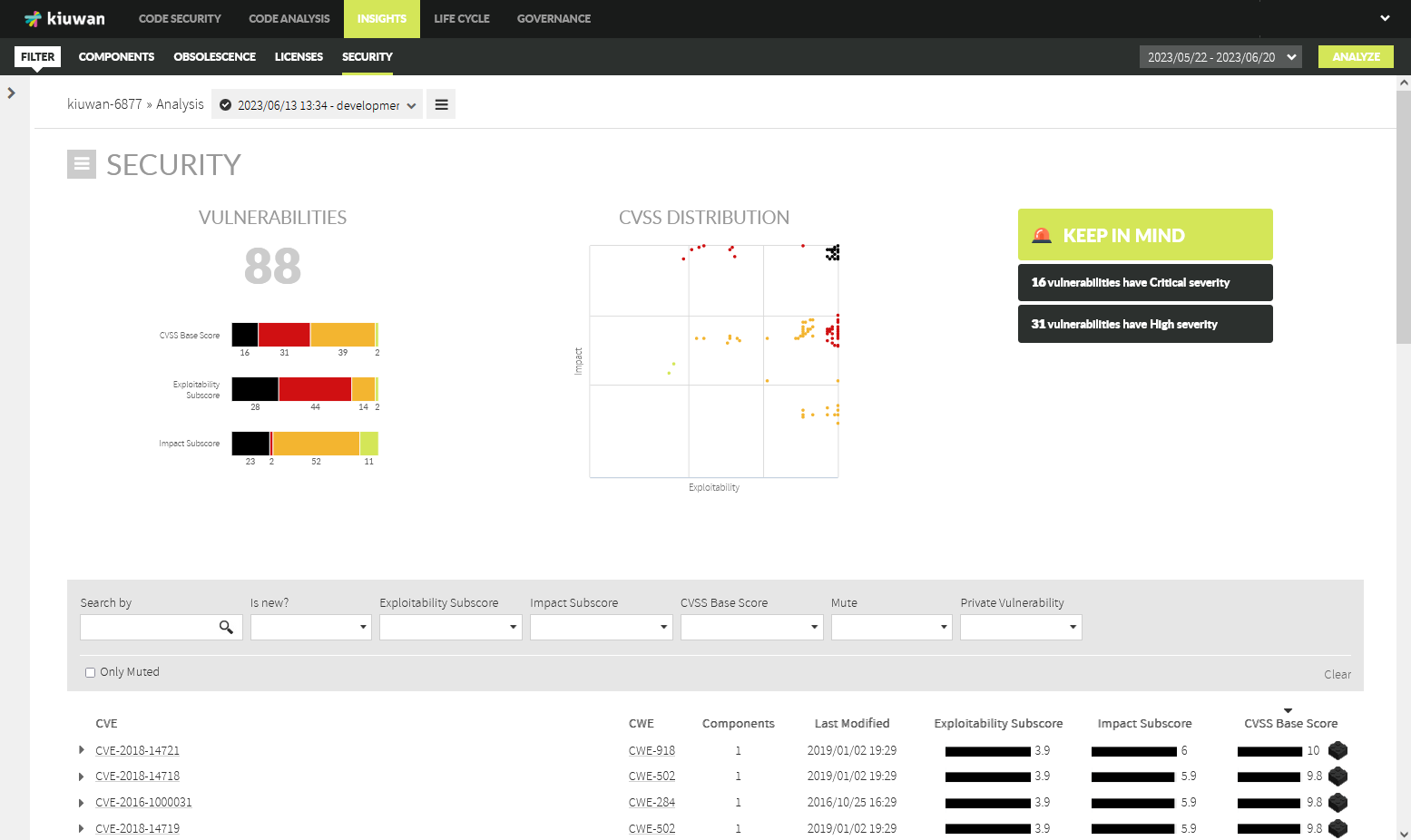
Information on components’ Security is accessible through Insights >> Security tab.
Security Risk
With Kiuwan Insights you can easily detect those components that have well-known security vulnerabilities.
...
...
...
...
This list is continuously growing.
...
...
...
...
...
...
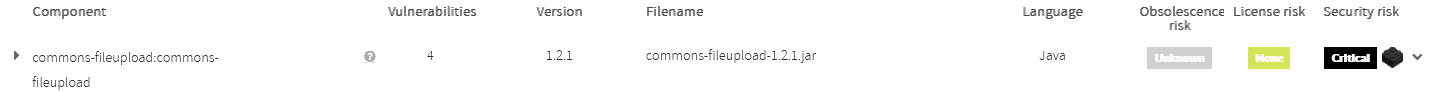
For example, let’s suppose your app is using Struts TagLib 1.3.8. Kiuwan will display next information:
Struts TagLib 1.3.8 has 4 known vulnerabilities, three are considered as Medium and one as High. Therefore, Kiuwan will mark Struts TagLib 1.3.8 as High.
...
...
Security Risk Indicator
...
Value
...
Label
...
0
...
( 0 , 4 ]
...
( 4 , 7 ]
...
( 7, 10 ]
...
...
...
...
...
...
...
...
...
...
...
...
...
...
...
...
...
...
...
...
...
| Info |
|---|
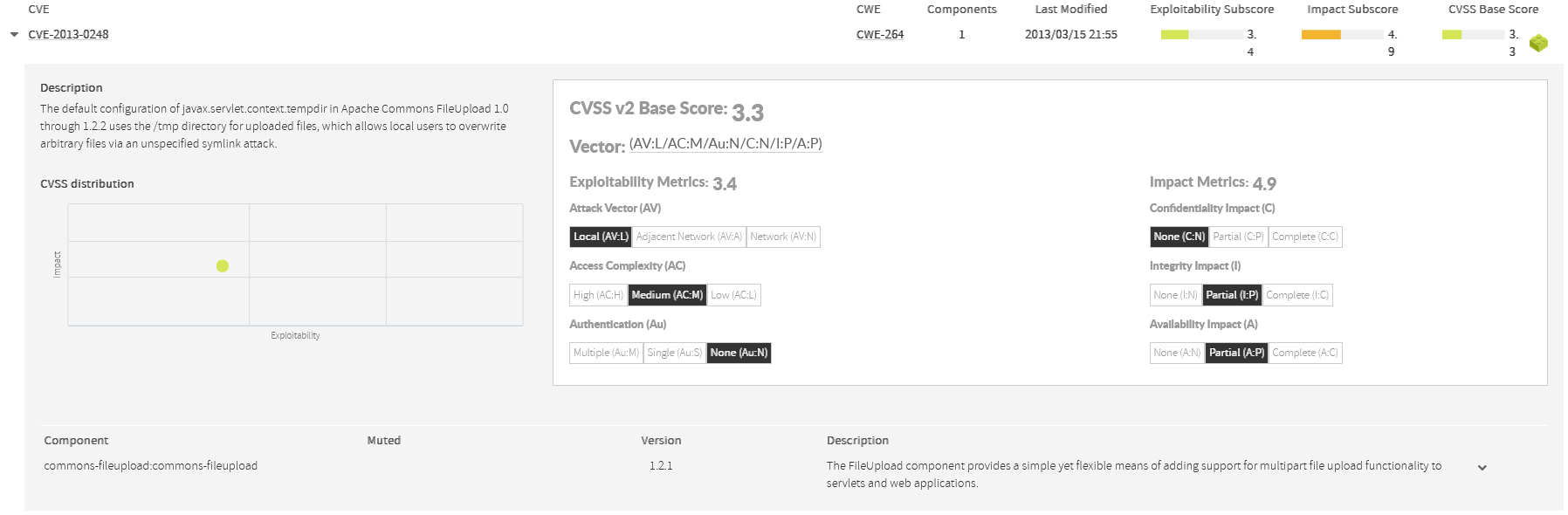
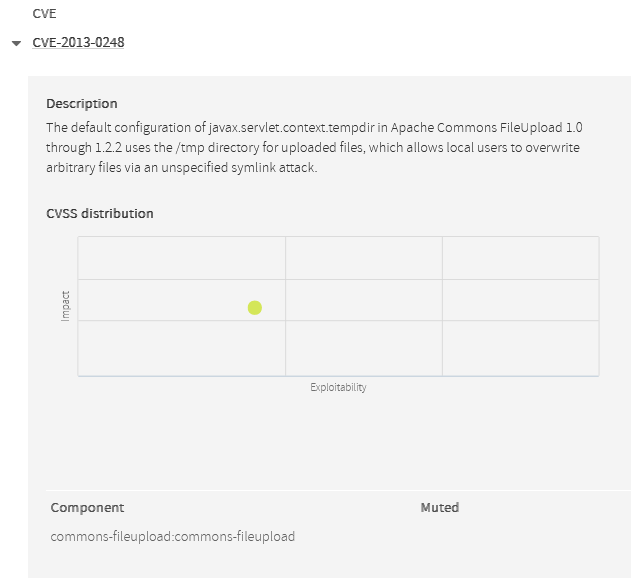
Kiuwan Insights provides a 2-axis figure that can help you to easily understand these two important characteristics of the vulnerability.
|
...
...
...
...
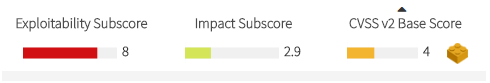
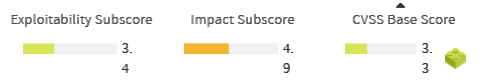
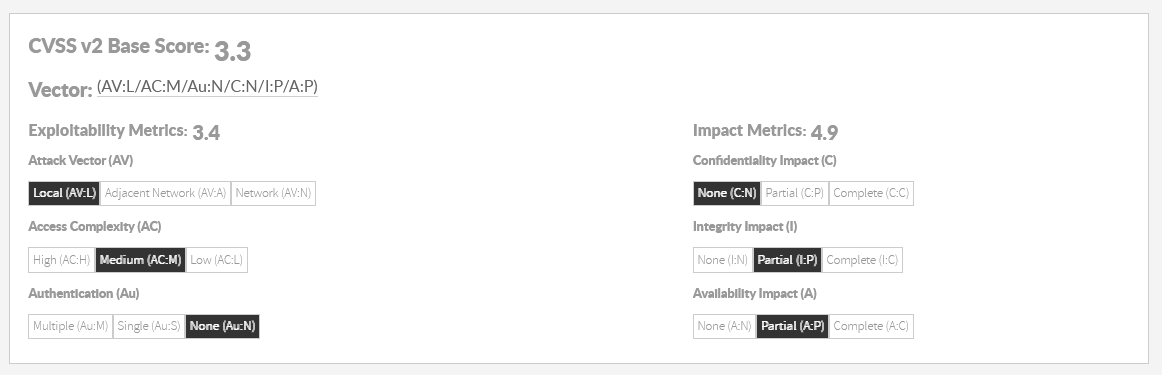
Let’s understand the meaning of every metric.
...
...
...
...
...
...
...
...
...
...
...
...
...
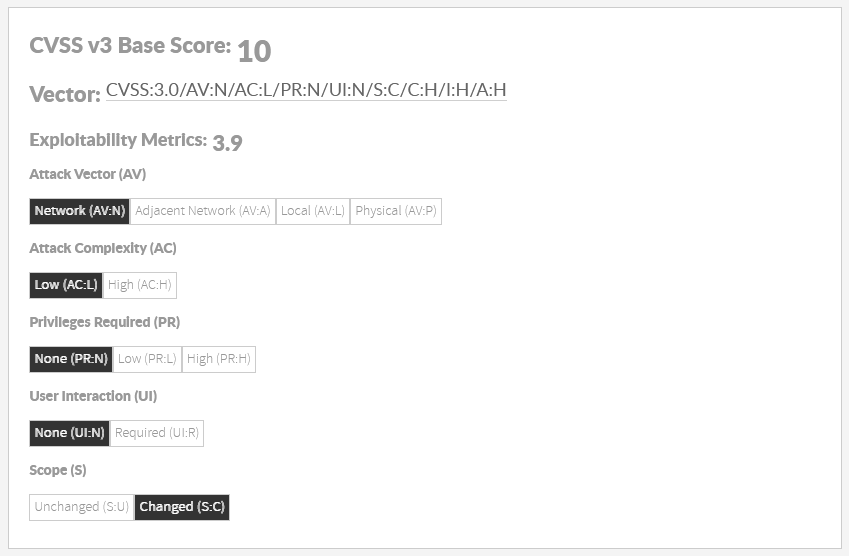
However, not all vulnerabilities reported to NIST‘s National Vulnerability Database (NVD) have been scored according to v3 guidelines. Indeed, only a subset of them has been re-scored.
| Info |
|---|
Because of this, although Kiuwan Insights displays v3 data (when available), only v2 data will be used when computing components’ Security Risk indicator. |
New vulnerabilities
...
...
...
...
...
...
...