...
How to understand tainted-flow vulnerabilities
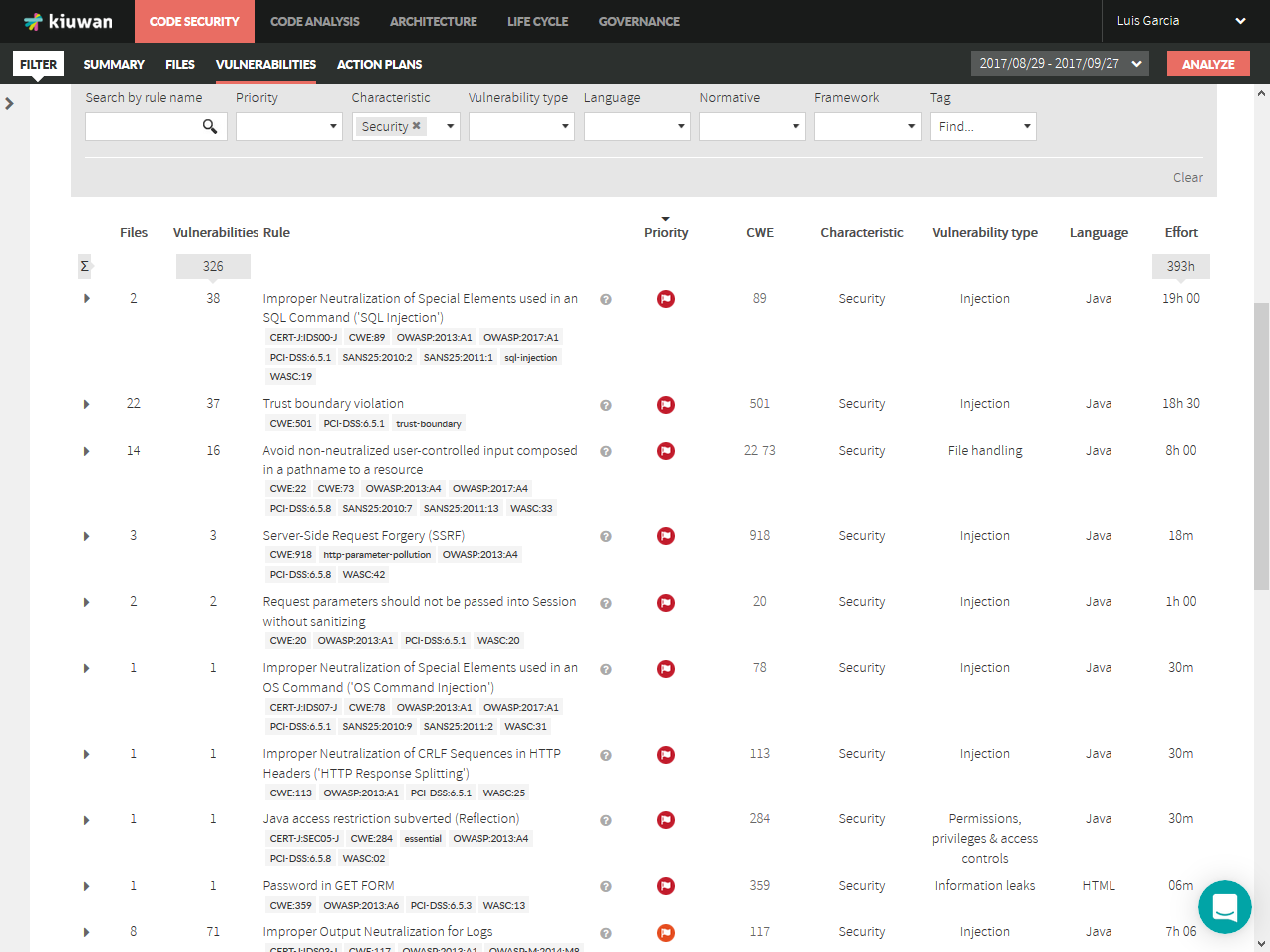
Vulnerabilities are reported at Code Security – Vulnerabilities section.
| Info |
|---|
All the vulnerabilities of the same type (i.e. coming from the same Kiuwan rule that checks for it) are grouped under the Kiuwan rule name, indicating how many files are “affected” and how many vulnerabilities were found. |
Finding Vulnerabilities (e.g. SQL Injection)
For our explanation, we will follow an example based on Waratek – Spiracle software, focused on SQL-Injection vulnerabilities.
Below image shows SQl-Injection vulnerabilities. Just use the "Search by rule name" filter..
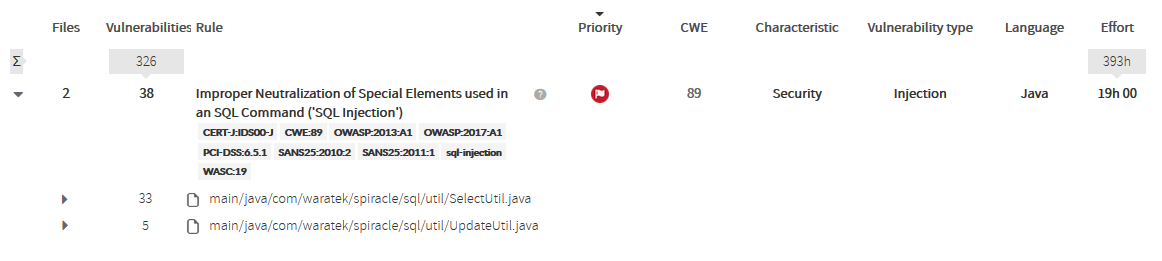
We can see in the image that there are 2 files affected, i.e. two files where there’s a sink that is being feed by tainted data, i.e. an injection point.
Also, we can see that for every file there are a number of vulnerabilities.
What do those vulnerabilities mean? See next image.
Graphical view of all Sources and Sinks related with a Vulnerability
For every vulnerability, you could see next icon
Clicking on that icon will open a graphical view of the complete set of sources, sinks and tainted flows of the selected vulnerability (rule) of your application.
Tainted data flows are represented as directed graphs from sources (at the top) to sinks (at the bottom).
Any element may have a number that indicates in which many tainted data flows participates.
You can see the detail of any element (source, sink or propagation node) by hovering the mouse overt it. A dialog information will be displayed as in the image below.
Finding Sources and Sinks
| Info |
|---|
Clicking on the affected file will open all its affected sinks. |
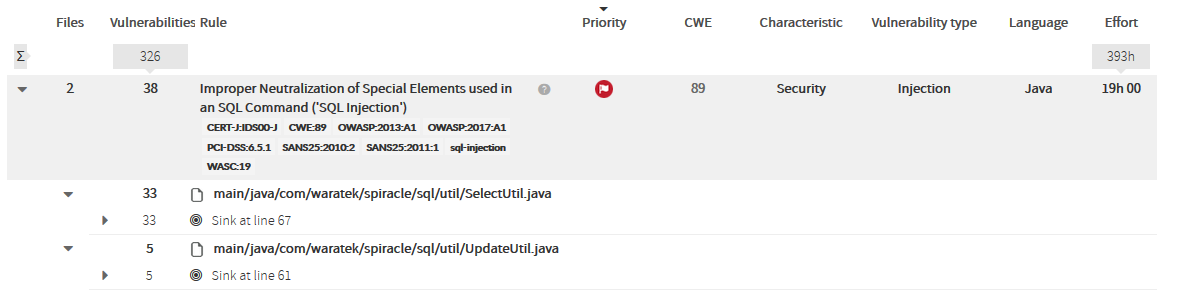
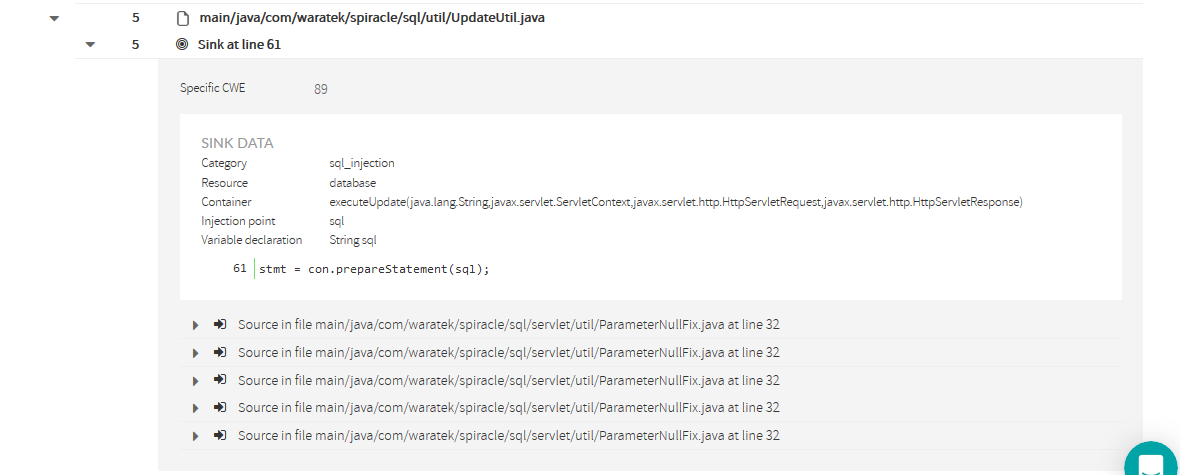
In this case, there’s only one sink for every file (only one injection point), but it could be many… Kiuwan will display all the line numbers of the affected sinks.
| Info |
|---|
Clicking on a sink will display its details as well as all the sources where data is collected form an untrusted source and flows to the sink without being neutralized (or sanitized). |
Sink's detailed information
| Info | ||
|---|---|---|
| ||
Sink detail includes following information:
|
Most commonly, every source will be a different file. But depending on the flow path, you could find same source and line many times.
Let’s see how to understand every source.
Source's detailed information
Clicking on a source will open a frame with information about the source.
| Info | ||
|---|---|---|
| ||
Source detail includes following information:
|
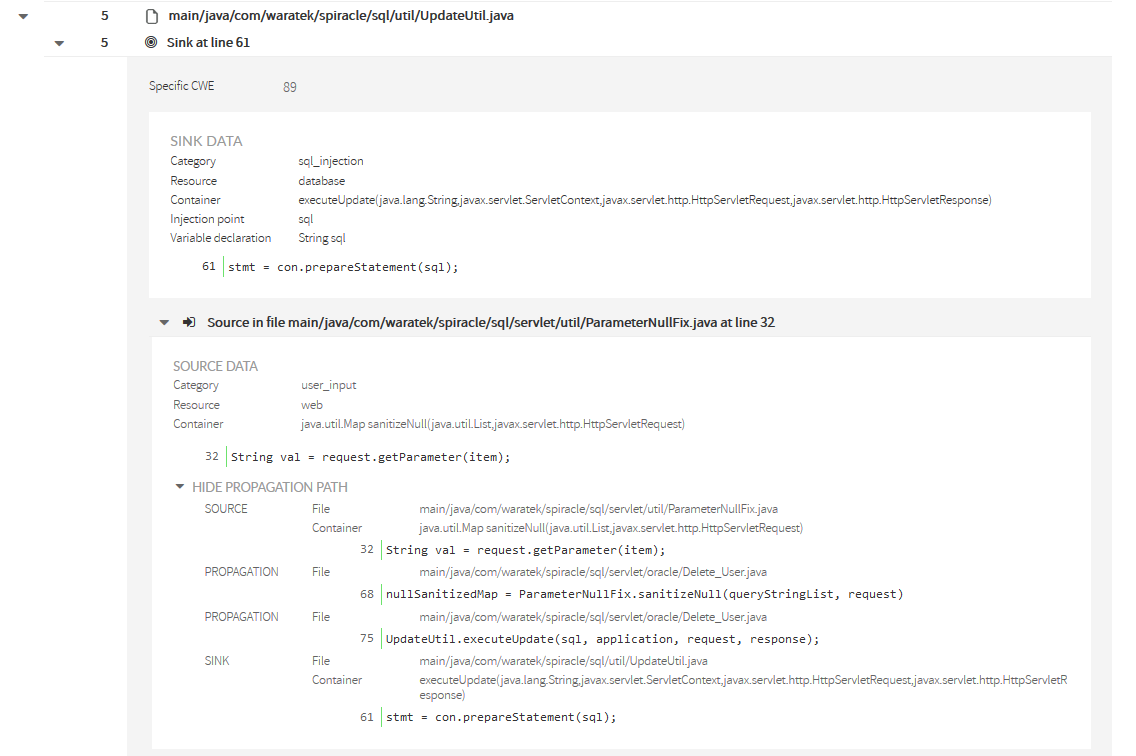
Propagation Path
| Info | ||
|---|---|---|
| ||
Important: You should not understand the propagation path as a typical stack of method calls. It’s not that. You should understand it as a data-flow path. |
Let’s see with the example.
| Info |
|---|
Any propagation path is composed of a source node, a sink node and as many propagation nodes as different methods are involved in the propagation path. |
In the example, we can see the next propagation path (flowing from source to sink) :
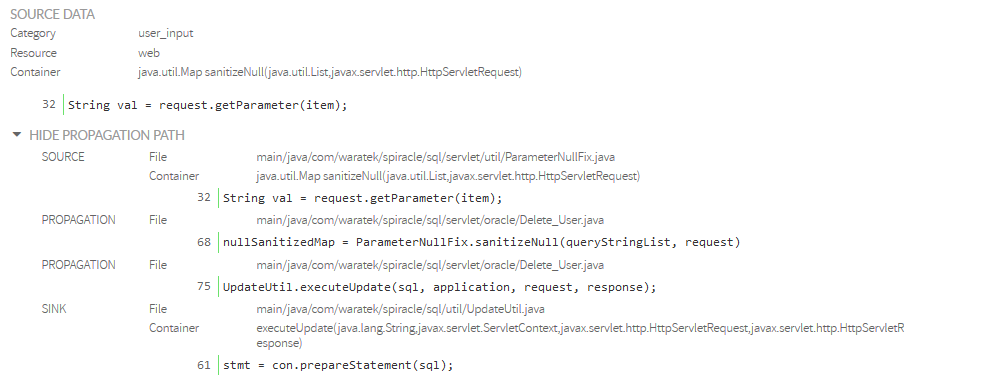
- Source node indicates that file ParameterNullFix.java line 32 (within sanitizeNull method) gets the value from a request parameter.
- This is marked a source because HttpServletRequest.getParameter(..) is considered as an untrusted input source (i.e. is directly manipulated by the user) and no neutralization routine has been found.
- First propagation node indicates that Delete_User.java line 68 receives back the above tainted data.
- Second propagation node indicates that Delete_User.java line 75 sends the tainted data (via method parameter) to another object through UpdateUtil.executeUpdate(…) method call.
- Looking at the source code, you could see that the tainted data is directly appended to a sql string without any neutralization, allowing this way to directly insert user code into the sql sentence.
- Sink node indicates that file UpdateUtil.java line 61 (within executeUpdate(…) method) injects tainted data (sql sentence) to a PreparedStatement that finally is executed against the database.
Once explained a concrete source-sink propagation path, let’s go back to the initial sink information.
...