Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
This section will guide you through the summary dashboard of Kiuwan Code Security.
The Code Security Summary page provides a comprehensive dashboard showcasing a high level overview of the securit of your application.
Code Security Summary providesThis dashboard shows the following:
| Table of Contents |
|---|
- Overall security rating,
- Vulnerabilities quadrant,
- Effort to reach upper levels of security,
- Top-10 security vulnerabilities,
- Top-10 worst files, and
- Timeline evolution of security indicators
Image Removed
Security Rating
|
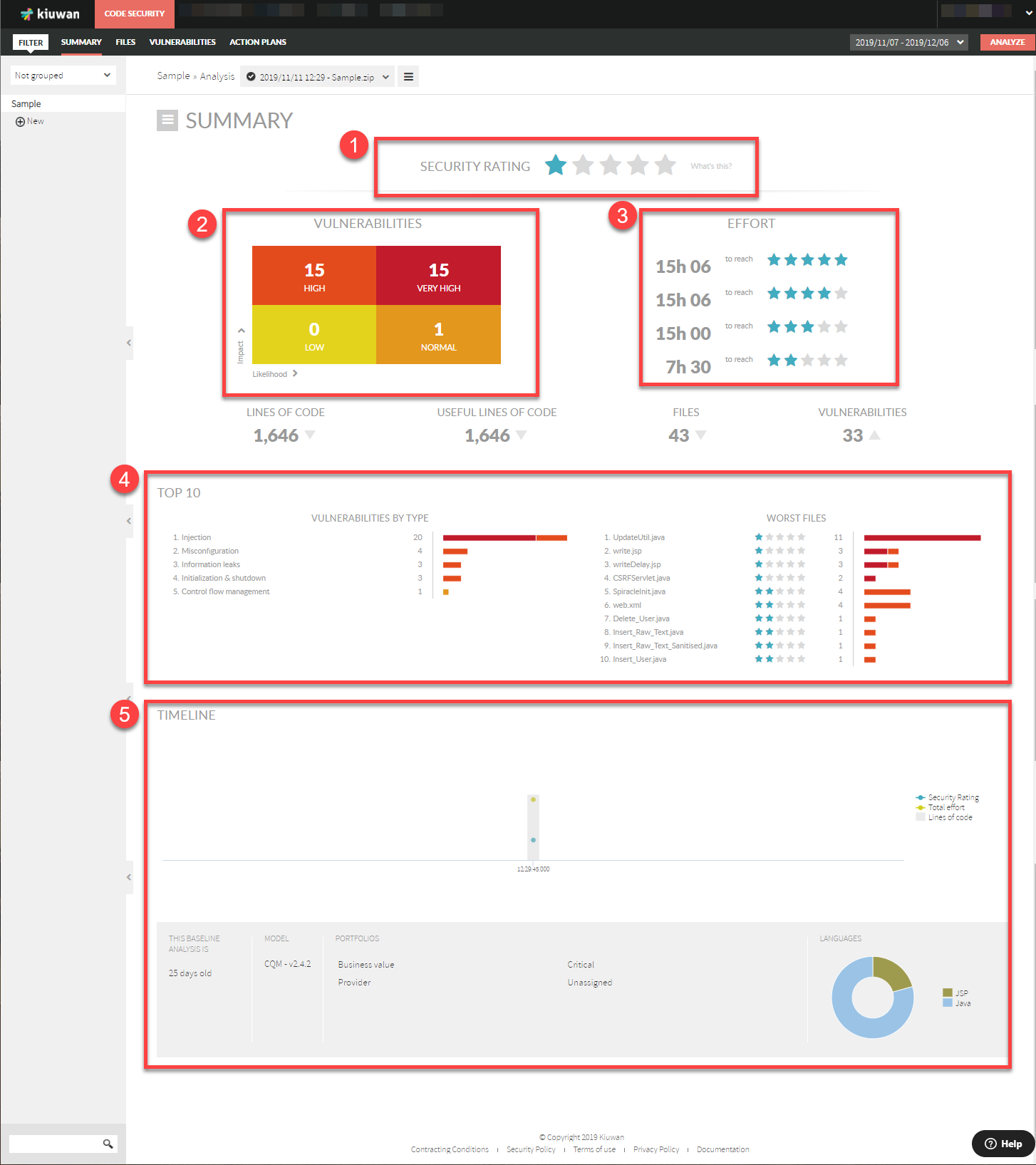 Image Added
Image Added
Security Rating
The Kiuwan Security Rating is a discrete 5-star grade rating that tells you how secure your application is in terms of the likelihood and impact of the found vulnerabilities.
This rating concentrates all the security evidences found in the source.
Image Modified
| Info | ||
|---|---|---|
| ||
Applications with 5 stars are considered to be secure, whereas those with 1 star are considered to be very insecure= secure 1 star = very insecure |
Security Vulnerabilities
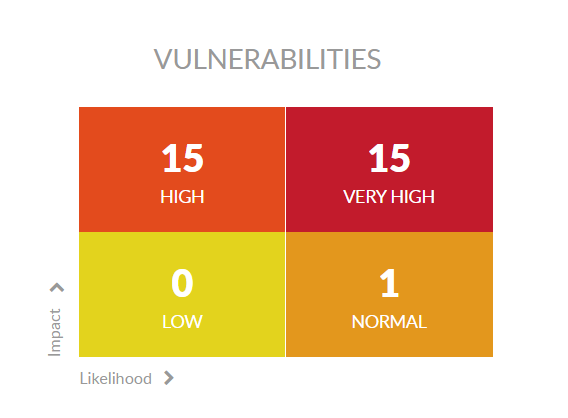 Image Added
Image Added
Security vulnerabilities are grouped in a quadrant according to two major axes:
- Impact of the vulnerability, according to the severity of the associated security risk
- Likelihood of the event that could cause the associated security breach
These two axes produce 4 quadrants. Kiuwan summarizes found vulnerabilities for each quadrant .
Image Removed
In this image, you can see that Kiuwan found 271 vulnerabilities and how kiuwan distributes them in the 4 quadrants:in the following way:
- Very High: both likelihood and impact are high
- High: likelihood is low but impact is high
- Low : likelihood and impact are both low
- Normal: likelihood is high and impact is low
Security rating is based on following:
This impacts the security rating mentioned above:
- Security Rating starts from 1-star (i.e. 0 is not considered) when there is at = at least 1 Very-High vulnerability vulnerability (high impact, high likelihood)
- 2-star rating when there is at = at least 1 High vulnerability vulnerability (high impact, low likelihood) and none of higher priority
- 3-star rating when there is at = at least 1 Normal vulnerability vulnerability (high likelihood, low impact) and none of higher priority
- 4-star when there is at = at least 1 Low vulnerability vulnerability (low likelihood, low impact) and none of higher priority
- 5-star when there are no vulnerabilities in = no vulnerabilities in terms of likelihood and impact for your application security
Effort
Based on the analysis' results, Kiuwan also calculates the Effort you you need to invest to reach the different rating levels according levels according to the remediation effort associated to fix each vulnerability.
 Image Added
Image Added
| Info |
|---|
Please note that Very Low vulnerabilites are discarded in the Security Rating algorithm and are not included in 4-quadrant image. That's the reason you could find that the total number of vulnerabilties in the 4-quadrant image is lower than the total vulnerabilities figure. To view detailed info on all the vulnerabilites, please go to Vulnerabilities page. |
Top 10 Vulnerabilities and Worst Files
Code Security Summary The summary dashboard also provides a Top-10 ranking of vulnerability types and worst files.
This way, you can easily concentrate on major contributors to current security rating.
Image Modified
Vulnerability Types
Moreover, any vulnerability found by Kiuwan is categorized according to its type:
- Buffer handling
- Control flow management
- Design error
- Encryption and randomness
- Error handling and fault isolation
- File handling
- Information leaks
- Initialization and shutdown
- Injection
- Misconfiguration
- Number handling
- Permissions, privileges and access controls
- Pointer and reference handling
- System element isolation
- Other
The Top-10 Vulnerabilities By Type graphic lets you to view which ones are the most frequent in your application, showing the total number of vulnerabilities for every type.
To view detailed info
Clickingon all the vulnerabilites, please go to Vulnerabilities page.
Click on the vulnerability type
you will be ableto see associated defects
(that link will forward you to Vulnerabilities page with the defects filtered by the selected type).If you want to see which vulnerabilities are checked by Kiuwan for every type, you should go to Model Management, select your model and click on Security Rulesin a new page.
 Image Added
Image Added
The Top-10 Worst Files graphic displays a ranking of the worst (low-rated) files of your application, showing the security rating and the number of vulnerabilities found.
Timeline
The Timeline section displays a historical a historical evolution of your Security Rating and Total Effort Effort (to reach 5-star rating) as well as the total LOC size of your application.
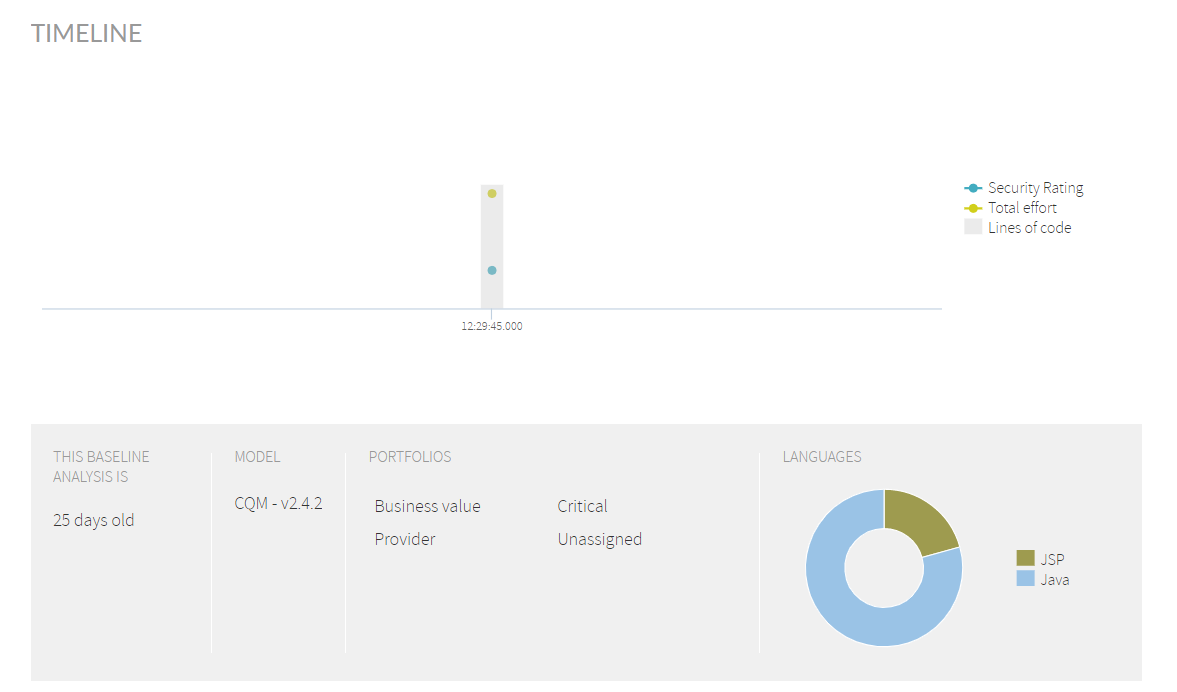 Image Added
Image Added
This section also displays information on:
- When a baseline analysis was performed (only applicable if you are using Life Cycle). If you are not using Life Cycle, that date will be current date of the analysis.
- Model used for the current analysis
- Portfolios this analysis belongs to
- Graphical distribution of LOCs in different languages