...
...
...
...
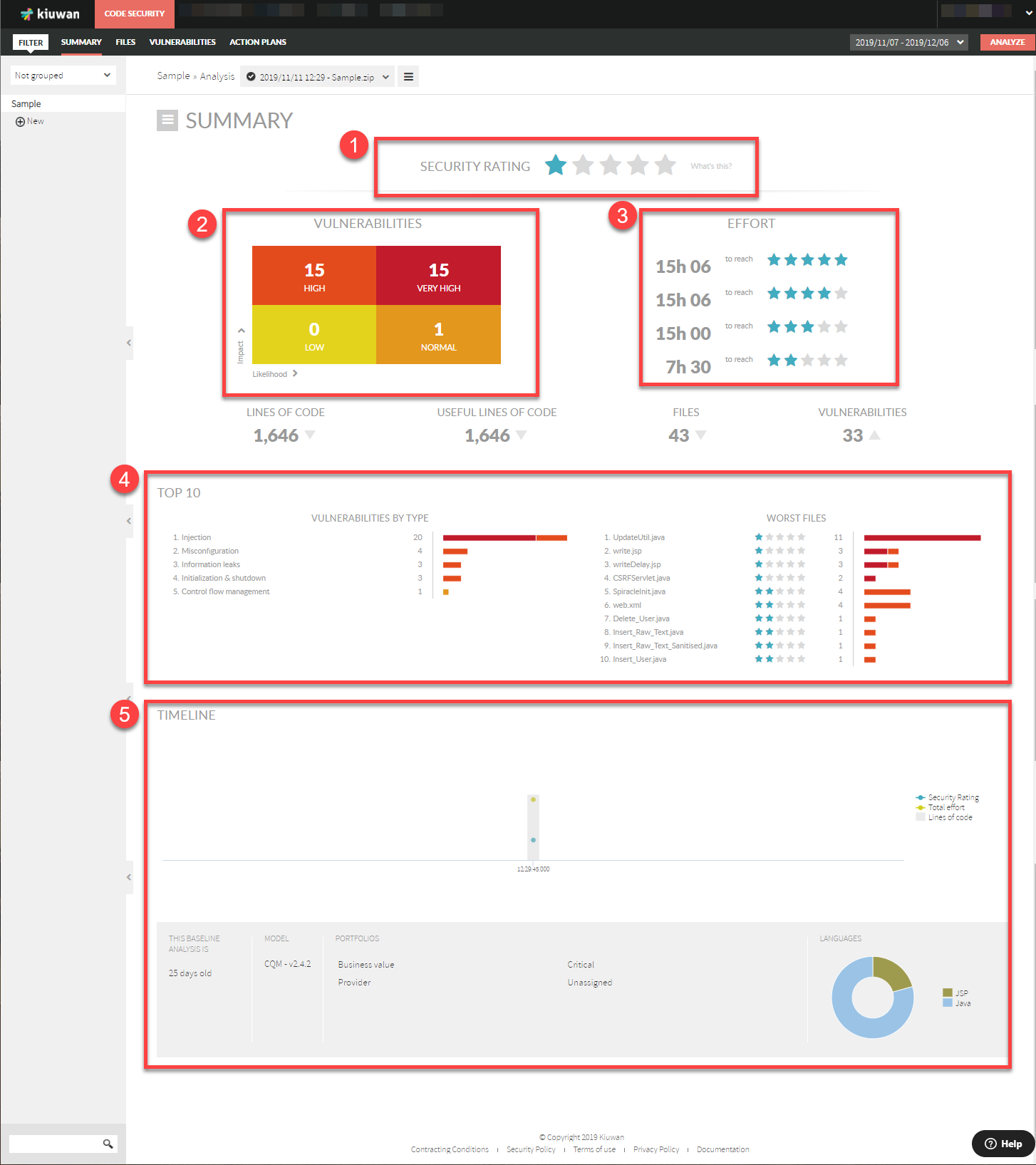
- Overall security rating,
- Vulnerabilities quadrant,
- Effort to reach upper levels of security,
- Top-10 security vulnerabilities,
- Top-10 worst files, and
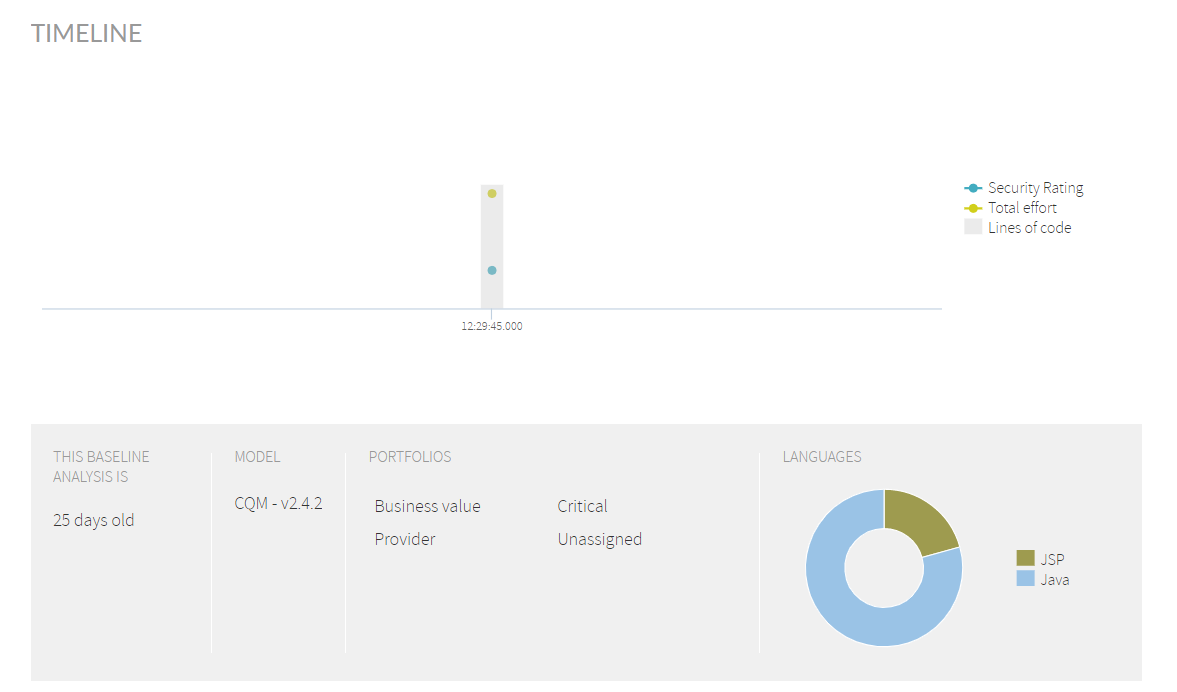
- Timeline evolution of security indicators
...
...
...
...
...
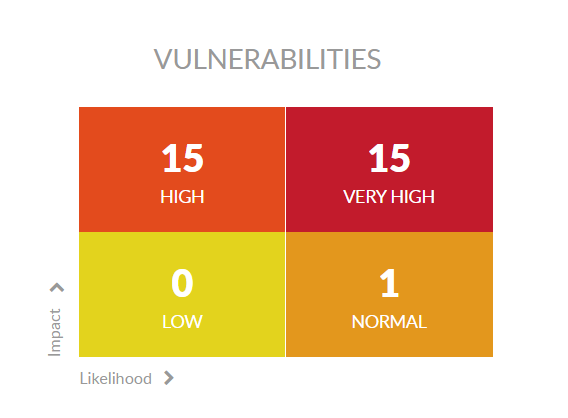
In this image, you can see that Kiuwan found 271 vulnerabilities and how kiuwan distributes them in the 4 quadrants:
...
...
...
...
...
...
Security rating is based on following:
...
...
...
...
...
...
...
...
...
...
...
...
...
...
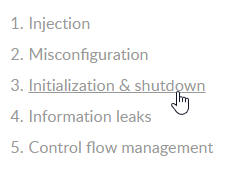
Any vulnerability found by Kiuwan is categorized according to its type:
- Buffer handling
- Control flow management
- Design error
- Encryption and randomness
- Error handling and fault isolation
- File handling
- Information leaks
- Initialization and shutdown
- Injection
- Misconfiguration
- Number handling
- Permissions, privileges and access controls
- Pointer and reference handling
- System element isolation
- Other
...
...
...
...
...
...
...