Versions Compared
Key
- This line was added.
- This line was removed.
- Formatting was changed.
Custom Components
Contents
| Table of Contents |
|---|
A customer will be able to add, modify, and delete custom components. Also, adding their own information about private vulnerabilities and licenses associated with custom components.
The customer can add components to Kiuwan, which may be custom or not. A custom component should be custom when the customer is the component owner or is a modification of the other public component.
For example a custom component may be:
- Group name: com.my.component
- Artifact name: component-core
- Version: 1.0.0
- Language: java
Required Permissions
Only users granted with Application Management permission are allowed to access Policies Management modules, add custom components, private vulnerabilities, or associate licenses to custom components.
How to manage components in Kiuwan Insights
You can manage components using the REST API defined below Insights Custom Components: https://static.kiuwan.com/rest-api/kiuwan-rest-api.html
Another way is through the Kiuwan website.
- Go to Insights Management in the setting menu.
 Image Removed
Image Removed Image Added
Image Added - Select CUSTOM COMPONENTSCustom Components.
 Image Removed
Image Removed Image Added
Image AddedBelow, the custom components administration in the Kiuwan website:
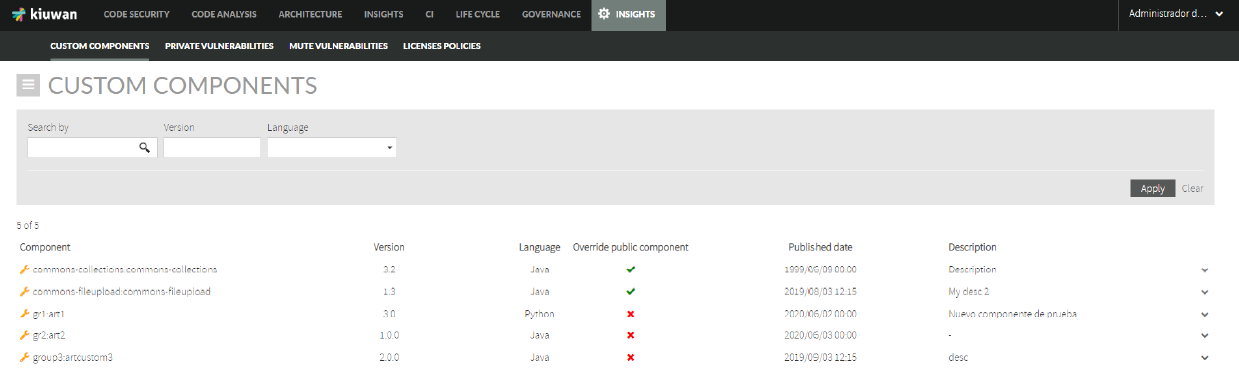 Image Removed
Image Removed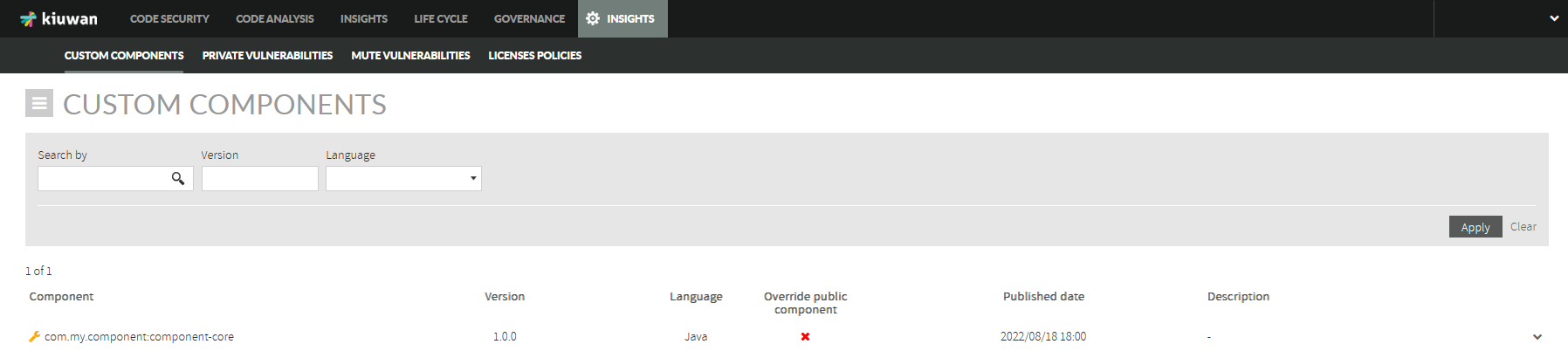 Image Added
Image Added - You can add new custom components by selecting Add Custom Component, located at the CUSTOM COMPONENTS Custom Components hamburger menu.
 Image Removed
Image Removed Image Added
Image Added - In the ADD CUSTOM COMPONENT Add Custom Component screen, fill the custom component data form.
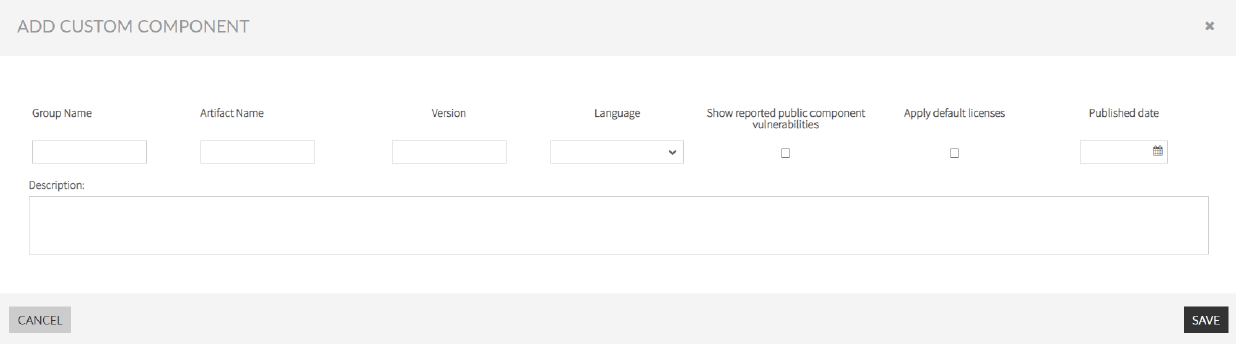 Image Modified
Image ModifiedNote The mandatory fields in the ADD CUSTOM COMPONENT form are "Artifact Name," "Version," "Language," and "Published date."
- Show reported public component vulnerabilities: If you check this option, the public vulnerabilities found by Kiuwan will be shown in the Kiuwan analysis that contains these components and the security risk will be calculated with these vulnerabilities and the private vulnerabilities.
- Apply default licenses: If you check this option the licenses found by Kiuwan will be shown in the Kiuwan analysis that contains these components and the license risk will be calculated with these licenses and the licenses associated by the customer.
- Click Save.
In the list of custom components you have the following actions:
- Remove custom attribute: Removes the custom attribute, but the component will still exist and the data could be replaced by the public data if the component is public.
- Modify custom data: Updates the custom components data.
- Modify licenses: Modify associated licenses to custom components.
- Delete component: This option is enabled if no public component with the same group name, artifact name, version, language exists. Also, if the component has not an analysis.
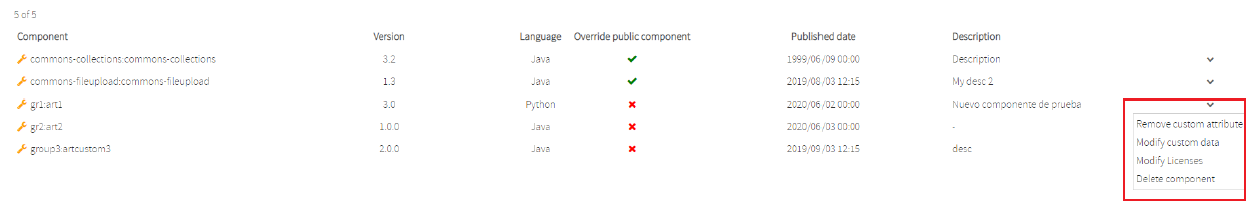
Remove custom attribute
This action removes the custom attribute, but the component will still exist and the data could be replaced by the public data if the component is public.
Modify custom data
The option “Modify licenses” modifies associated licenses to custom components. If you select this option a pop-up opens where you could modify the licenses associated to custom components.
Modify licenses
The option “Modify licenses” helps you modify associated licenses to custom components. If you select this option a pop-up opens where you can modify the licenses associated to custom components.
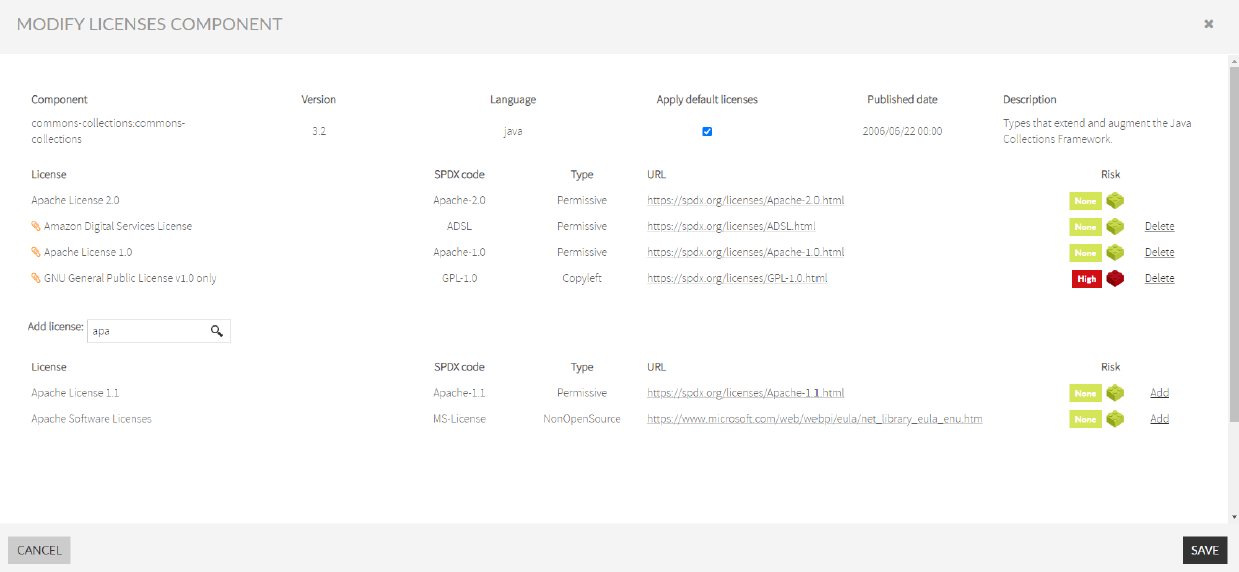
- You can delete associated licenses by the customer or add new licenses, and select if you want to apply for default licenses or not. To delete associated licenses you must click Delete located next to the Risk column.
- Search for new licenses in the Add license search box, and select the licenses by clicking Add located next to the Risk column.
- After you finished modifying the licenses component, click SAVE.
Delete Component
This option will be enabled if does not exist a public component with the same group name, artifact name, version, and language, and the component has not in an analysis
This option deletes the component and it will not appear in the obsolescence data for other components with the same group name, artifact name, and language.
How to manage private vulnerabilities in Kiuwan Insights
You can manage components using the REST API defined below Insights Custom Components: https://static.kiuwan.com/rest-api/kiuwan-rest-api.html
Another way is through the Kiuwan website.
You must go to Insights Management in the setting menu:
- Go to Insights Management in the setting menu.
 Image Removed
Image Removed Image Added
Image Added - Select Private Vulnerabilities.
 Image Modified
Image Modified
Below, the PRIVATE VULNERABILITIES administration in the Kiuwan website: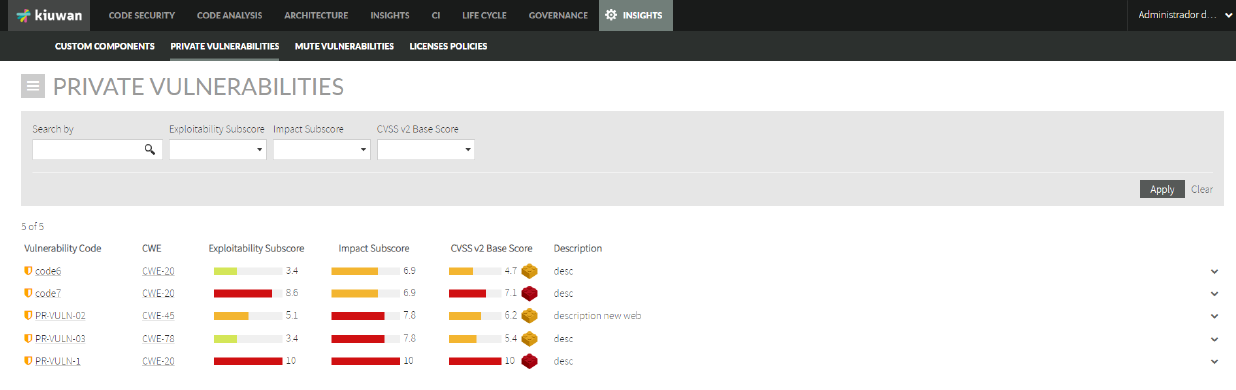 Image Removed
Image Removed - You can add new private vulnerabilities by selecting Add Private Vulnerability at the PRIVATE VULNERABILITIES Private Vulnerabilities hamburger menu.
 Image Removed
Image Removed Image Added
Image Added - In the ADD PRIVATE VULNERABILITY Add Private Vulnerability screen, fill the private vulnerability data form.
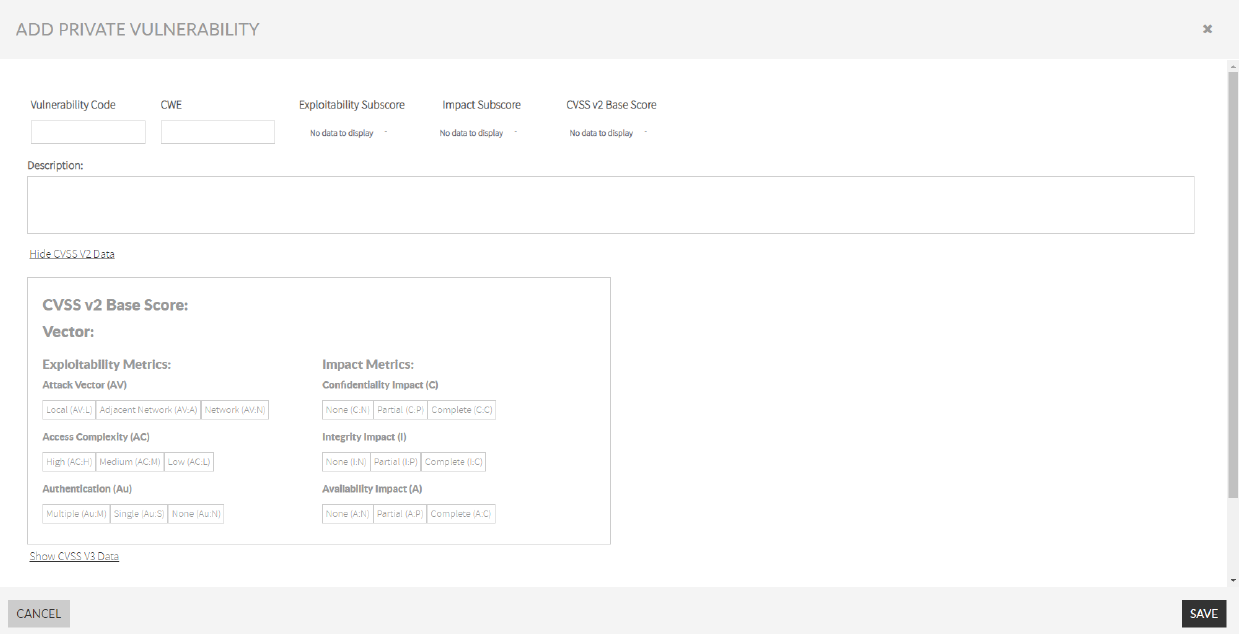
Vulnerabitlity Vulnerability code (Mandatory, CWE, and Description): The vulnerability code must be unique. The sub-score and score data will be calculated from CVSS v2 section. Image Modified
Image Modified
CVSS v2 section: You can inform the CVSS v2 attack vector for the current private vulnerability.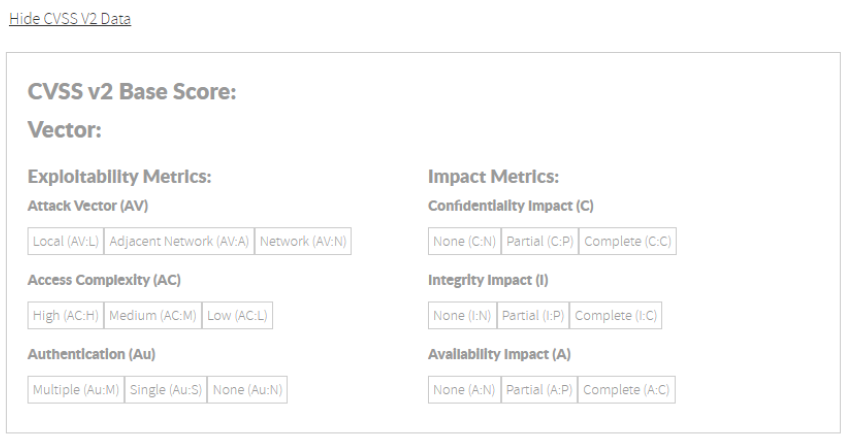 Image Modified
Image Modified
When you select all the data, the score and sub-score are populated.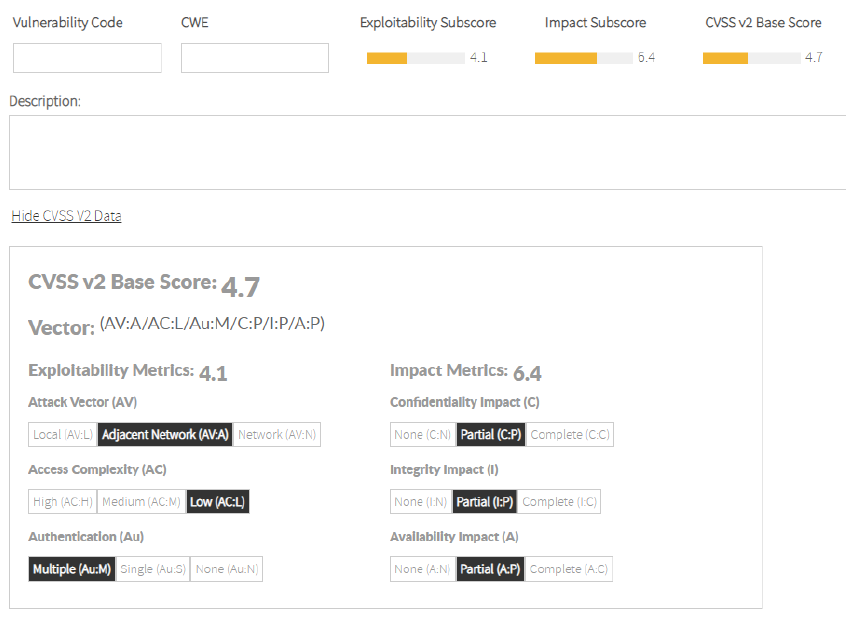 Image Removed
Image Removed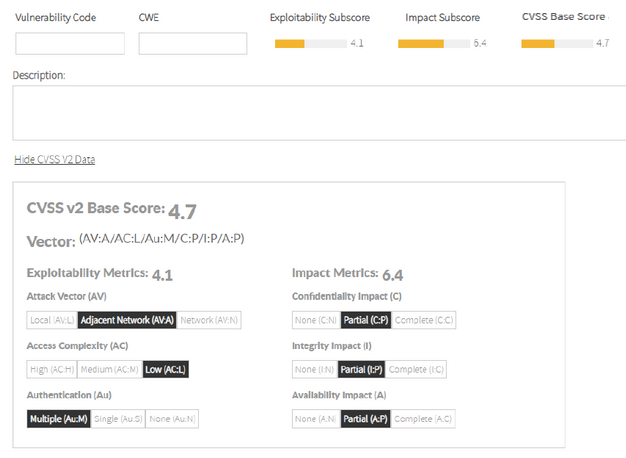 Image Added
Image AddedCVSS v3 section: You can inform the CVSS v3 attack vector for the current private vulnerability.
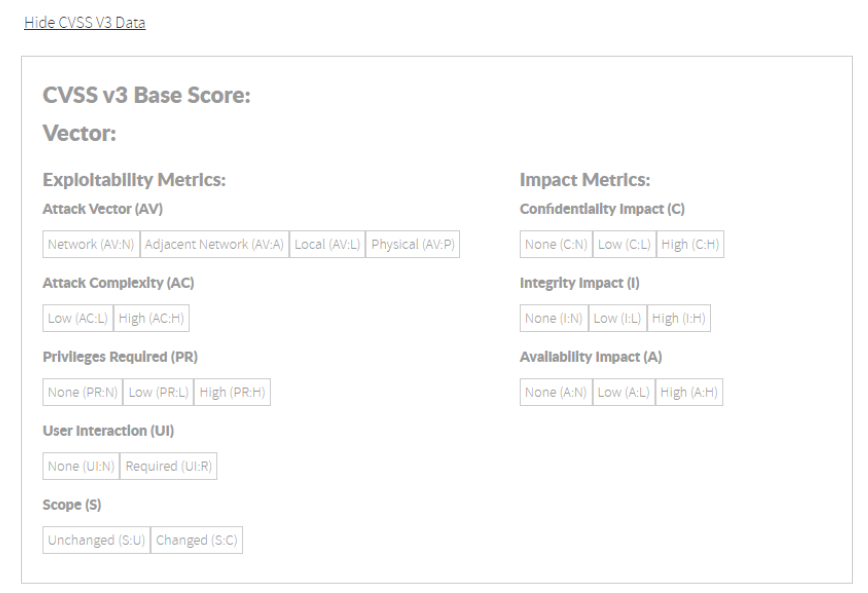 Image Modified
Image Modified
Affected components and versions:
a. Click Add Component to add a new affected component.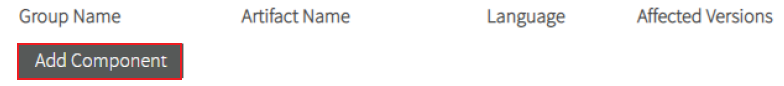 Image Modified
Image Modified
b. Fill the component information in the avaiable fields. Below, you will find more information of how to fill the Affected Versions.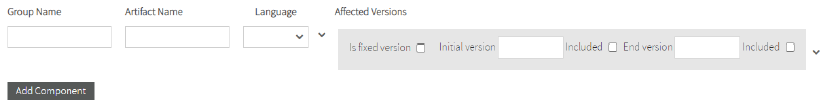 Image Modified
Image Modified
Take into account that the Artifact Name and Language fields are mandatory.
The affected versions can be fixed versions or range versions:
- Fixed Version: You must check the Is fixed version checkbox and enter the Field version.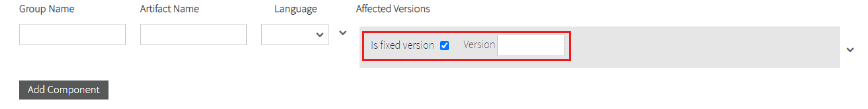
- Range Version: You must uncheck the Is fixed version checkbox and enter the Initial version.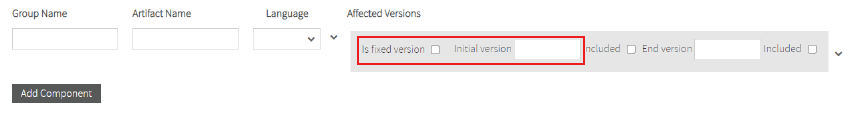
If the initial version is included you must check the Included checkbox.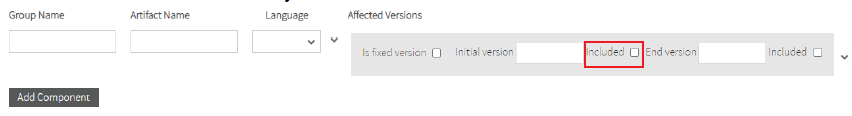
If the private vulnerability affects all versions from the initial version you must leave the End Version field empty.
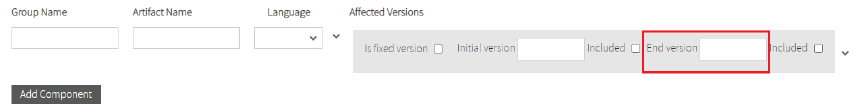
If the private vulnerability has end affected version, fill the End version field and if the end version is included in vulnerable versions you must check the Included checkbox.
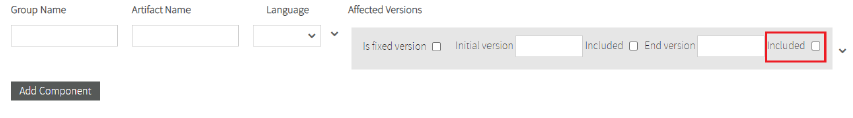
You can add Affected version or Delete affected component.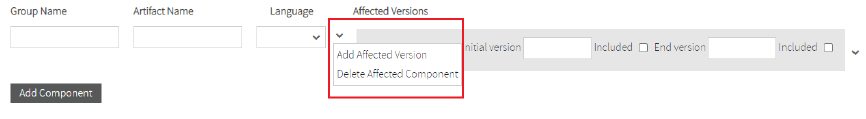
If you select Add Affected Version a new affected version for this component will display.
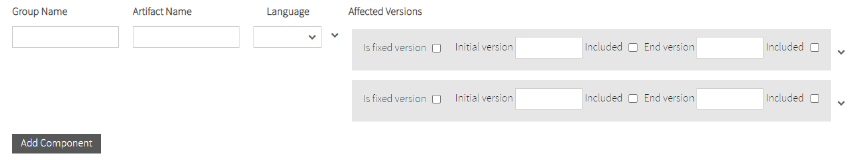
Also, you can Delete affected versions.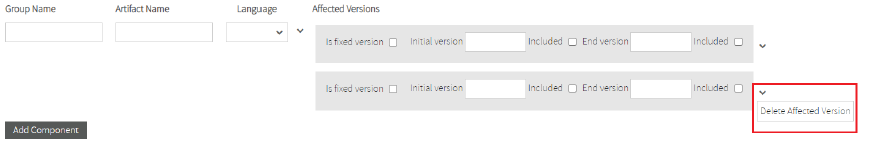
- After completing to configure your private vulnerability information, click SAVE.
In the list of private vulnerabilites you have the following actions:
- Modify vulnerability
- Delete vulnerability
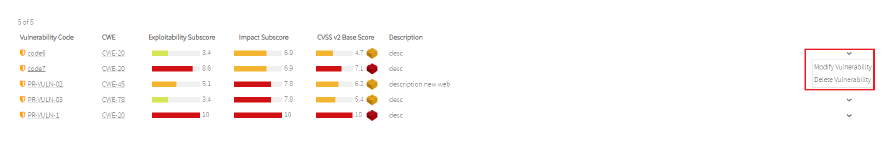 Image Removed
Image Removed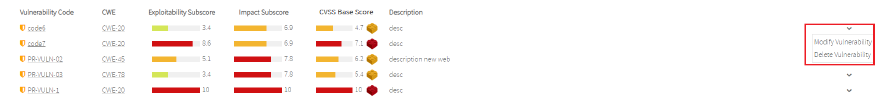 Image Added
Image Added
Edit custom components, private vulnerabilities, and licenses associated to custom components by the customer
Insights Components
Next to the custom components, the following icon ![]() is displayed. Also, the following risks are displayed depending on the custom data:
is displayed. Also, the following risks are displayed depending on the custom data:
- Obsolescence risk: Depends on the component date and other custom components with the same group name, artifact name, and language.
- License Risk: Depends on the licenses found by Insights for this component, if you have checked this option, and the associated licenses by the customer.
- Security Risk: Depends on the vulnerabilities found by Insights for this component, if you have been checked this option, and the private vulnerabilities affecting this component.
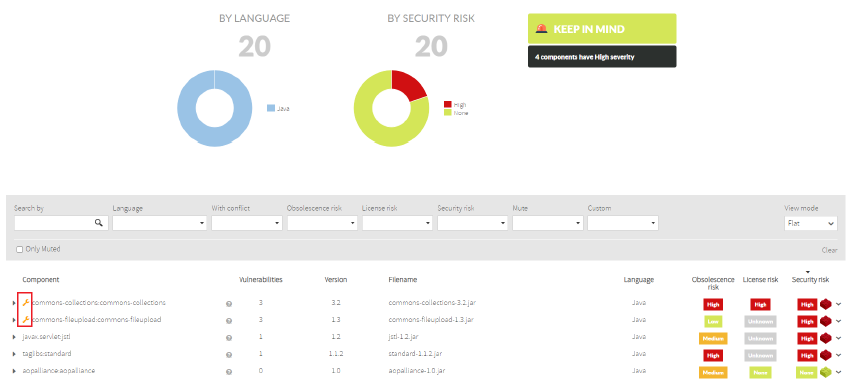 Image Modified
Image Modified
Also, you can filter by Custom components:
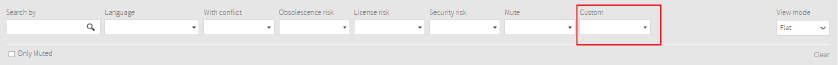 Image Modified
Image Modified
The associated licenses are represented by the![]() icon.
icon.
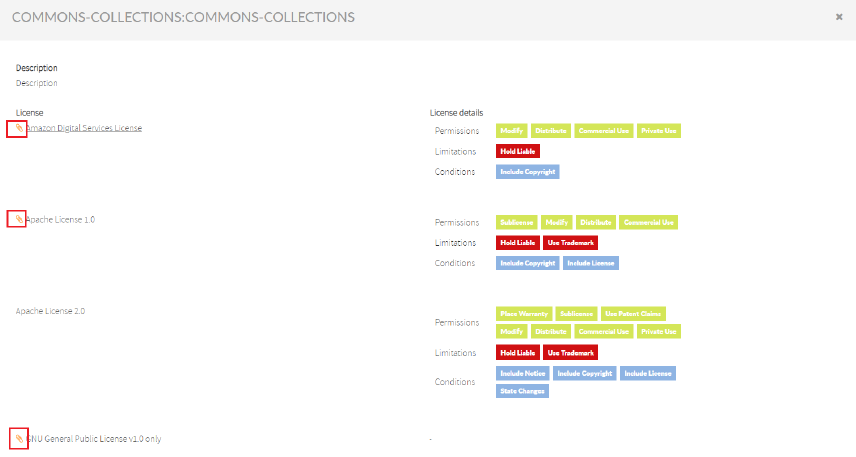 Image Modified
Image Modified
And the private vulnerabilities that affected this component are represented by the ![]() icon.
icon.
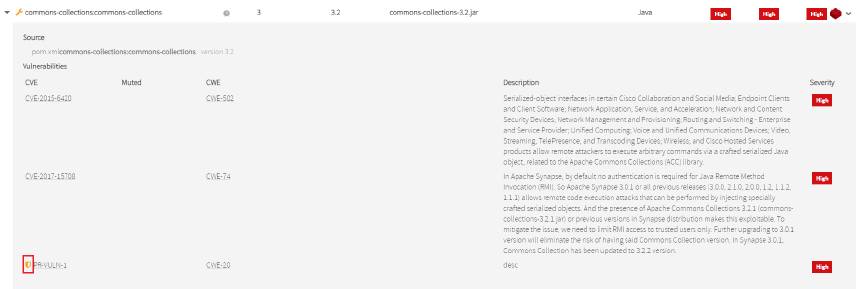 Image Modified
Image Modified
Insights Obsolescence
Next to the custom components, the ![]() icon is displayed. Also, obsolescence risk depends on the custom data:
icon is displayed. Also, obsolescence risk depends on the custom data:
- Depends on the component date and other custom components with the same group name, artifact name, and language.
If the component is a copy of another public component when you display the drill-down you can see the public data for this component:
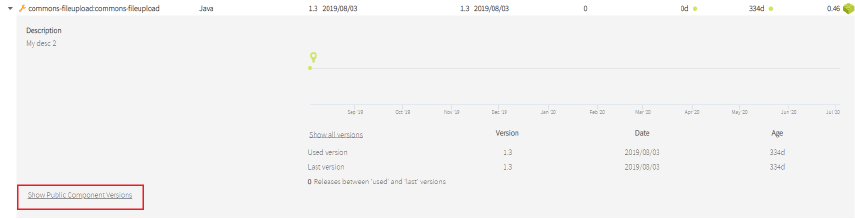 Image Modified
Image Modified
You can see the timeline for the public component:
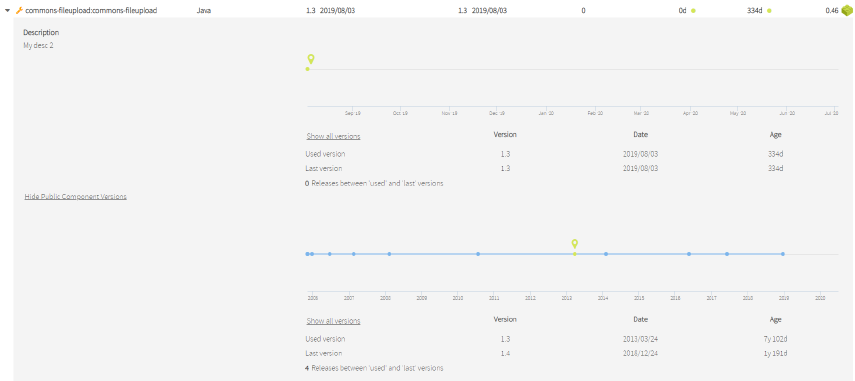 Image Modified
Image Modified
Also, you can filter by Custom components.
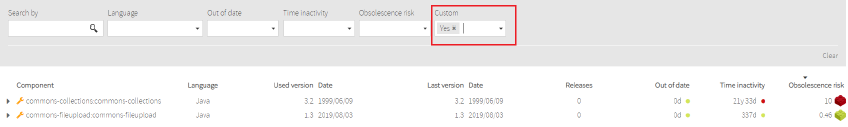 Image Modified
Image Modified
Insights Licenses
The custom components with licenses associated by the customer have the ![]() icon next to the component name:
icon next to the component name:
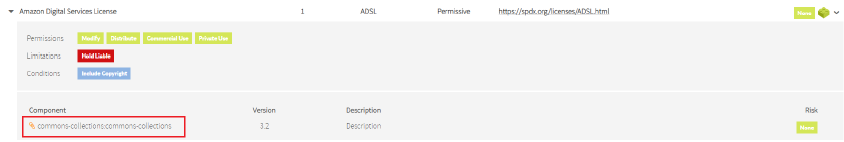 Image Modified
Image Modified
Insights Security
The private vulnerabilities have the ![]() icon next to the vulnerability name.
icon next to the vulnerability name.
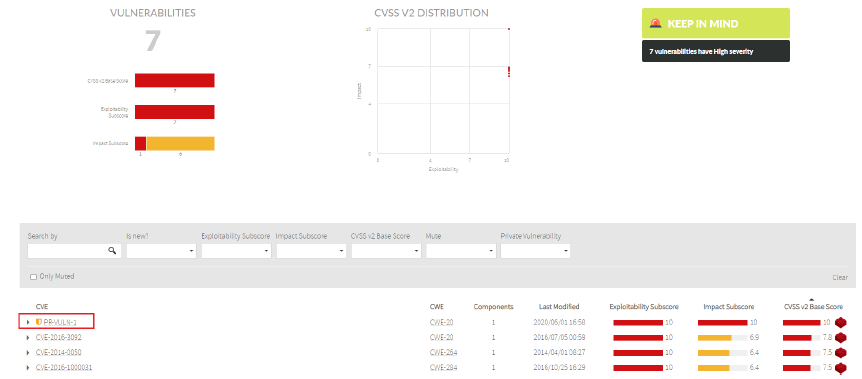 Image Modified
Image Modified
Also, you can filter by Private Vulnerabilites:
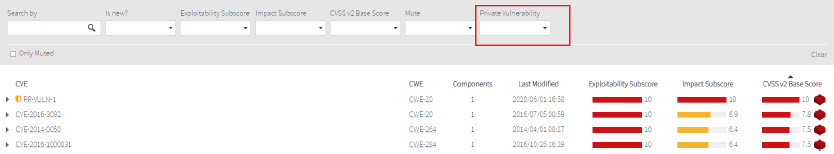 Image Removed
Image Removed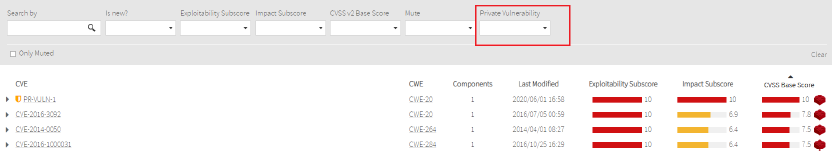 Image Added
Image Added
The custom components affected by private vulnerabilities displays ![]() next to the component name:
next to the component name:
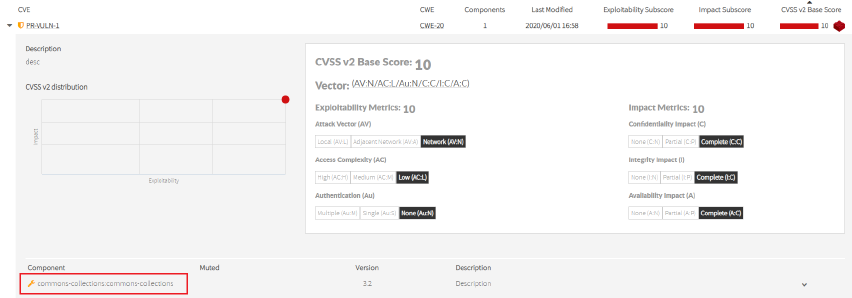 Image Removed
Image Removed
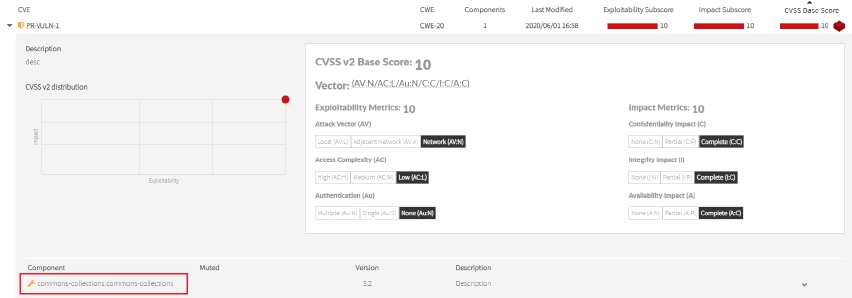 Image Added
Image Added