...
Contents:
| Table of Contents |
|---|
Web Browser Single Sign-On
When configured, a Kiuwan user can authenticate against an OAuth/OIDC server, and access Kiuwan resources.
...
Before the user can start using Web Browser SSO flow, the administrator of the OpenID Provider in their organization must first have registered Kiuwan as a Relying Party, and subsequently, the account owner of the Kiuwan user account must have registered their OpenID Provider in Kiuwan.
Configuring OpenID Provider
The following describes how to setup Kiuwan as a registered application on Azure ADFS, any other OAuth2.0/Open ID Provider with a similar configuration.
...
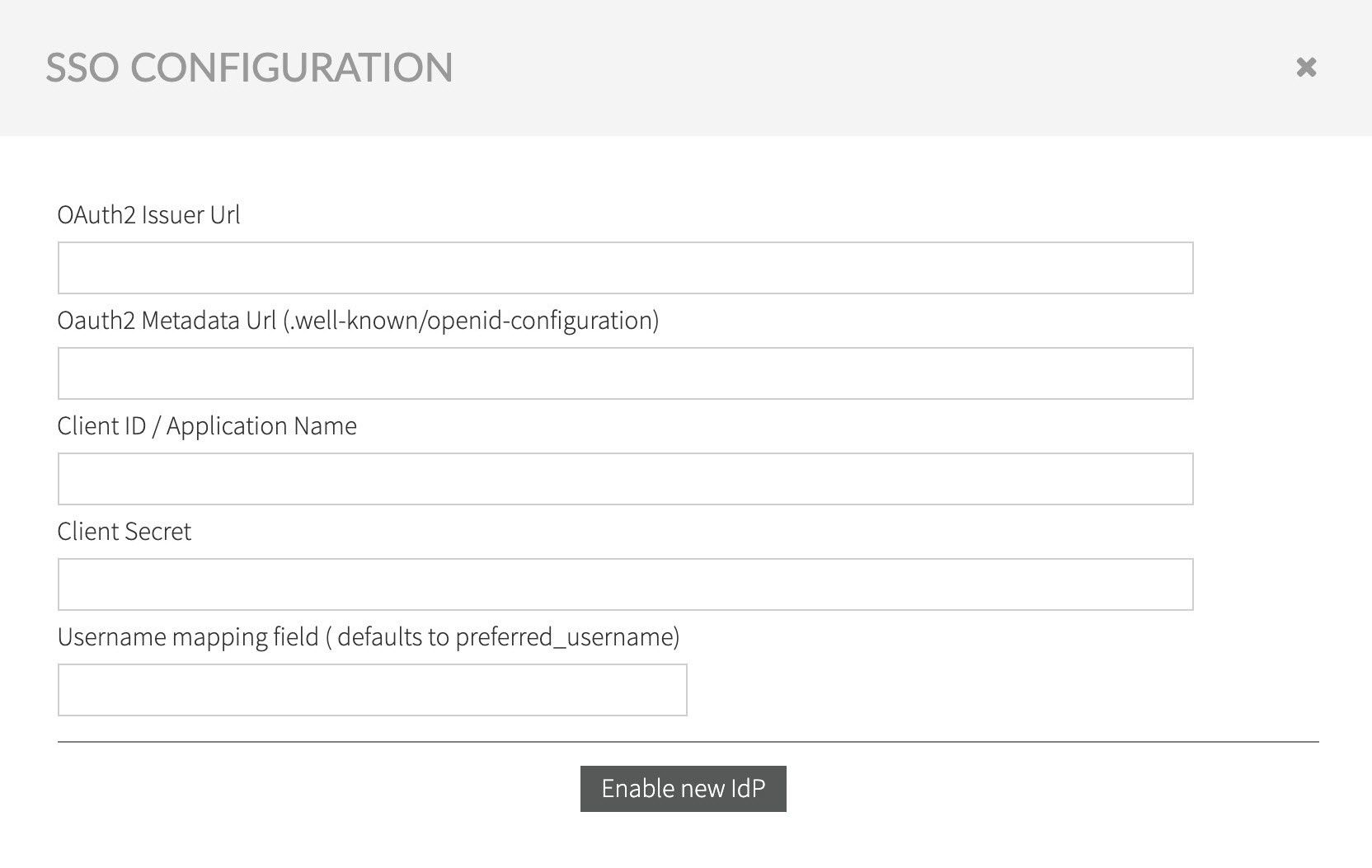
- URL of the issuer: The base URL provided by the OAuth provider that will be used for authentication and exchange of tokens.
- OIDC Metadata URL: e.g. .well-know/opendi-configuration URL while not mandatory by OpenID connect standard, the auto-configuration enables clients to derive all server configuration.
- Application ID: The name of the Kiuwan application as registered in the Oauth2.0 / OIDC Server.
- Client Secret: Kiuwan OIDC Client demands encrypted tokens, so a client secret, produced by the Oauth2.0/OIDC Server must be provided.
- The username mapping: The name of the OAuth/OIDC token field that enables Kiuwan to obtain the corresponding user in Kiuwan. For instance, if a user email is used to define the Kiuwan username, then the user mapping could be “e-mail”. Any other field described by the Oauth/OIDC server claims can be used, as long as the resulting value matches the Kiuwan user. It is common for the issuer server to include in the authentication token the field preferred_username, which usually maps to the username in the Identity Provider OAuth issuer.
In Azure AD, preferred_username matches the Unique Principal Name, e.g. the unique username of the identity within the AD definition.
Registering Kiuwan as an Oauth/OIDC client in Azure AD
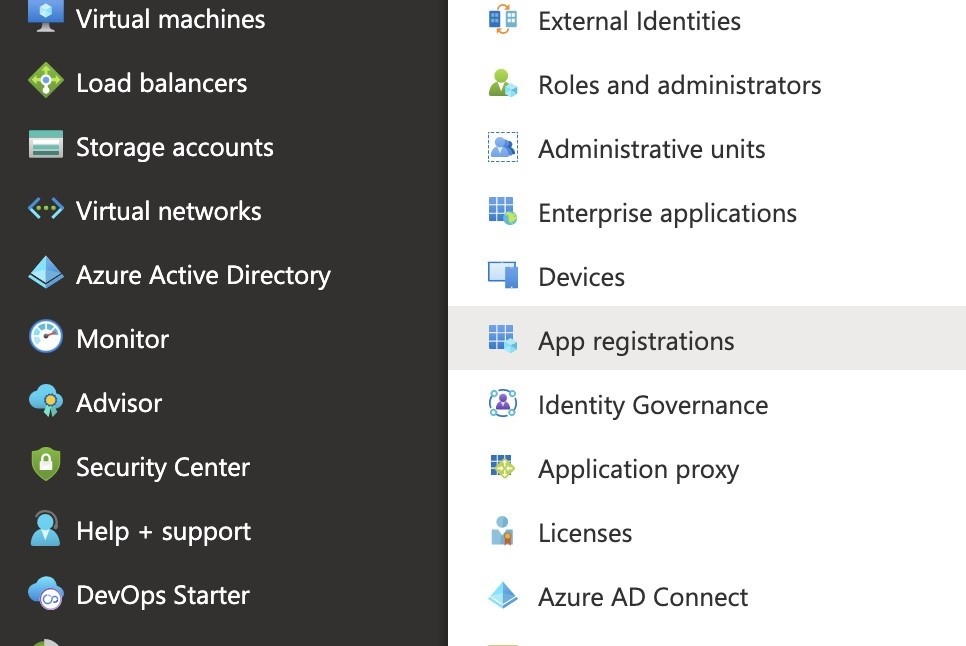
- Login to your Azure Portal and navigate to Active Directory > App Registrations.
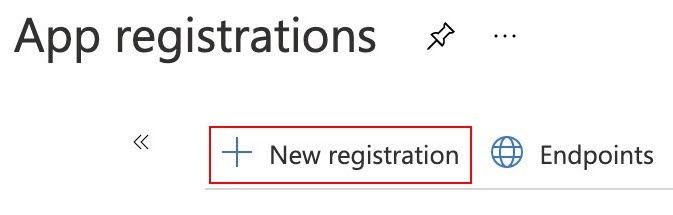
- Select New registration.
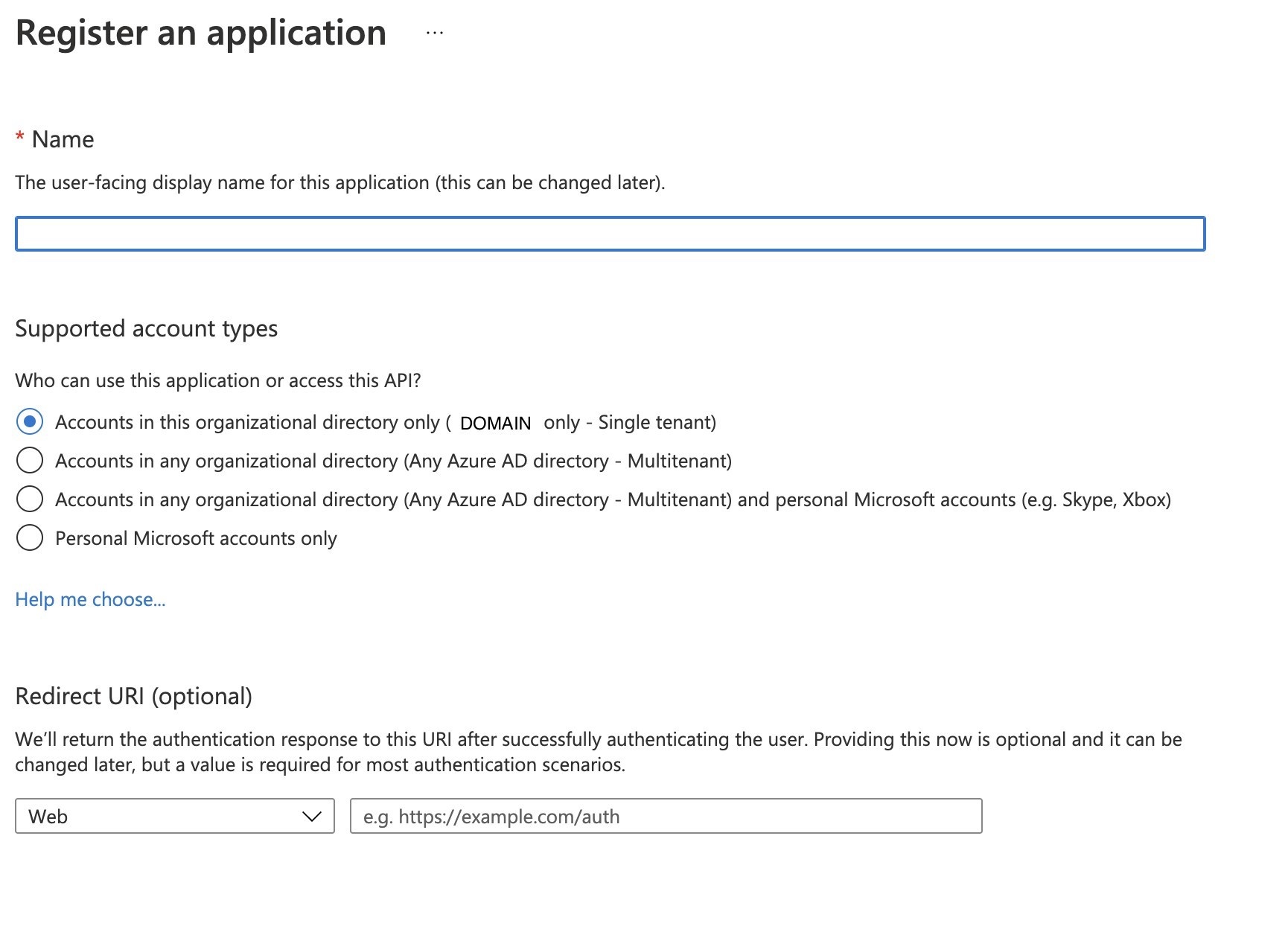
- Fill in the required information
- Configure the Redirect URI as follows:
- Add the following URI as the redirect URI: https://www.kiuwan.com/saas/oidc/auth
- The endpoint OAuth2/OIDC server will redirect, within the Kiuwan server, after the successful authentication of a specific user.
- If you have a local installation of Kiuwan, instead of www.kiuwan.com enter the corresponding URL, or IP address, of the local Kiuwan server.
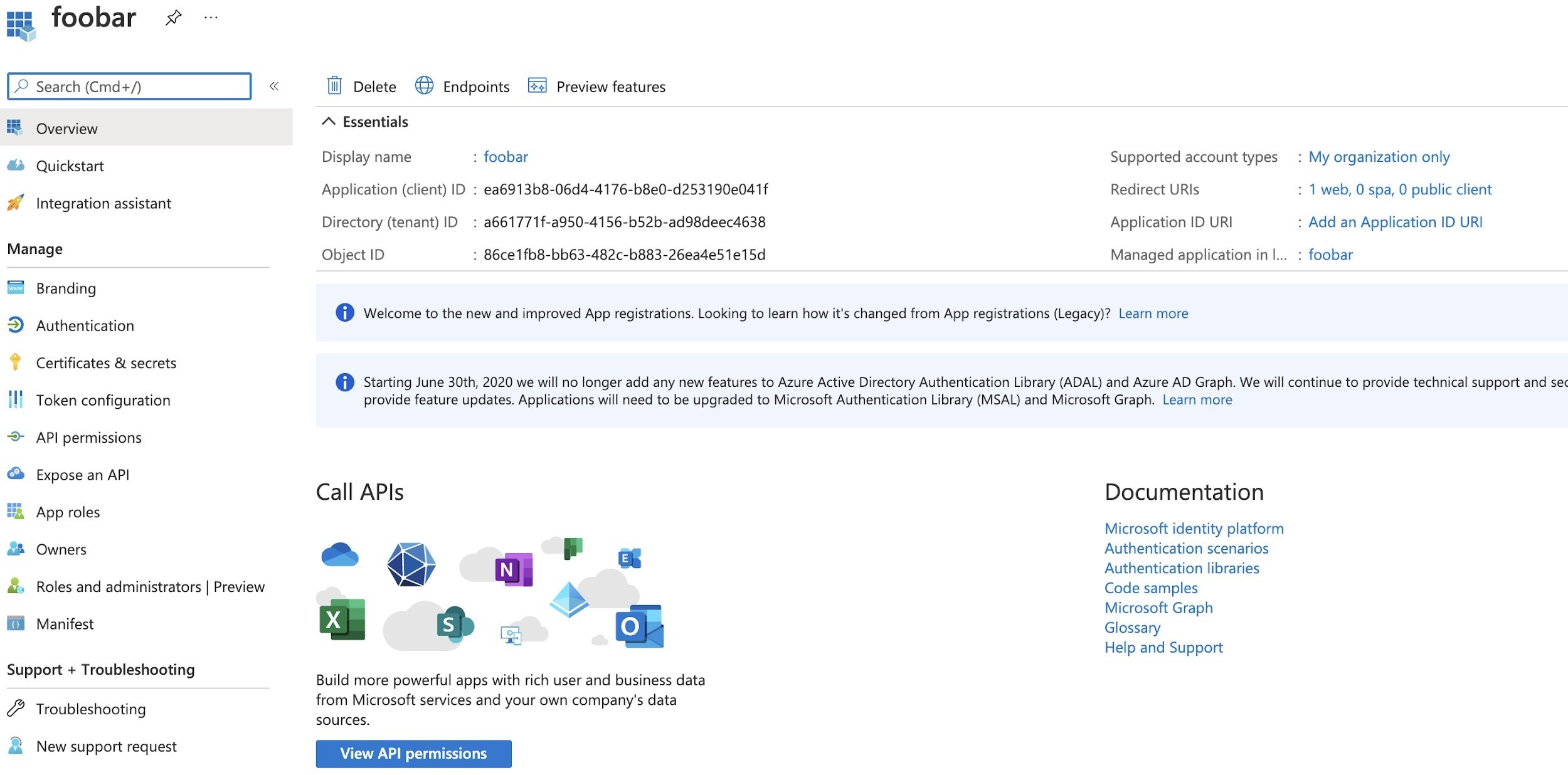
- After defining this Application Registration, the following is obtained:
- Configure Client Secret.
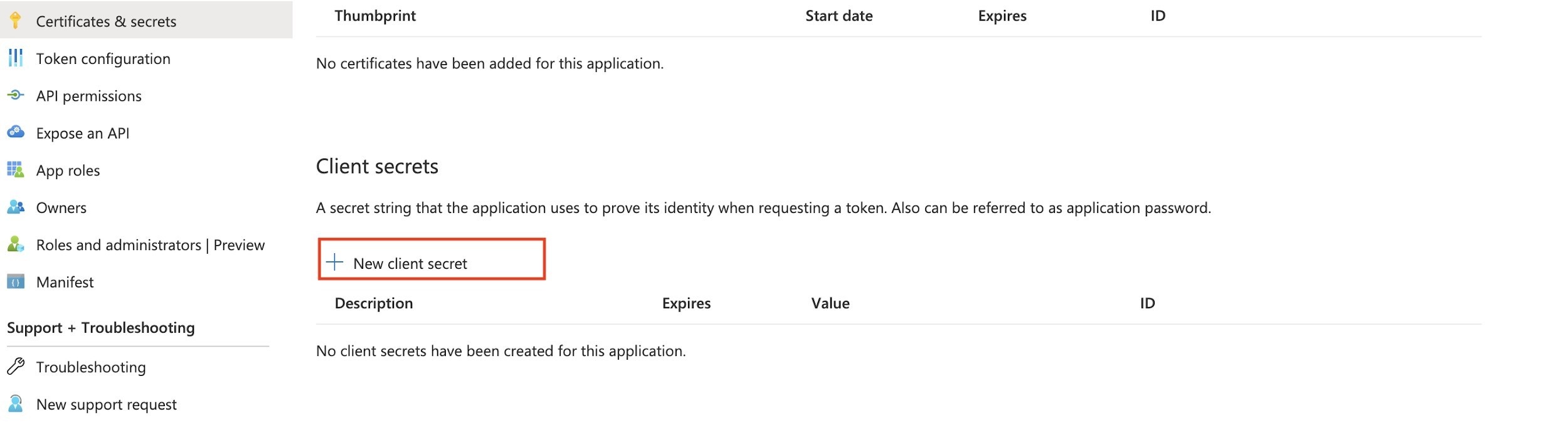
- After creating the registration, select the Certificates & Secrets option, and New Client Secret.
- Enter the needed values and click Add.
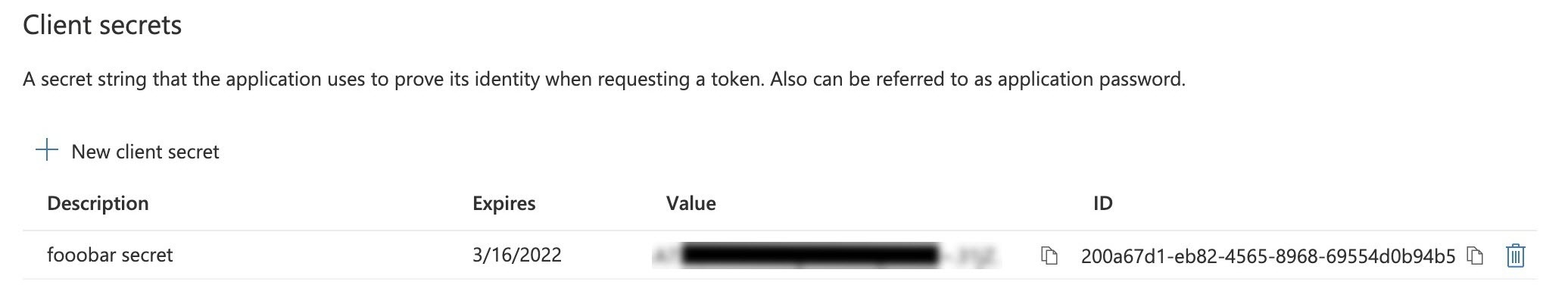
- A new secret for this Client Application ID is generated.
Copy this value to a temporary location as it will be needed later and after the screen is closed the access to the secret value is lost. Ideally, paste it directly into the OAuth/OIDC configuration at Kiuwan described in the next chapter.
- After creating the registration, select the Certificates & Secrets option, and New Client Secret.
...
Additionally, you would also need to collect the following endpoints:
Registering Kiuwan as an OAuth/OIDC client in Windows ADFS 2016
Similar to Azure DevOps, as with any other OAuth/OIDC issuer or identity provider, the configuration of ADFS follows the specifics defined for that Idp. However, information needs to be collected during the setup of Kiuwan as a registered app, as detailed in section Summary:
...
As stated, the application group and corresponding client are now configured.
Registering Kiuwan as an OAuth/OIDC client in OKTA
To use OKTA as an OAuth SSO identity provider, it is required to register Kiuwan in OKTA.
...
OKTA allows for additional configuration and provides extensive support, make sure you tailor the configuration to your needs.
| Anchor | ||||
|---|---|---|---|---|
|
To set up Kiuwan SSO with OAuth/OpenID connect follow these instructions:
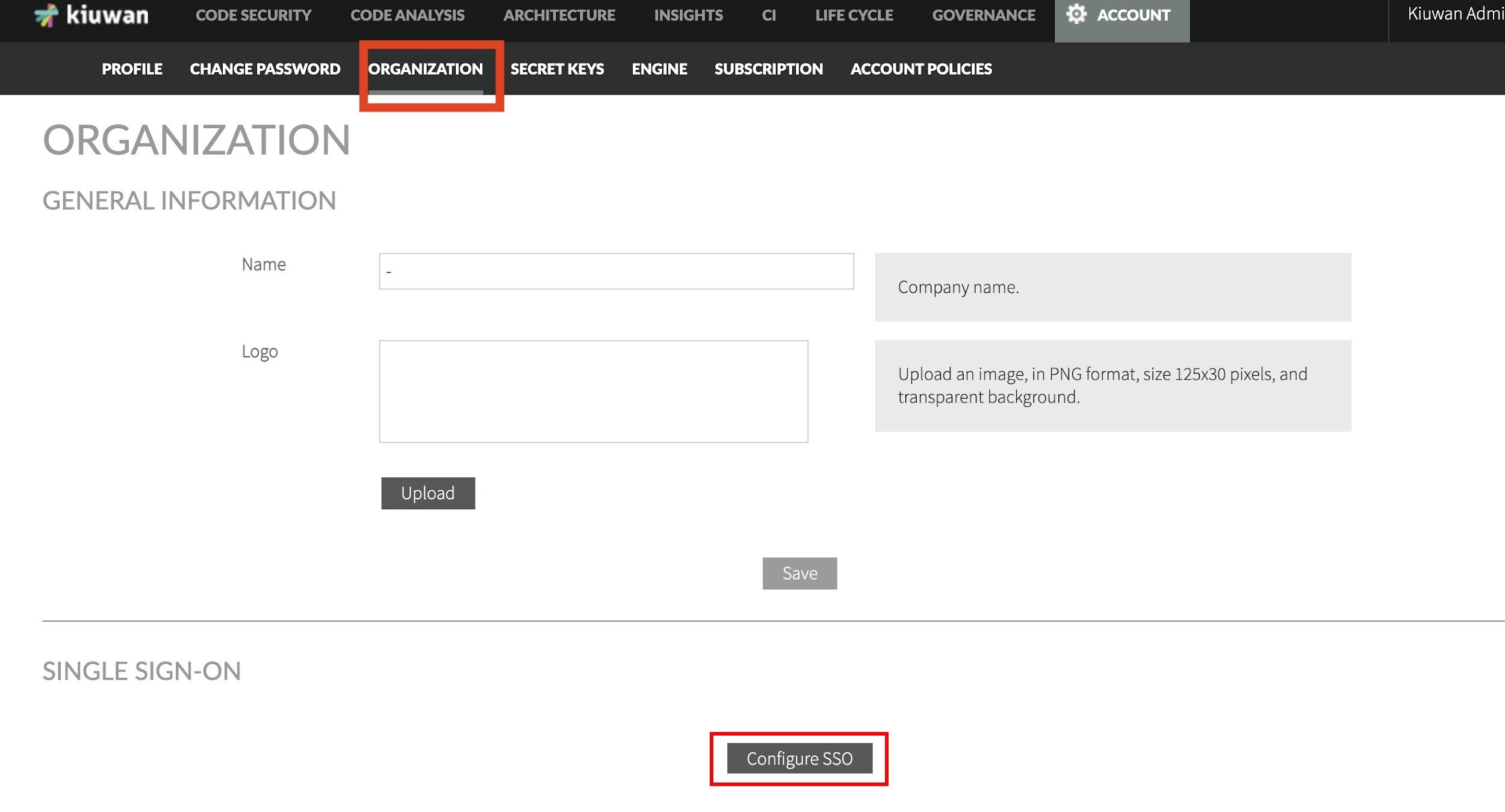
- As Account Administrator open the Account Management section:
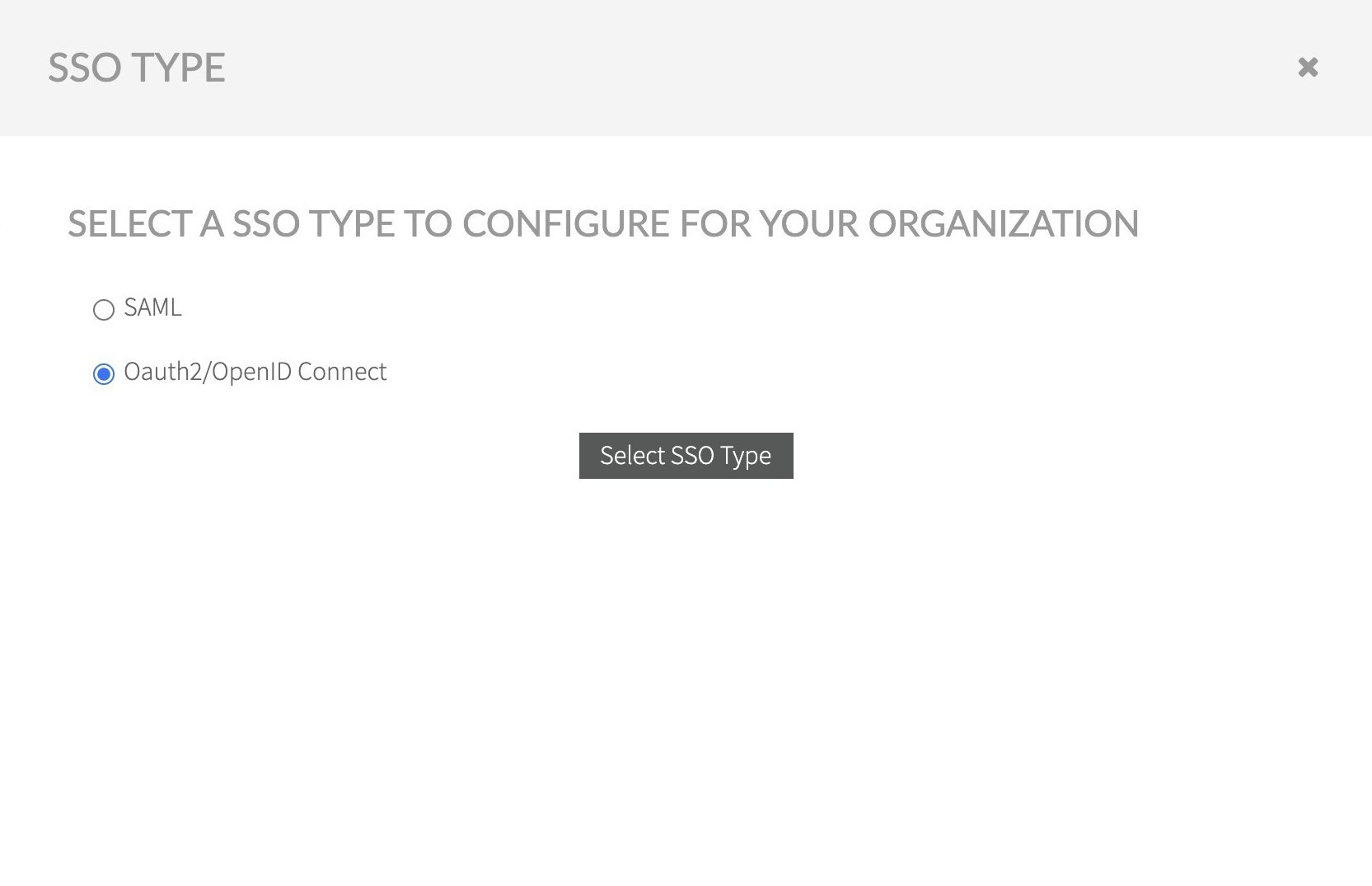
- In the Organization tab select Configure SSO option.
Select OAuth2/OpenID Connect option and confirm.
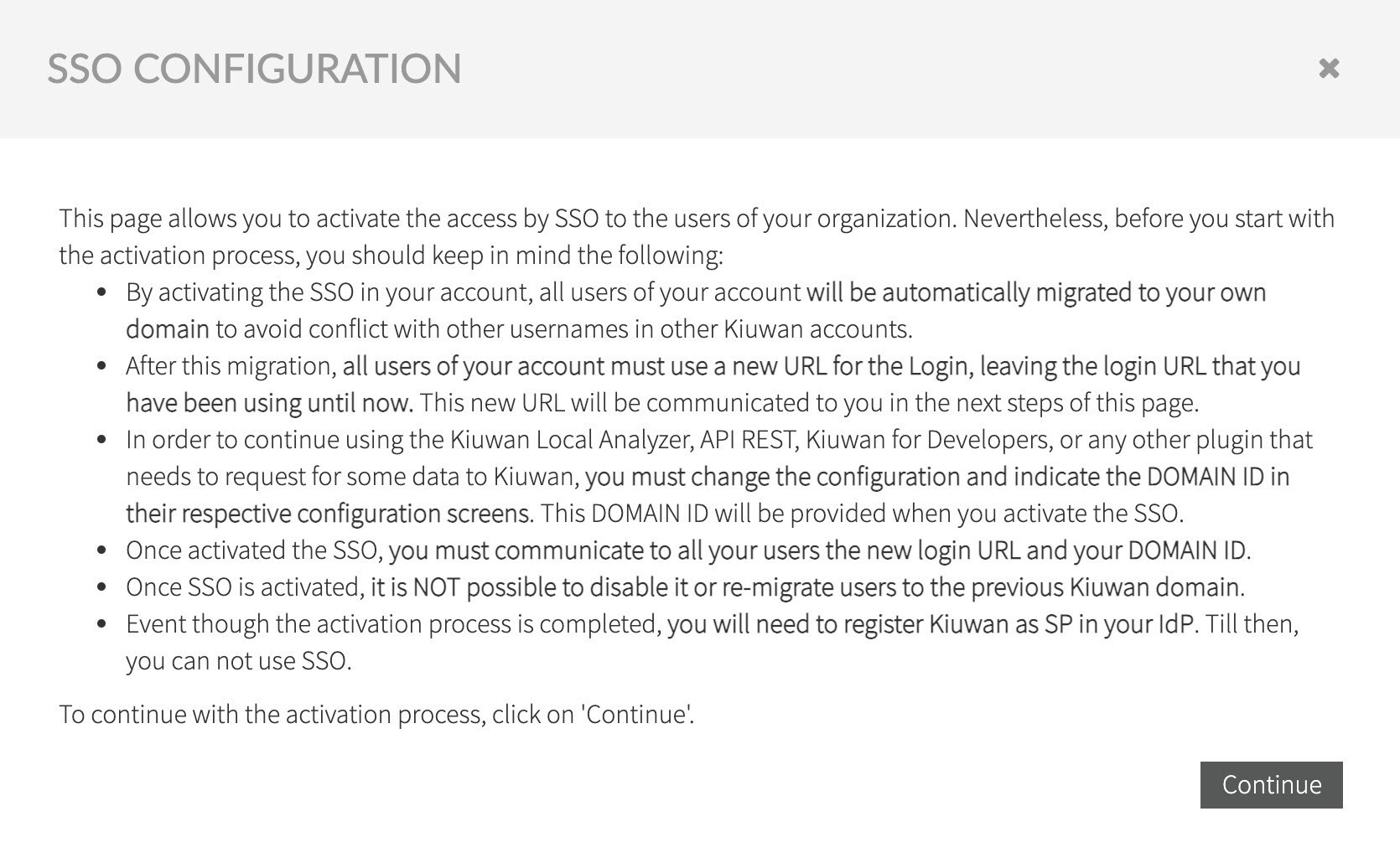
Read the following text explaining the implications when activating SSO, click Continue to proceed to the OAuth2/OpenID Connect setup.
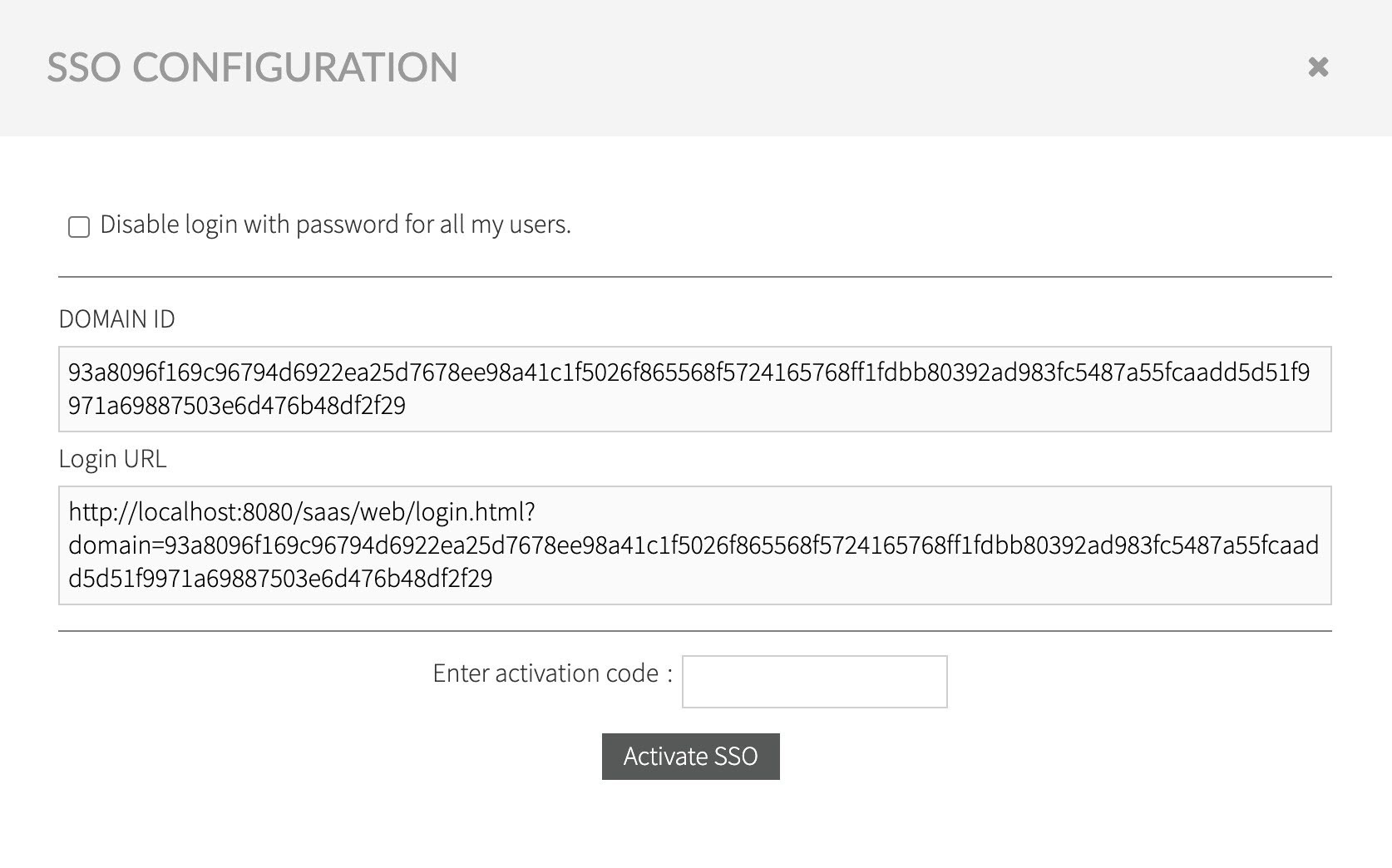
Fill in the information, as gathered during Configuring OpenID Provider, and confirm entered data by selecting Enable new IdP.
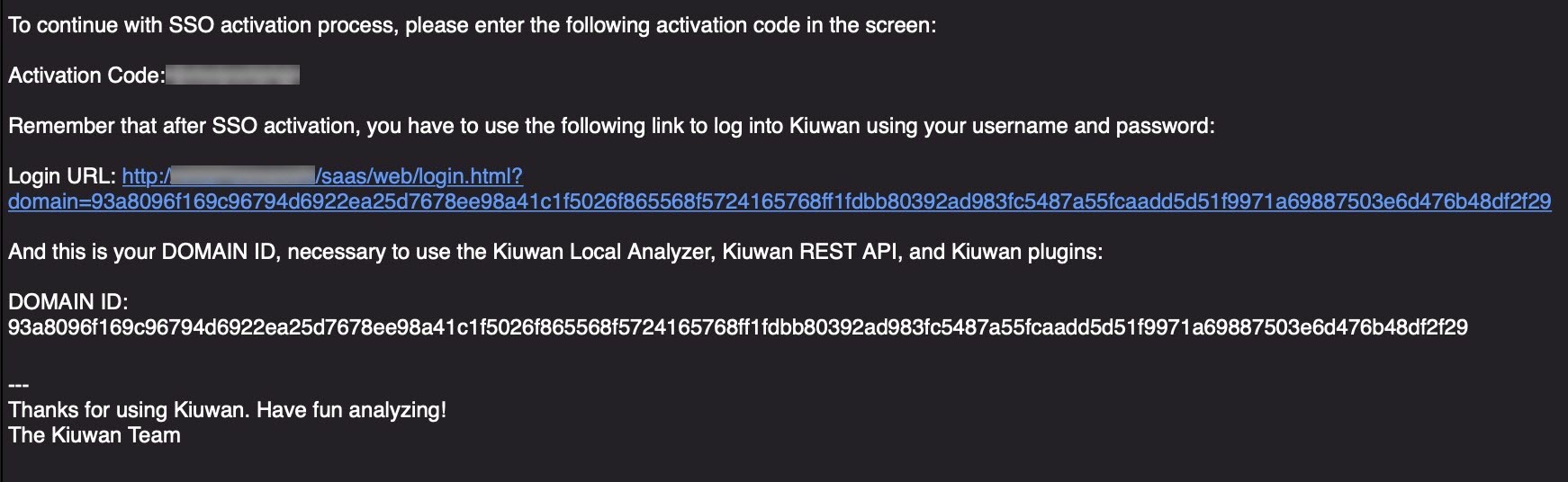
After confirming the SSO data, a new email is sent with the activation confirmation code, alongside the instructions explaining how to log in to Kiuwan after the SSO is activated.Copy the confirmation code and enter it in the confirmation form.
Note When the option Disable Login with password for all my users is checked, it prevents any user registered in your account, with the exception of Account Owner user, to be able to login using Kiuwan managed identity username/password.
Users will be able to log in only through defined OAuth/OIDC server authentication.
After entering the activation code a confirm the activation of SSO, the following confirmation dialogue displays:
Login to Kiuwan after OAuth SSO is activated
As explained in the confirmation email received during the configuration process, and as shown, after SSO setup in the Organization tab in the Account Management section, after SSO is completed the login must comply with the following URL:
...
Successful authentication will enable access to Kiuwan, with the corresponding authorization configured for the logged-in user.
Login in with Kiuwan defined username and password
When the user is configured to login with Username and Password in Kiuwan, as shown below:
...
In either case, after setting up SSO, the domain must always be set during the authentication process, otherwise, Kiuwan will not be able to identify the corresponding user.
Setup KLA to use Oauth2 SSO
After an account is configured to use SSO through OAuth2, this configuration becomes also available to KLA.
...
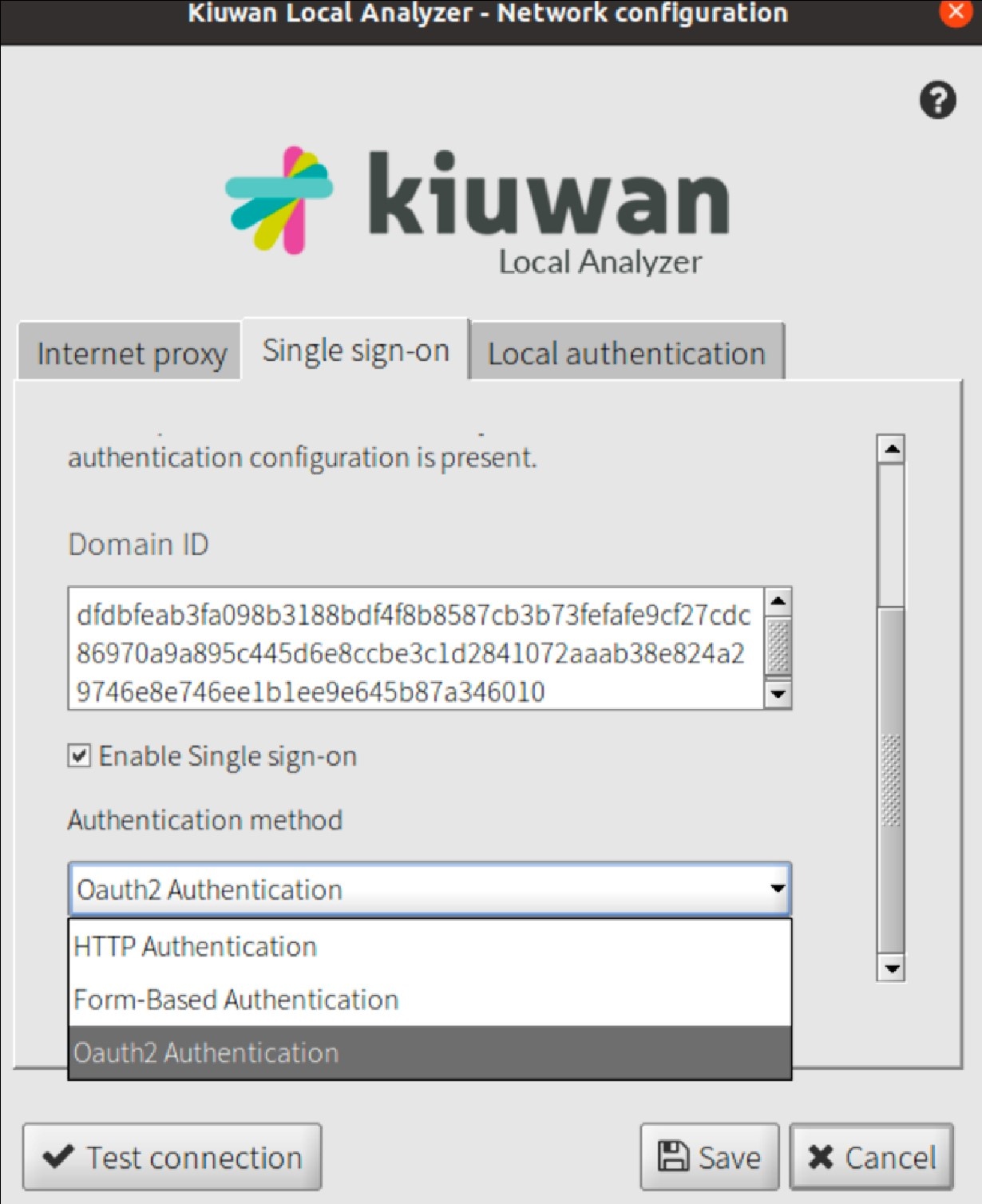
- Select the Advanced option.
- Enter the corresponding Domain ID, select the Enable SSO and the OAuth Authentication options from the pull-down list.
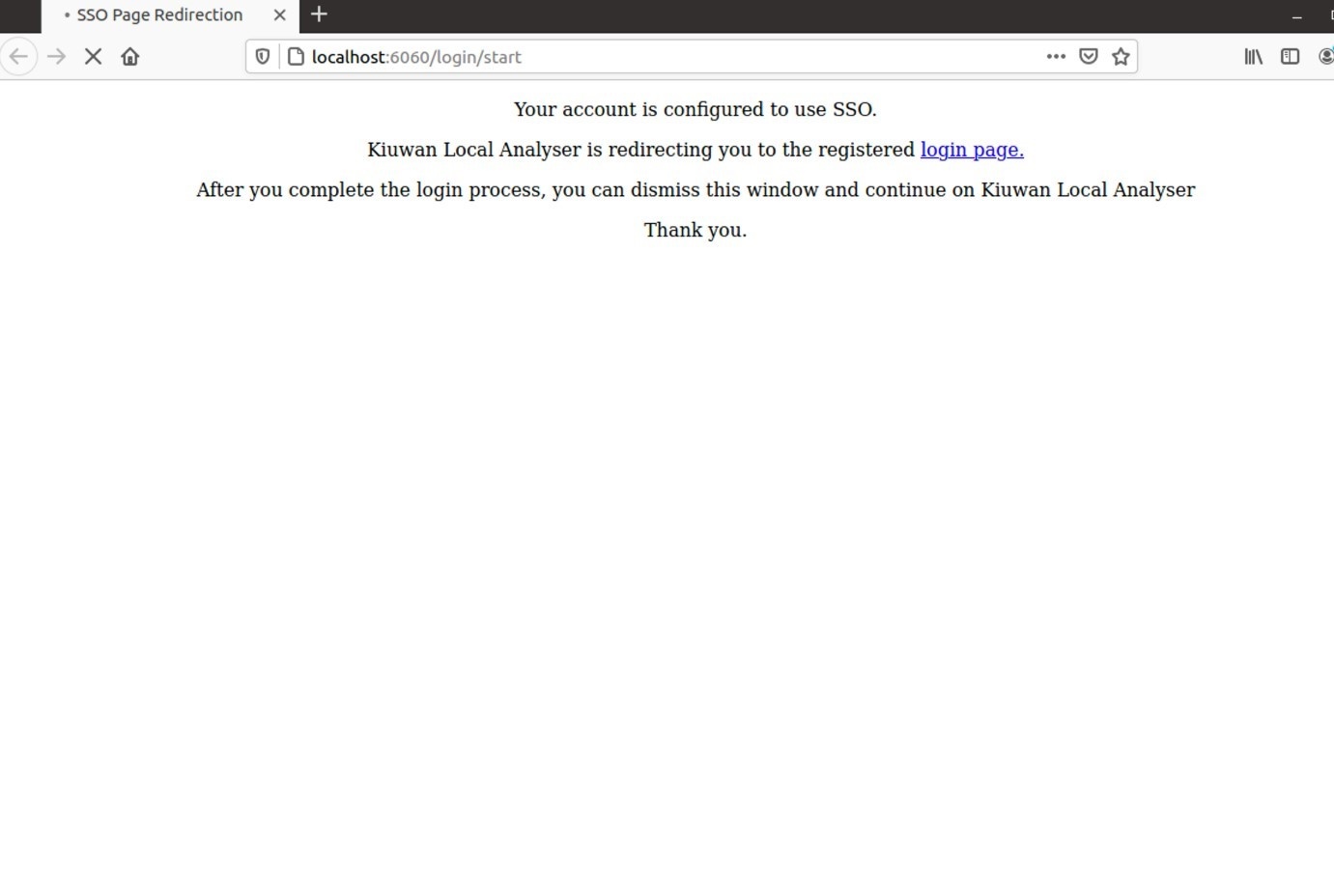
KLA is now configured to use the OAuth authentication as configured for that Kiuwan Account. Click Test Connection and KLA will redirect the authentication procedure to the native web browser:
The above page is temporarily presented informing the user that the login process is underway, and finally the regular authentication process for the configured Identity provided is initiated.
After the authentication process is completed, the browser window can be discarded as KLA has collected the needed information to proceed.
Login to KLA after OAuth SSO is activated
When KLA is configured to use SSO with OAuth, the Login form will show an indication that SSO is activated.
...