...
The following describes how to setup Kiuwan as a registered application on Azure ADFS, any other OAuth2.0/Open ID Provider with a similar configuration.
To enable the authentication through an OAuth/OIDC server when configuring Kiuwan as a client application is required to be obtained from OAuth Issuer the following:
...
- Start ADFS Management.
- Right-click the Application Groups folder from the left side of the window, and select Add Application Group.
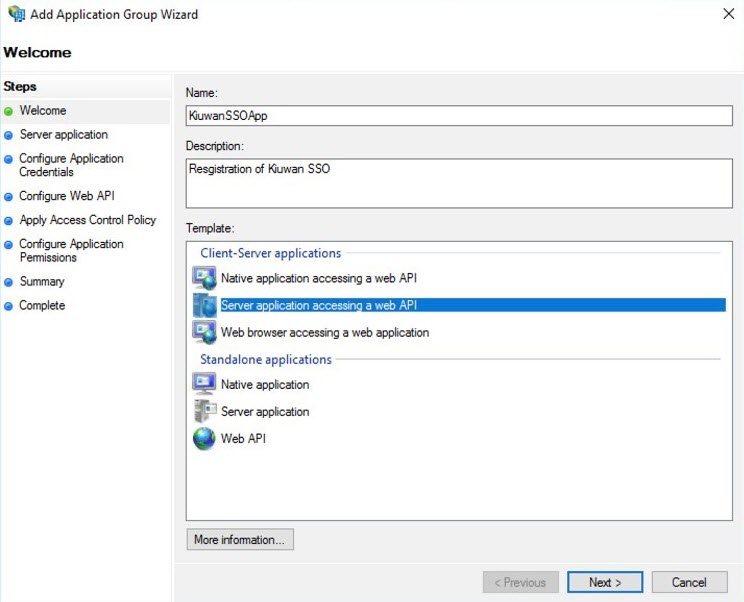
- Fill in the required Application Group Name, Description, select the option Server application accessing web API, and click Next.
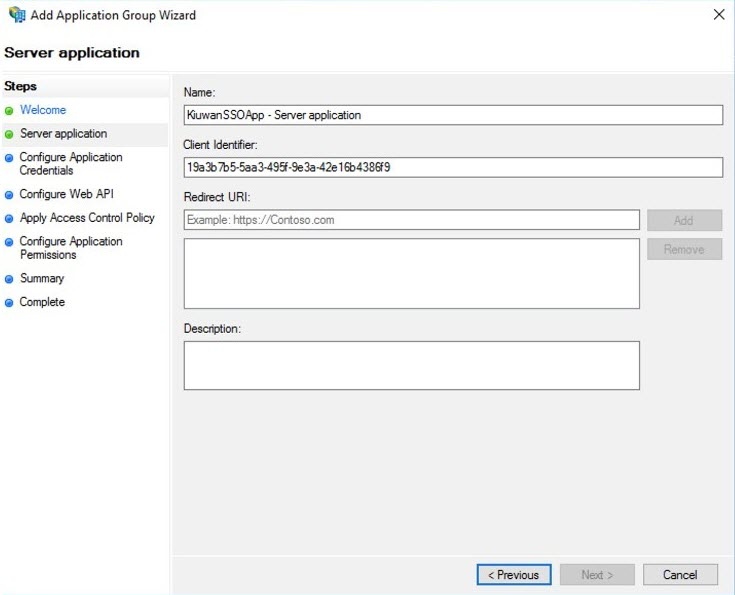
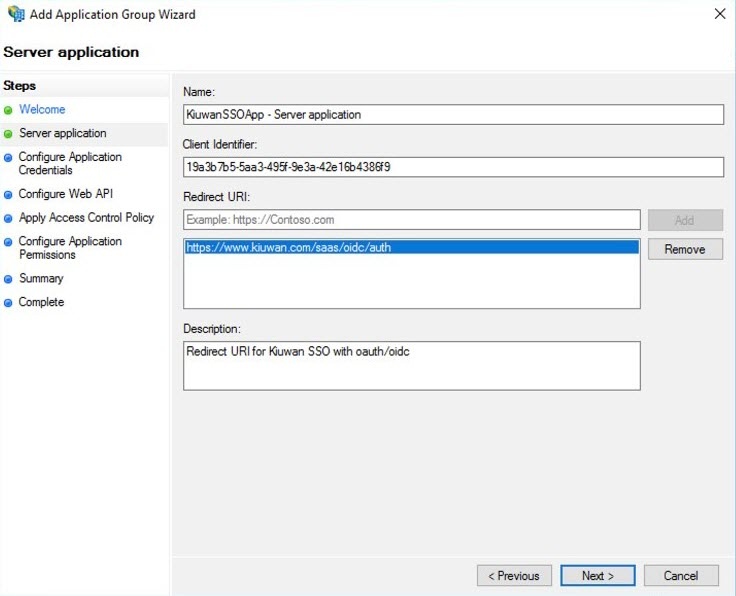
- Enter the Name of the Server Application and collect – and save in a temporary location the Client Identifier generated automatically. This information will be available for later consultation but can be copied now and pasted to the Kiuwan SSO configuration form as described in Setting up Kiuwan SSO with OAuth/Open ID Connect. Click Next.
- Next, add the Kiuwan Login entry point URI as a valid URI for redirection, e.g. https://www.kiuwan.com/saas/oidc/auth or the corresponding if you are using Kiuwan On-Premises or a custom installation instead of the standard Kiuwan cloud setup. Click Next.
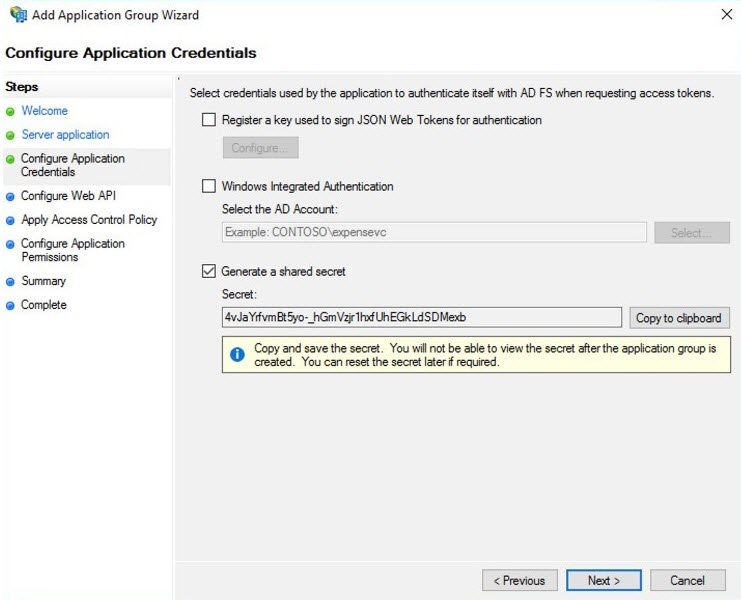
On the Configure Application Credentials tab, check the option Generate a shared secret, this will create the corresponding secret to be copied into the Kiuwan OAuth configuration panel, as described in Setting up Kiuwan SSO with OAuth/Open ID Connect. Click Next.
Tip Copy the generated the shared secret for a temporary location as it will not be available again, and if needed it will need to be regenerated.
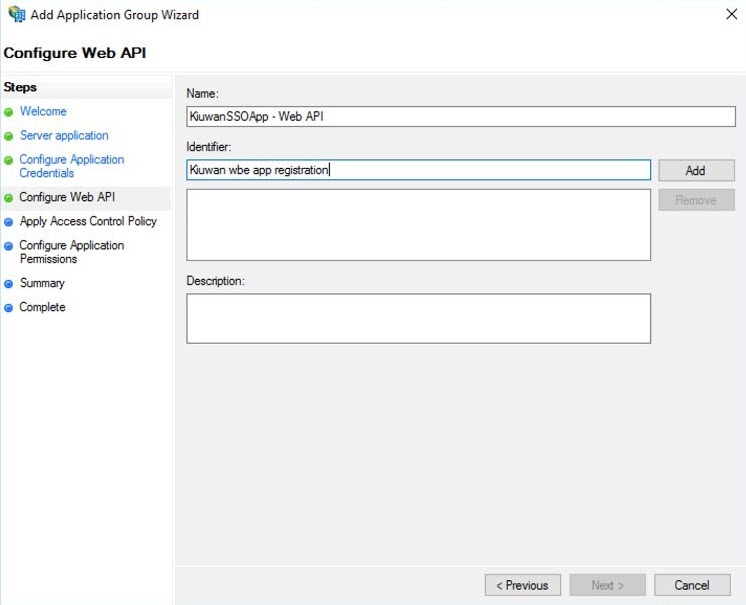
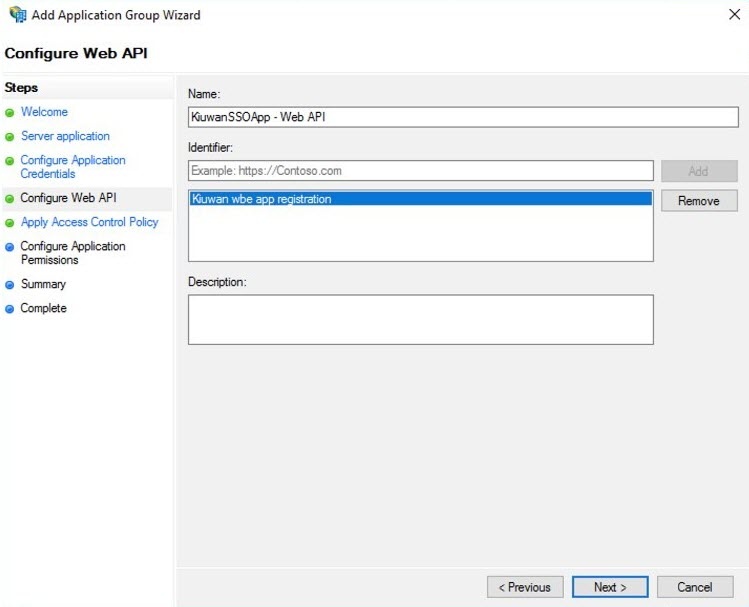
- Configure the Web API for ADFS by entering the name of the API and a description for the identifier of this Web API in ADFS. Click Next.
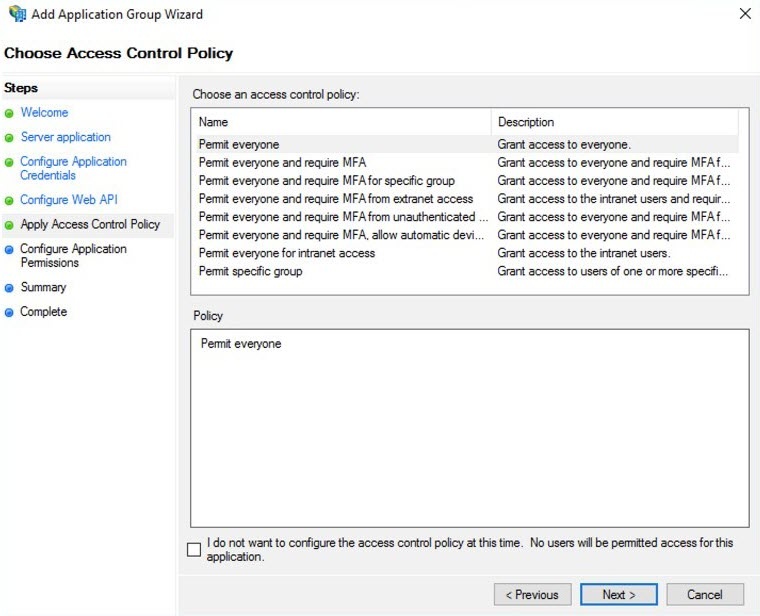
- Select the Permit Everyone option as a policy for Access Control and click Next.
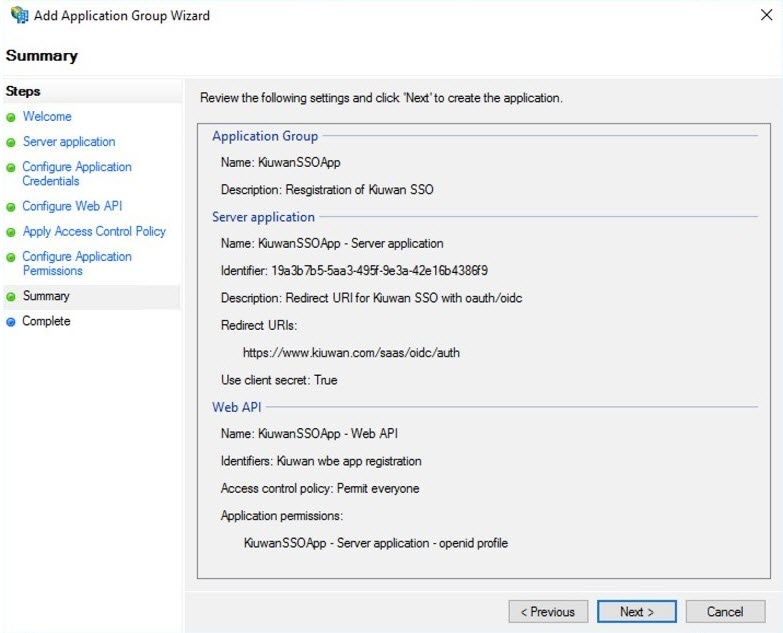
- Configure Application Permissions, select OpenID and Profile as Permitted scopes. If needed or desired additional scopes can be added to the list, this configures the available information about the authenticated user to be passed to Kiuwan.
If more information is required in Kiuwan to match the ADFS user with the Kiuwan user, it is allowed to select or even define new scopes. As minimal both OpenID (default) and profile scopes are needed by Kiuwan. Click next, to confirm the summary information. - Click Close to complete the process.
...
OKTA allows for additional configuration and provides extensive support, make sure you tailor the configuration to your needs.
| Anchor | ||||
|---|---|---|---|---|
|
To set up Kiuwan SSO with OAuth/OpenID connect follow these instructions:
...