The Code Security Tool Developers Trust
Kiuwan is a powerful, end-to-end application security platform. Our comprehensive toolset is designed to empower your team throughout the development process. With a combination of SAST, SCA, and QA, we help developers identify vulnerabilities in applications and remediate them rapidly.
Start scanning for vulnerabilities today.
Trusted by Developers Worldwide for 20 Years
Developers at the world’s leading brands rely on Kiuwan to ensure application security, keep important data safe, and accelerate time to market.
Why Kiuwan?
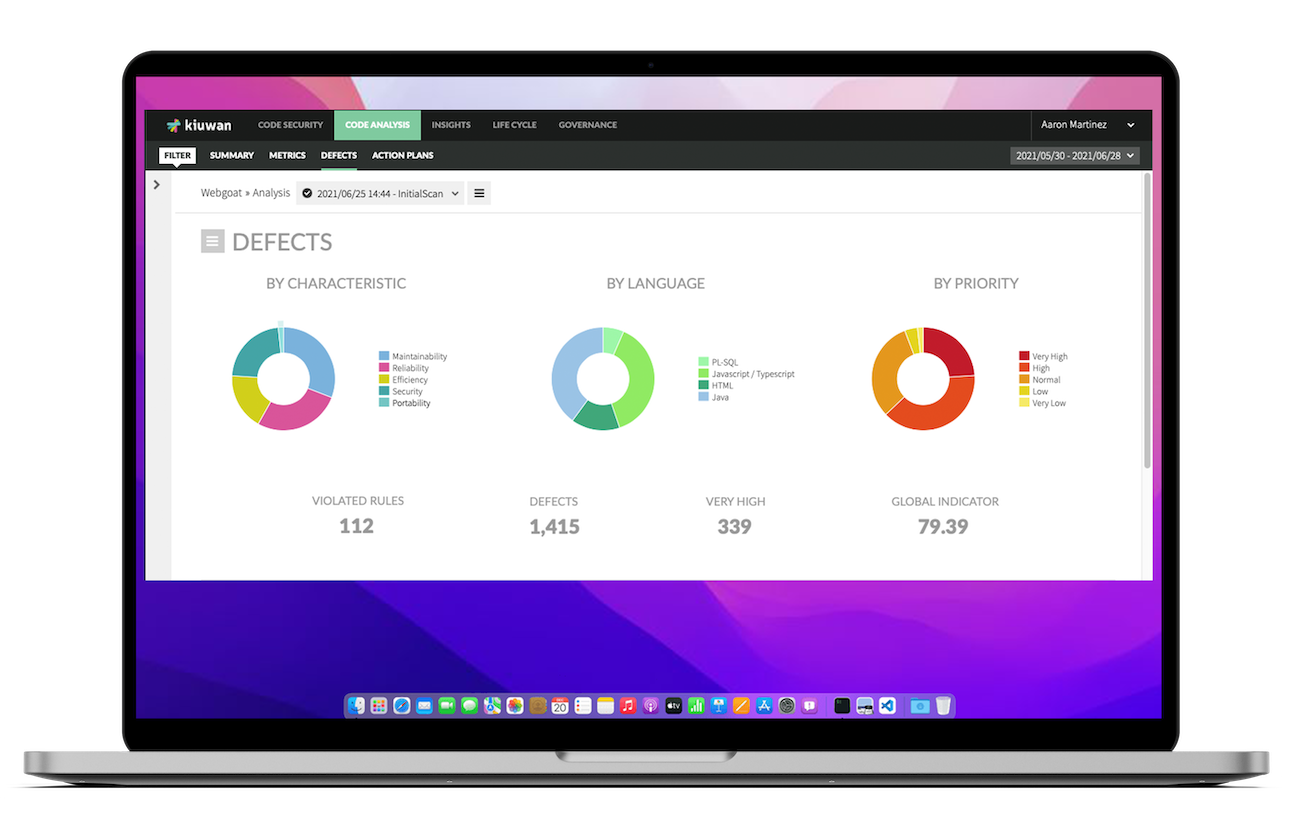
Kiuwan is the ultimate code security tool that all developers need. It detects security vulnerabilities in source code, enforces coding guidelines, and manages open-source components so developers can eliminate defects and improve application security.
Aligned with OWASP, CWE, CVE, CPE, and NIST security standards, developers and dev teams know they’re getting the ultimate protection.
Kiuwan supports 30+ major programming languages and frameworks. So whether the need is a WordPress vulnerability scanner, Python code analyzer, or other automated code review tool, Kiuwan has it covered.

The Benefits of Adding SAST to the SDLC
Kiuwan brings static application security testing (SAST) and software composition analysis (SCA) to the SLDC. Our source code vulnerability scanner is used by more Fortune 500 developers who need to meet industry-specific security regulations and internal security policies.
Integrates With Your Pipeline
Kiuwan works with all common programming languages and dev environments for easy integration directly into your existing development processes.

Develop a Security Process
Kiuwan uses industry standards to rate vulnerability severity and priority so that you get complete visibility over all the security risks that your applications face.

Improve Application Security
Kiuwan meets stringent industry requirements and market standards, so you can implement a rigorous approach to app security and deploy them with confidence.
Begin Scanning for Vulnerabilities Today
Products Kiuwan Offers
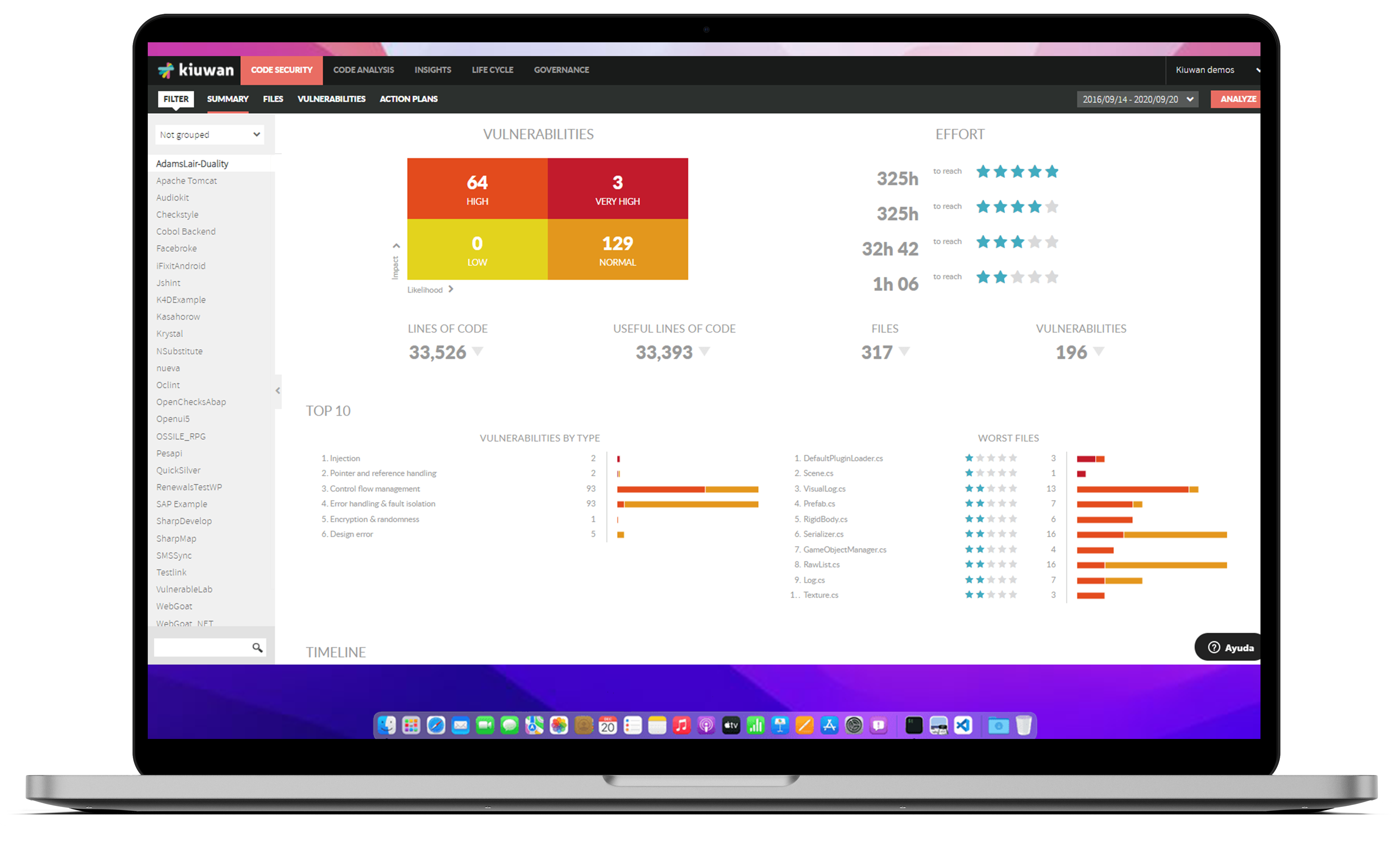
Code Security (SAST)
Kiuwan SAST is compliant with stringent security standards including CWE, OWASP, PCI, CERT, and SANS.
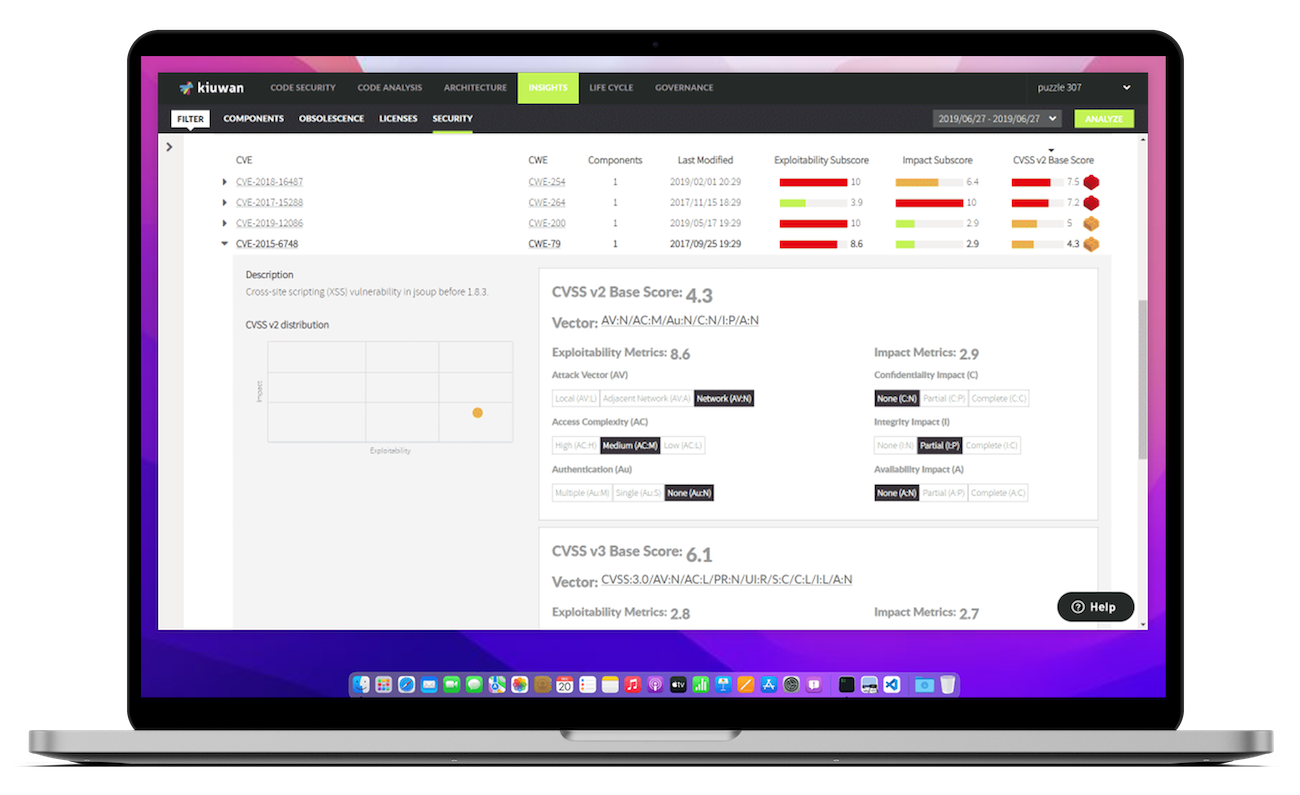
Insights (SCA)
Reduce risk from third-party components. Remediate vulnerabilities and ensure license compliance.
Code Analysis & Governance
Fast code analysis in a cloud environment for security QA/engineers and IT teams.

Ready to Start Scanning for Vulnerabilities?
Get the complete set of Idera DevOps tools:

App Shielding & Hardening

UI Test Automation

Targeted Automated Testing